The Voice of Cyber®
News & Thoughts
Stay up-to-date on the news with press releases from some of the biggest organisations and deep-dive articles from leaders within the industry.
Deep Dive Articles

Privacy Has a Business Model Problem
Business growth should not come at the expense of customer privacy. Unfortunately, that’s not a belief that everybody holds, and the result is an environment in which data privacy breaches are increasing in regularity and severity. Whether it’s Facebook, Cambridge Analytica and The US Elections, or any of the nearly 1,000 incidents received by Office ...
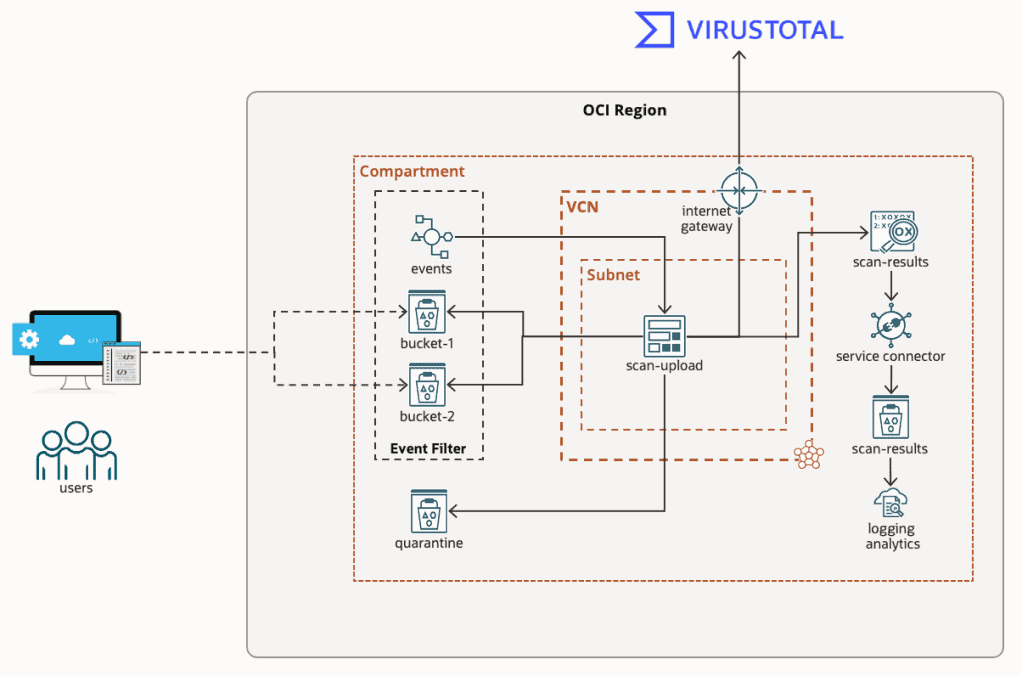
Virus & Malware Scanning Object Storage in OCI
If you’re like me, then working in IT means you also assume Tech Support duties for friends, family, and those distant relatives that only seem to call when they’ve got a problem.
I just clicked on this link, and my computer is doing something weird. I think my PC has a virus, what do I do?
When it’s just a single computer, the answer is simple, ...
Tenable Research Reveals “Do-It-Yourself” Ransomware Kits Have Created Thriving Cottage Industry of Cybercrime
The self-sustaining ransomware industry earned $692m from collective attacks in 2020 The shift to the subscription economy has created a new norm in the as-a-service world. And it’s not just Netflix and Spotify that have adopted this business model. New research from Tenable®, the Cyber Exposure company, found that one of the main reasons ransomware ...
Tenable Research Reveals “Do-It-Yourself” Ransomware Kits Have Created Thriving Cottage Industry of Cybercrime
The self-sustaining ransomware industry earned $692m from collective attacks in 2020 The shift to the subscription economy has created a new norm in the as-a-service world. And it’s not just Netflix and Spotify that have adopted this business model. New research from Tenable®, the Cyber Exposure company, found that one of the main reasons ransomware ...

Darktrace – Media Roundtable | Event Report
I was recently invited to a Roundtable Media Event held by Darktrace to unpack the new era of cyber security threats. Held on Thursday 16th June, it was led by Tony Jarvis, Director of Enterprise Security and Dave Palmer, Chief Product Officer.
The following is a synopsis of the event and a deeper dive into what was covered.
Most Significant ...
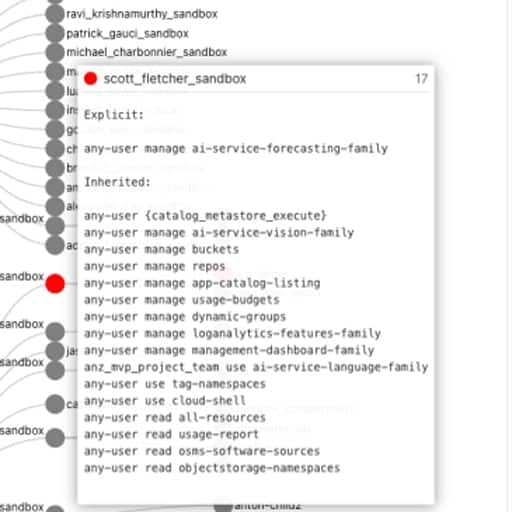
OCI User Access Review Made Easy
I’m sure we can all agree, adopting a cloud strategy is awesome. The opportunities and benefits it affords are many. However cloud governance is an ongoing problem that plagues security, compliance, and management teams, which cloud vendors like Oracle are continually trying to solve.
If you’re reading this, you’ve probably been asked, or heard at ...
Media Alert: Scammers Hack Twitter Accounts to Steal Popular NFTs and Digital Currencies
According to recent research, published by Tenable’s Staff Research Engineer, Satnam Narang, scammers have once again dug deep into their bag of tricks to capitalise on the fervour in non-fungible tokens (NFT) and cryptocurrencies.
Many are hijacking verified and unverified accounts on Twitter to impersonate popular NFT projects including Bored Ape ...

Why Renewal of Your Privacy Practice is Critical
It is without doubt that the COVID-19 pandemic forced some of the most significant changes in society, business and workforce practices in the last century. With billions of consumers and workers driven online, businesses adapted and accelerated their digital strategies. As staff worked remotely and scammers capitalised on the explosion of e-commerce, ...
No results found.
In The News

New Akamai Study Reveals API Security Incidents Cost APAC Enterprises Over US$580,000 on Average in the Past Year
Internal disconnects, poor visibility, and misaligned priorities leave organisations vulnerable to costly API security incidents
Barracuda Networks Welcomes Dan Mclean as Country Manager for ANZ
Barracuda Networks Welcomes Dan McLean as Country Manager for ANZ - New Leader to Drive Growth and Partner Success
Delinea Unveils Enterprise-Grade Cloud-Native Security Capabilities to Help Safeguard and Scale AI Innovation
New and planned enhancements to Machine and AI solution on the Delinea Platform provide guardrails for organisations to secure the use of AI and secure with AI without compromising compliance or productivity.
Genetec Announces Alignment With ACSC’s Essential Eight Cybersecurity Framework
SYDNEY, May 6, 2025—Genetec Inc. (“Genetec”), the global leader in enterprise physical security software, today announced it has been assessed to align with the Australian Cyber Security Centre’s (ACSC) Essential Eight threat mitigation requirements, as verified by CyberCX.
Developed in partnership with the Australian Government, the ACSC’s ...
CyberArk Named an Overall Leader in the KuppingerCole Analysts 2025 Leadership Compass for Enterprise Secrets Management
Recognition underscores CyberArk’s market leadership in Machine Identity Security

Akamai Firewall for AI Enables Secure AI Applications with Advanced Threat Protection
Akamai’s latest solutions use AI to strengthen security while also protecting businesses from AI-driven threats
Excite Announces $2.8 Million Capital Raise To Accelerate Growth In Cyber Security And Training Initiatives
Excite Managing Director and CEO, Mr Bryan Saba, commented: "The funds will enhance our core capabilities in digital forensics, cyber training, and offensive security whilst directly supporting revenue-generating opportunities already in play. We're building momentum across defence, government and critical infrastructure sectors, and this investment ...
Tenable Research Shows How “Prompt-Injection-Style” Hacks Can Secure the Model Context Protocol (MCP)
Tenable Research has published new findings that flip the script on one of the most discussed AI attack vectors. In the blog “MCP Prompt Injection: Not Just for Evil,” Tenable’s Ben Smith demonstrates how techniques resembling prompt injection can be repurposed to audit, log and even firewall Large Language Model (LLM) tool calls running over the ...
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
- 191
- 192
- 193
- 194
- 195
- 196
- 197
- 198
- 199
- 200
- 201
- 202
- 203
- 204
- 205
- 206
- 207
- 208
- 209
- 210
- 211
- 212
- 213
- 214
- 215
- 216
- 217
- 218
- 219
- 220
- 221
- 222
- 223
- 224
- 225
- 226
- 227
- 228
- 229
- 230
- 231
- 232
- 233
- 234
- 235
- 236
- 237
- 238
- 239
- 240
- 241
- 242
- 243
- 244
- 245
- 246
- 247
- 248
- 249
- 250
- 251
- 252
- 253
- 254
- 255
- 256
- 257
- 258
- 259
- 260
- 261
- 262
- 263
- 264
- 265
- 266
- 267
- 268
- 269
- 270
- 271
- 272
- 273
- 274
- 275
- 276
- 277
- 278
- 279
- 280
- 281
- 282
- 283
- 284
- 285
- 286
- 287
- 288
- 289
- 290
- 291
- 292
- 293
- 294
- 295
- 296
- 297
- 298
- 299
- 300
- 301
- 302
- 303
- 304
- 305
- 306
- 307
- 308
- 309
- 310
- 311
- 312
- 313
- 314
- 315
- 316
- 317
- 318
- 319
- 320
- 321
No results found.
What We Do
KBI.Media is The Voice of Cyber.
We broadcast some of the most important and informative cyber content from some of the largest organisations, governments, and promising start-ups from around the world.
We're also responsible for creating a lot of it..
