The Voice of Cyber®
News & Thoughts
Stay up-to-date on the news with press releases from some of the biggest organisations and deep-dive articles from leaders within the industry.
Deep Dive Articles
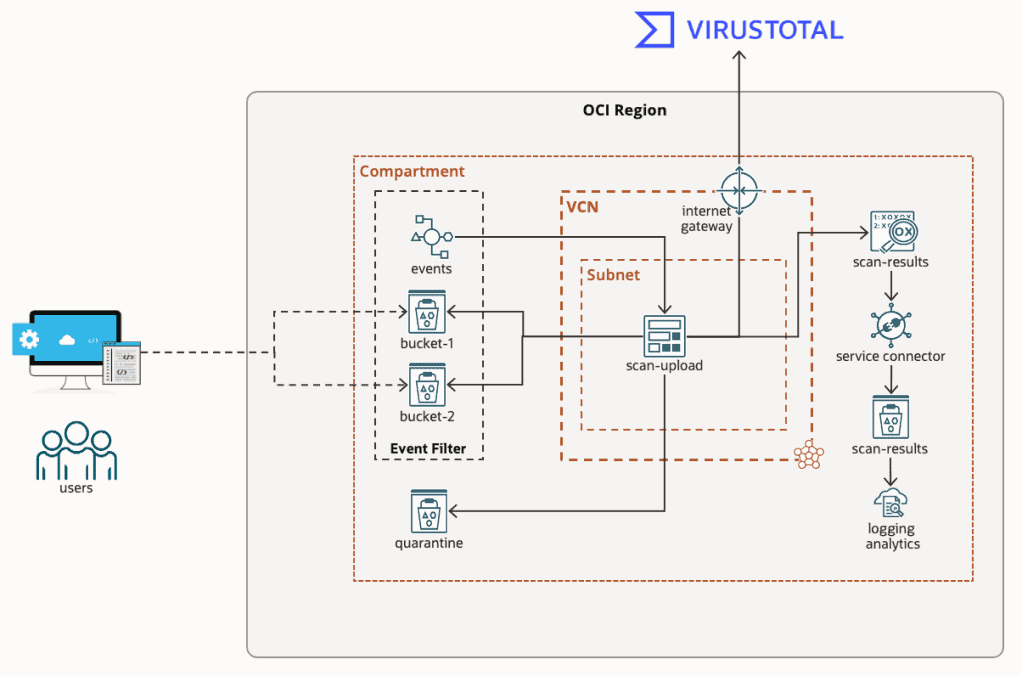
Virus & Malware Scanning Object Storage in OCI
If you’re like me, then working in IT means you also assume Tech Support duties for friends, family, and those distant relatives that only seem to call when they’ve got a problem.
I just clicked on this link, and my computer is doing something weird. I think my PC has a virus, what do I do?
When it’s just a single computer, the answer is simple, ...

Tenable Research Reveals “Do-It-Yourself” Ransomware Kits Have Created Thriving Cottage Industry of Cybercrime
The self-sustaining ransomware industry earned $692m from collective attacks in 2020 The shift to the subscription economy has created a new norm in the as-a-service world. And it’s not just Netflix and Spotify that have adopted this business model. New research from Tenable®, the Cyber Exposure company, found that one of the main reasons ransomware ...

Tenable Research Reveals “Do-It-Yourself” Ransomware Kits Have Created Thriving Cottage Industry of Cybercrime
The self-sustaining ransomware industry earned $692m from collective attacks in 2020 The shift to the subscription economy has created a new norm in the as-a-service world. And it’s not just Netflix and Spotify that have adopted this business model. New research from Tenable®, the Cyber Exposure company, found that one of the main reasons ransomware ...

Darktrace – Media Roundtable | Event Report
I was recently invited to a Roundtable Media Event held by Darktrace to unpack the new era of cyber security threats. Held on Thursday 16th June, it was led by Tony Jarvis, Director of Enterprise Security and Dave Palmer, Chief Product Officer.
The following is a synopsis of the event and a deeper dive into what was covered.
Most Significant ...
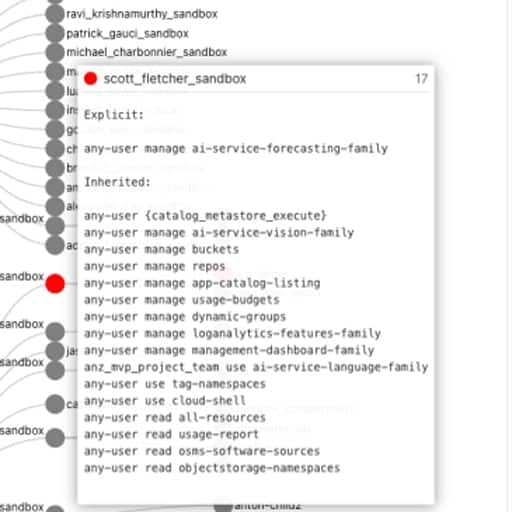
OCI User Access Review Made Easy
I’m sure we can all agree, adopting a cloud strategy is awesome. The opportunities and benefits it affords are many. However cloud governance is an ongoing problem that plagues security, compliance, and management teams, which cloud vendors like Oracle are continually trying to solve.
If you’re reading this, you’ve probably been asked, or heard at ...

Media Alert: Scammers Hack Twitter Accounts to Steal Popular NFTs and Digital Currencies
According to recent research, published by Tenable’s Staff Research Engineer, Satnam Narang, scammers have once again dug deep into their bag of tricks to capitalise on the fervour in non-fungible tokens (NFT) and cryptocurrencies.
Many are hijacking verified and unverified accounts on Twitter to impersonate popular NFT projects including Bored Ape ...

Why Renewal of Your Privacy Practice is Critical
It is without doubt that the COVID-19 pandemic forced some of the most significant changes in society, business and workforce practices in the last century. With billions of consumers and workers driven online, businesses adapted and accelerated their digital strategies. As staff worked remotely and scammers capitalised on the explosion of e-commerce, ...

Communication for Internal Teams On the Importance of Understanding Risk
If all communication was abolished, society would crumble. Fast. Yet one area that I have noticed in the security industry, which I believe needs a lot more attention - and often goes unmentioned - is how we communicate internally to our teams on the importance of understanding risk in the face of change.
Through my work, I’ve lately had a huge volume ...
In The News
Cado Security Announces New Integration with CrowdStrike to Accelerate Forensics and Incident Response
New integration with the CrowdStrike Falcon platform helps to automate investigations and perform root cause analysis
SolarWinds Unveils Transformative Enhancements to Observability Solutions
SYDNEY, Australia – February 8, 2024 – SolarWinds (NYSE:SWI), a leading provider of simple, powerful, secure observability and IT management software, today announced enhancements to its SaaS-based and self-hosted, on-premises observability solutions built to monitor and observe complex, distributed environments from anywhere. The AI-powered ...
SailPoint Introduces Two New Offerings: Identity Security Cloud Standard Suite and Customer Success Portfolio Packages
New solutions arm customers for success throughout their journey with offerings that match program maturity and business scale
Qualys Unveils TotalCloud 2.0 with TruRisk Insights to Measure, Communicate, and Eliminate Cyber Risk in Cloud and SaaS Applications
Expanded solution brings cloud infrastructure, SaaS apps and externally exposed assets together for a unified view of risk across multi-cloud environments
Motorola Solutions Joins Forces with Google Cloud to Advance Safety and Security
Motorola Solutions and Google Cloud today announced a strategic, multi-year agreement that will focus on innovating cloud solutions across Motorola Solutions’ safety and security technologies. With Google Cloud’s infrastructure, Motorola Solutions will prioritise the advancement of assistive intelligence, including highly accurate and reliable video ...
F5 Transforms Application Security for the AI Era
New end-to-end API security and AI capabilities make it easier for customers to protect their AI-powered applications

Trend Micro Appoints Srujan Talakokkula as New ANZ Commercial Managing Director
Trend Micro bolsters ANZ leadership team to reinforce its commitment to local customers and partners
Check Point Software Technologies Triumphs in Miercom’s 2024 Next Generation Firewall Benchmark Report
Check Point demonstrated a block rate of 99.8% on new malware, a flawless 100% phishing prevention rate, and an industry-leading lowest False Positive Detection rate of 0.13%
What We Do
KBI.Media is The Voice of Cyber.
We broadcast some of the most important and informative cyber content from some of the largest organisations, governments, and promising start-ups from around the world.
We're also responsible for creating a lot of it..
