The Voice of Cyber®
News & Thoughts
Stay up-to-date on the news with press releases from some of the biggest organisations and deep-dive articles from leaders within the industry.
Deep Dive Articles

MyCISO Launches in Style
Thursday, 18th August, I was the MC of the MyCISO Launch event hosted at the stunning ‘Shell House’ in Sydney, Australia. The team has been working on the development of the MyCISO product for a number of years, so the launch was a huge milestone for them.
The launch opened with guest speaker, Jan Schreuder, Co-Founder of the Cyber Leadership ...
Security Fatigue: How Public Agencies Can Counter this Silent Menace
Every one of us knows one person or colleague who has a Post-it® Note full of passwords stuck to their monitor. Pre-pandemic, this is a one-in-ten case of security malpractice. But with how rapidly organisations have adopted digital solutions for remote work in the past two years, I’m willing to bet remote workers have passwords written down everywhere ...

What I’ve Learnt as an Entrepreneur
A few things I’ve learnt over the years of being an Entrepreneur. This changes for me all the time, our challenges become easier to tackle and what scares us varies. Ultimately, you learn so much, and I wanted to share what I’ve learnt so far.

What I’ve Learnt as an Entrepreneur
A few things I’ve learnt over the years of being an Entrepreneur. This changes for me all the time, our challenges become easier to tackle and what scares us varies. Ultimately, you learn so much, and I wanted to share what I’ve learnt so far.

Australian Public: How to add 2FA
Two-Factor Authentication (2FA) is a necessity to ensure your daily security, no matter who you are. It can protect your social media accounts, banking accounts, email, or just about any other online service from being hacked. “How?” you ask. Well, let’s take a closer look at how it works and how to get it working fast. To keep your online identity as ...

Privacy Has a Business Model Problem
Business growth should not come at the expense of customer privacy. Unfortunately, that’s not a belief that everybody holds, and the result is an environment in which data privacy breaches are increasing in regularity and severity. Whether it’s Facebook, Cambridge Analytica and The US Elections, or any of the nearly 1,000 incidents received by Office ...
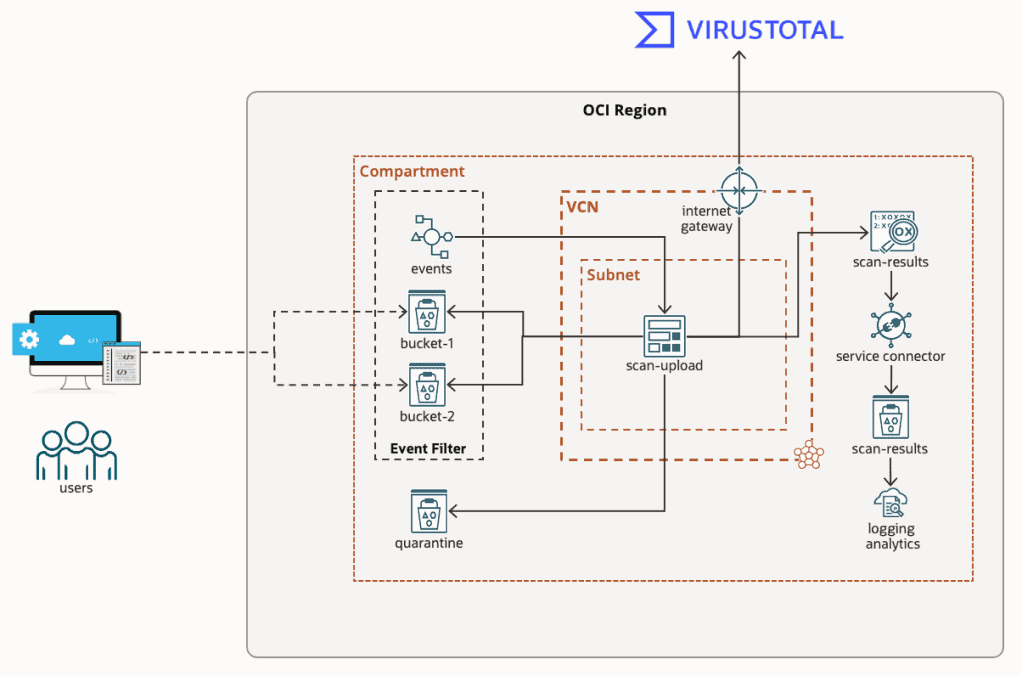
Virus & Malware Scanning Object Storage in OCI
If you’re like me, then working in IT means you also assume Tech Support duties for friends, family, and those distant relatives that only seem to call when they’ve got a problem.
I just clicked on this link, and my computer is doing something weird. I think my PC has a virus, what do I do?
When it’s just a single computer, the answer is simple, ...

Tenable Research Reveals “Do-It-Yourself” Ransomware Kits Have Created Thriving Cottage Industry of Cybercrime
The self-sustaining ransomware industry earned $692m from collective attacks in 2020 The shift to the subscription economy has created a new norm in the as-a-service world. And it’s not just Netflix and Spotify that have adopted this business model. New research from Tenable®, the Cyber Exposure company, found that one of the main reasons ransomware ...
No results found.
In The News
Kyndryl Survey, Conducted With AWS, Reveals Cybersecurity Readiness Gap In Australian And New Zealand Enterprises
Survey of enterprises in Australia and New Zealand confirms disconnect between cyber preparedness and readiness Urgent need for improved awareness and cyber resilience strategies amid rising threats
Fortinet Continues to Expand Generative AI Across Its Portfolio With Two New Additions To Simplify Security Operations
FortiAI now spans seven unique Fortinet products with new generative AI integrations for FortiNDR Cloud to accelerate threat coverage analysis and Lacework FortiCNAPP to streamline investigation
Quadrant’s Security Operations Center Experts Receive 2024 SOC Analyst Appreciation Awards
Quadrant congratulates Charles Goggins, Joshua Hall, and Joshua Hubner for their exceptional achievements and dedication to advancing cybersecurity within the SOC. Their recognition highlights Quadrant's commitment to fostering talent and enhancing cybersecurity resilience.
WatchGuard Earns Top Awards from TrustRadius for Network and Endpoint Security, and Multi-Factor Authentication
TrustRadius accolades across product categories add to broad recognition for WatchGuard’s comprehensive cybersecurity platform
Elastic Enables Innovation in Next Generation Knowledge Management with LG CNS
Elasticsearch enhances LG CNS’s KeyLook AI with hybrid search, achieving a 95% increase in search relevance to dramatically improve the accessibility and usability of corporate knowledge

2020Partners Kicks Off Dialogue In Australia
Sydney, Australia – 2020Partners kicks off its inaugural Advanced Technology Dialogue in Sydney and Canberra, with support from the Australian Strategic Policy Institute (ASPI) and our media partner, KBI.Media. This initiative aims to facilitate greater connections between Australia, United Kingdom and the United States on mission critical technology ...
CrowdStrike to Acquire Adaptive Shield to Deliver the Only Platform that Unifies Cloud and Identity Security with Integrated SaaS Protection
Falcon platform will deliver complete protection against identity-based attacks across hybrid cloud environments, from on-prem AD to cloud-based identity providers and SaaS apps
Proofpoint Signs Definitive Agreement to Acquire Normalyze
Acquisition of leading DSPM company will bolster Proofpoint’s human-centric security platform aiming to address the full spectrum of data security challenges across today’s complex data landscape
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
- 191
- 192
- 193
- 194
- 195
- 196
- 197
- 198
- 199
- 200
- 201
- 202
- 203
- 204
- 205
- 206
- 207
- 208
- 209
- 210
- 211
- 212
- 213
- 214
- 215
- 216
- 217
- 218
- 219
- 220
- 221
- 222
- 223
- 224
- 225
- 226
- 227
- 228
- 229
- 230
- 231
- 232
- 233
- 234
- 235
- 236
No results found.
What We Do
KBI.Media is The Voice of Cyber.
We broadcast some of the most important and informative cyber content from some of the largest organisations, governments, and promising start-ups from around the world.
We're also responsible for creating a lot of it..
