As the latest phishing techniques are more sophisticated than ever before, general anti-phishing tips cannot safeguard you from becoming a victim. High-quality emails, confusing branding of domain names and poor user interfaces all play right into the hands of the cybercriminals. In the following article, we will showcase a range of real-world phishing emails caught by our anti-phishing technology, which would have otherwise ended up in our clients’ inboxes.
This is Part 2 of a two-part article. In our previous article, we reviewed what the commonly cited anti-phishing tips were and how they have failed to protect us from phishing.
Not Every Spelling Error Is Silly
Our first example is an email mimicking legitimate account notifications from PayPal. The spelling of certain words looks ridiculous first because the words ‘PayPal’ and ‘limitation’ are written with a capital ‘I’ (for Idaho).
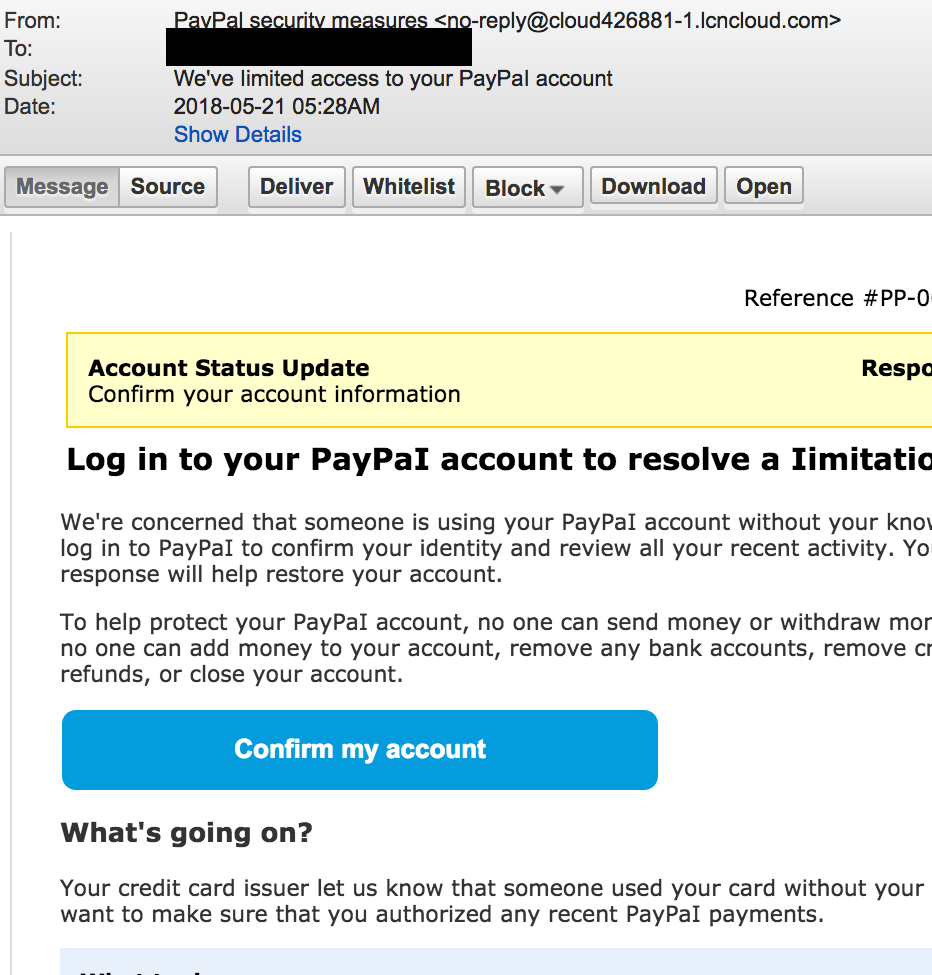
Any recipient of these fake emails would probably have spotted the spelling mistakes and never clicked on the ‘Confirm my account’ button – which would take the victim to a fake PayPal login page. Clearly, real emails from PayPal would never feature such spelling mistakes.
However, if we open the same email on in a different email client, the misspelled words suddenly disappear. The look of the uppercase ‘I’ (Idaho) is similar to the letter ‘l’ (Lima) thus, correctly spelling the word ‘PayPal’.
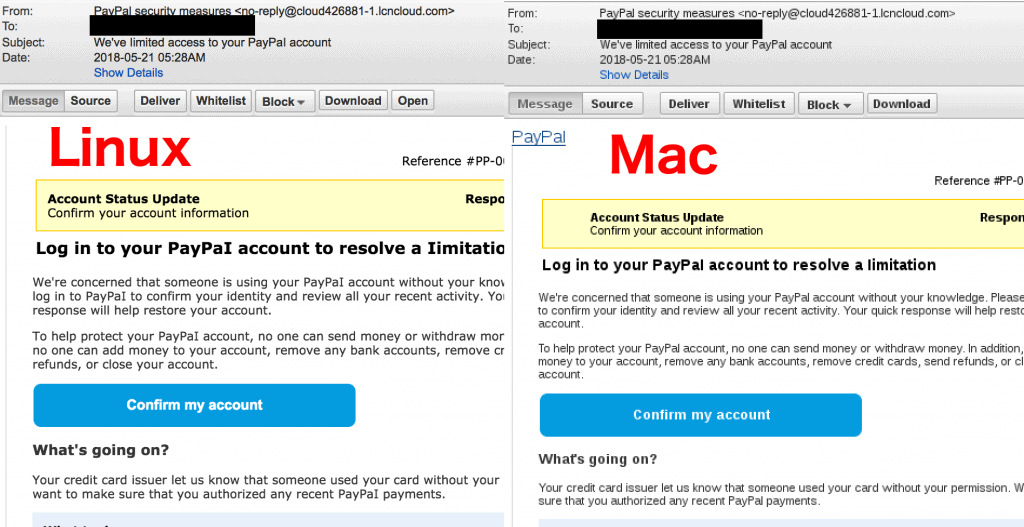
A different font style renders the correct spelling of the word ‘PayPal’
The reason for this unusual behaviour is that the email client on the right is using a sans-serif fonts style to display the email. Hackers rely on this technique because clever misspellings like this are used to evade basic spam filters.
The takeaway here is that spelling mistakes are not necessarily unintentional because of the attacker’s poor English skills. Spelling ‘mistakes’ are often invisible to the naked eye and done intentionally for malicious purposes.
Poor Grammar Is an Issue of the Past
Another indicator of a phishing email – according to the usual round of top-tips – is grammatical mistakes. This statement may have been true a decade ago when cybercriminals with English as a second language had no help with writing deceptive emails.
Since then the sophistication of cybercriminals has improved, and so have the resources at their disposal to write better quality phishing emails. Cybercriminals can use third-party services to proofread their emails to get the grammar right, or in what has become a common practice in phishing, attackers will clone common email notifications of well-known brands and businesses.
The Attack of the Clone Emails
Australian brands, like Australia Post, Commonwealth Bank, ASIC and Woolworths, are frequently abused by cybercriminals. The phishing emails impersonating these brands are usually pixel-perfect copies of legitimate notification emails, such as package delivery notifications or online banking notifications. The wording, spelling and look and feel are genuine enough to pass the age-old ‘poor English’ test.
At first sight, the following email bill appears to be from Origin Energy. It has the same look and feel of actual Origin emails apart from the embedded hyperlink – which is pointing to a malware-infected file instead.
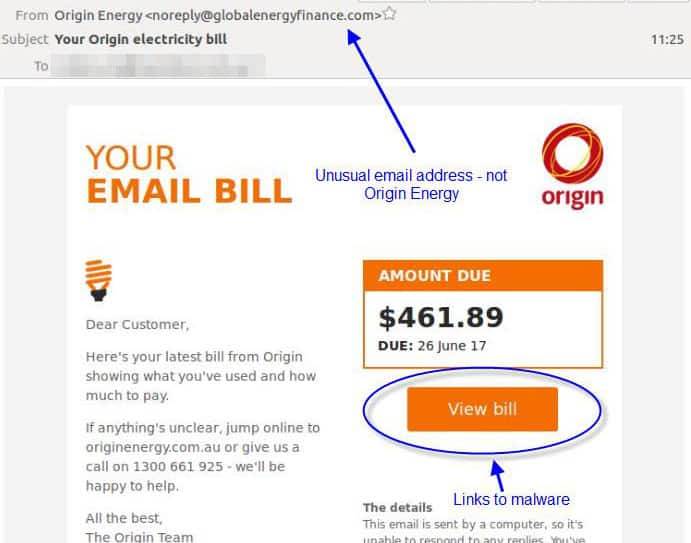
A perfect clone of the Origin Energy bill notifications (Source: MailGuard)
Proofreading Is Within Arm’s Reach
The other reason why poor grammar is no longer an issue for cybercriminals without a good command of English is that online professional proofreading services are readily accessible and cheap. Services like Fiverr can connect cybercriminals with native English speakers who are keen on proofreading any text for as low as A$6.

Low-cost proofreading service on Fiverr
Cybercriminals with poor English can also rely on machine learning-assisted spelling and grammar tools like Grammarly or Hemingway Editor, which are more advanced compared to traditional spell checker and grammar tools. They can help even the most clumsy writer create grammatically correct and correctly spelled emails. These advanced tools check for punctuation, grammar, context, and sentence structure to produce better-quality texts.
Confusing Domains are Confusing
Phishing emails frequently contain hyperlinks which take their victims to fake login pages or other webpages riddled with malicious software. The standard advice is to hover over a link before clicking on it, so that you can check where the hyperlink will take you. The process should be simple: if the email comes from PayPal, both the email sender and the web link should be PayPal.com (or a country-specific variant), right?
Wrong. Sadly, many companies tend to register confusing domain variants of their brands. For example, [email protected] is a legitimate email address belonging to the PayPal Merchant Tech Support team.
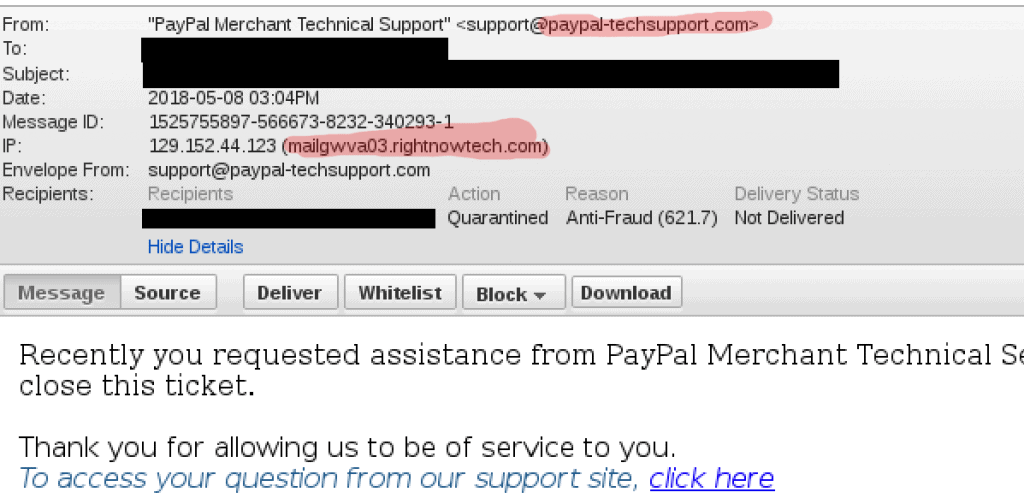
Despite of the sender details, this email was sent by PayPal
The web link in the email points to epl.paypal-communication.com, and it took us several minutes to confirm that the web link is indeed legitimate. Brand name domain variations not only confuse customers but also other security researchers, and even the PayPal’s own security team. For instance, paypal-knowledge.com and paypal-community.com are also legitimate domains used by PayPal.
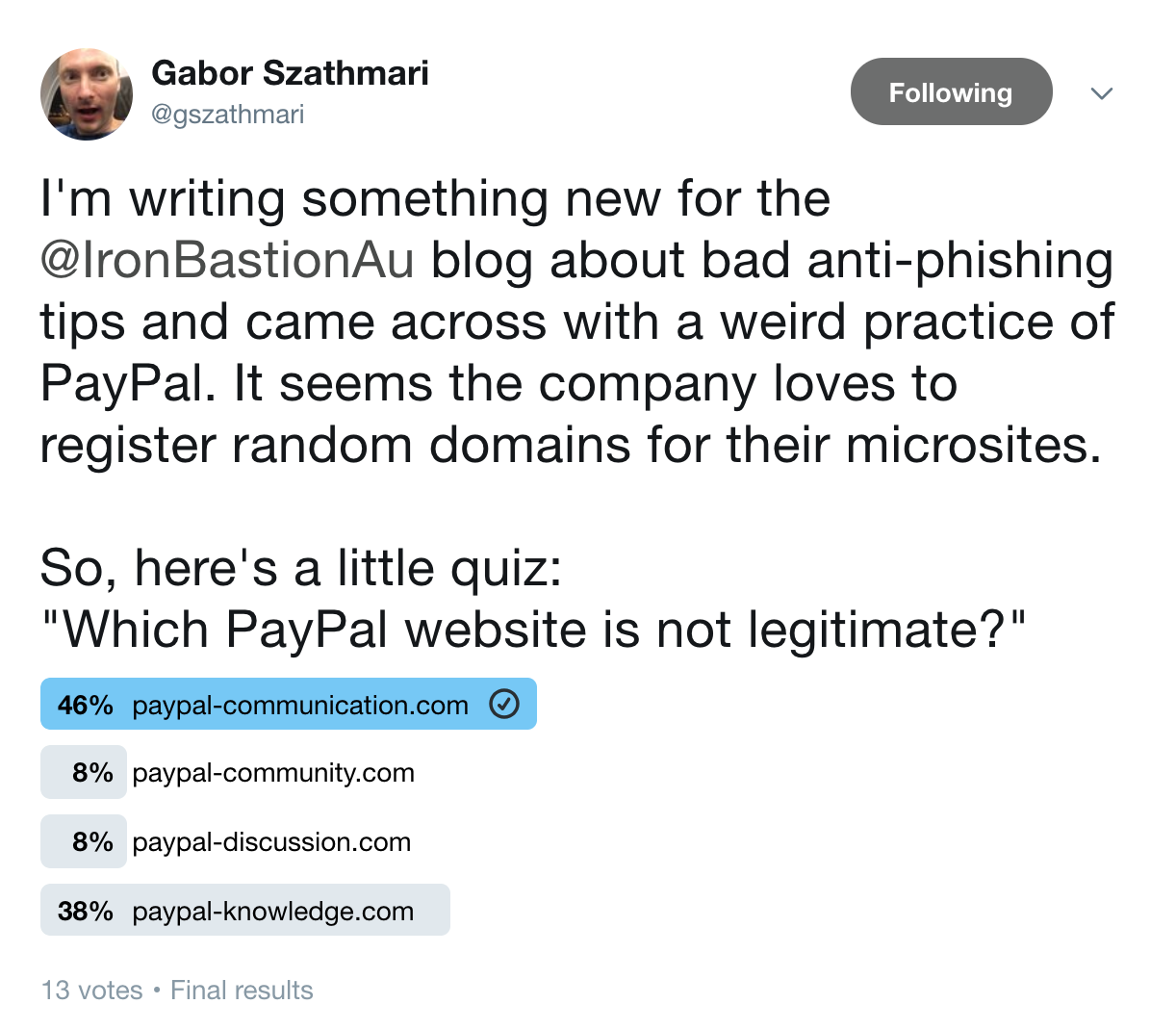
Out of curiosity, we ran a Twitter poll to see if other people would have trouble identifying a faux PayPal domain. We asked our followers to pick the fake PayPal domain from three other legitimate ones. Sadly, the majority of the responders could not recognise that paypal-discussion.com was a fraudulent domain not run by PayPal. How can we expect anyone to recognise a legitimate domain name before clicking then?
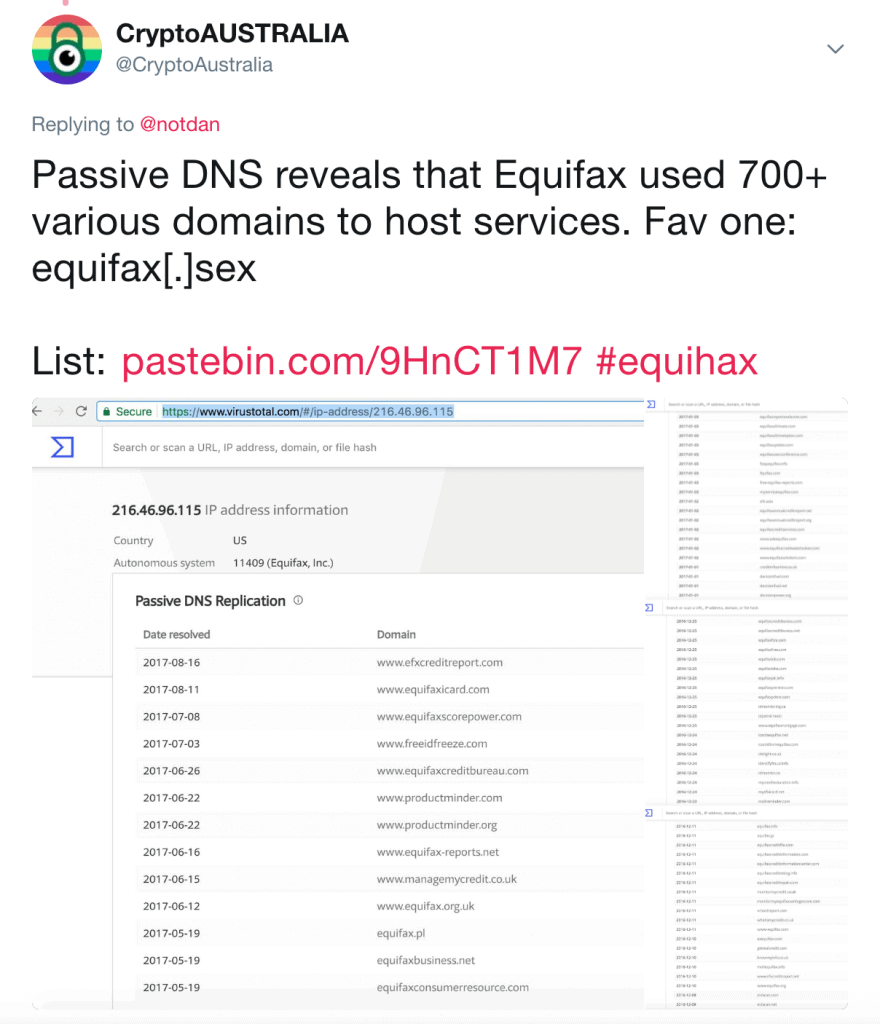
To make things worse, some businesses cannot keep a tally of their own registered domain names. Just last year, a customer service representative at Equifax was sending their customers to a phishing website for over two weeks. It is no wonder that even the Equifax employees got confused, as the company has over 700 domain name variants for their brands registered.
Bad User Interface Designs Work in the Attackers Favour
Another reason why the top-tip of ‘always hovering over a hyperlink in an email to check where it would take you’ does not work is that lousy user interface design in email clients can prevent users from to follow the advice.
For example, Lotus Notes does not display the URL location of a hyperlink if you hover over it with the mouse pointer. Yes, it takes three complicated steps to reveal what lies beneath a simple hyperlink.
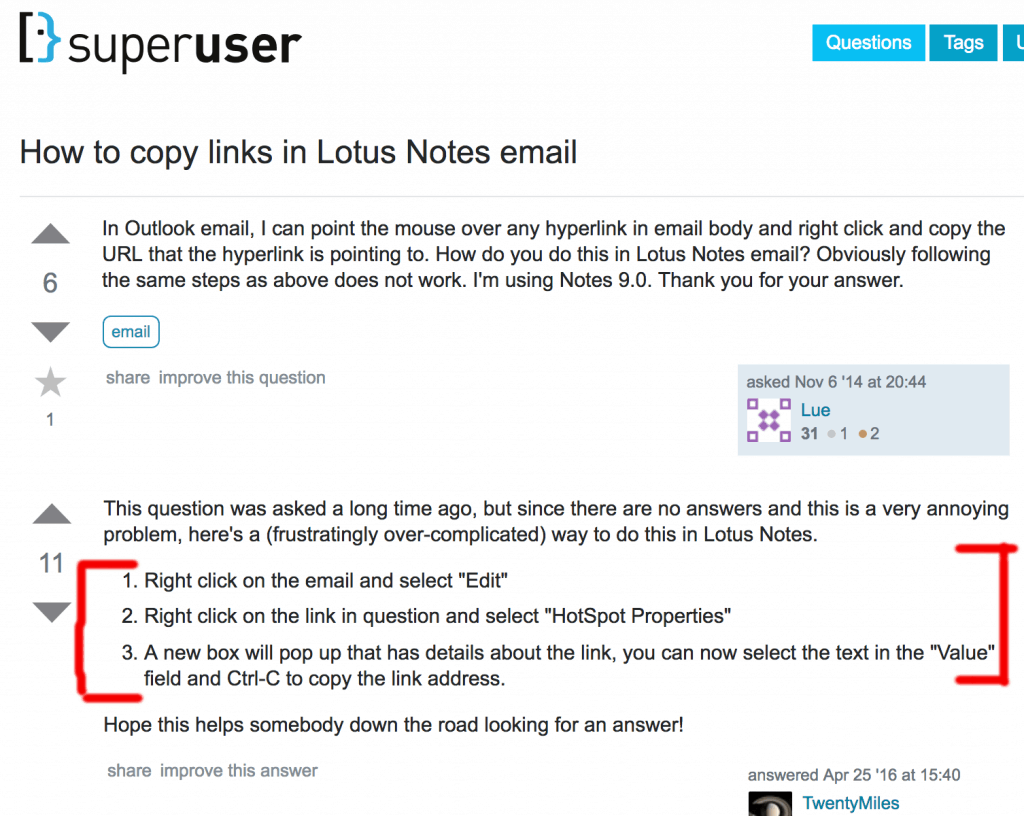
Sadly, this is not a joke
Another ‘poor’ design choice that prevents those common anti-phishing tips from working is that several smartphone email clients will only display the name of the email sender, not the email address. The native mail client for iOS, and Outlook and Gmail email clients for both iOS and Android, by default will not display the sender’s email address on an incoming email. Emails only display the sender’s name and can require a few taps to reveal the sender’s full email address. This is likely to be a design feature to save space, as screen real estate on smart devices is precious, but it has proven to be a fatal one.
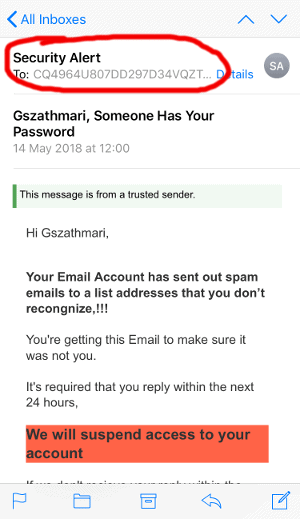
The native iPhone Mail app requires an additional tap to reveal the sender’s address
Cybercriminals exploit this fatal design. The technique is called ‘Display Name Spoofing’ and is relatively simple, yet effective method to deceive phishing victims. According to a security firm, 91% of phishing attacks are display name spoofs.
Real-World Display Name Spoofing Attempts
Our anti-phishing services intercepted the following email, in which the attacker was attempting to exploit the design weakness mentioned above. This was a typical money transfer scam whereby an attacker sends an email requesting that an urgent financial transaction be made. The name of the sender was the CEO’s, but the email domain a free internet mail provider. Interestingly, the criminal knew which members of the staff were managing payments, and were specifically targeted.
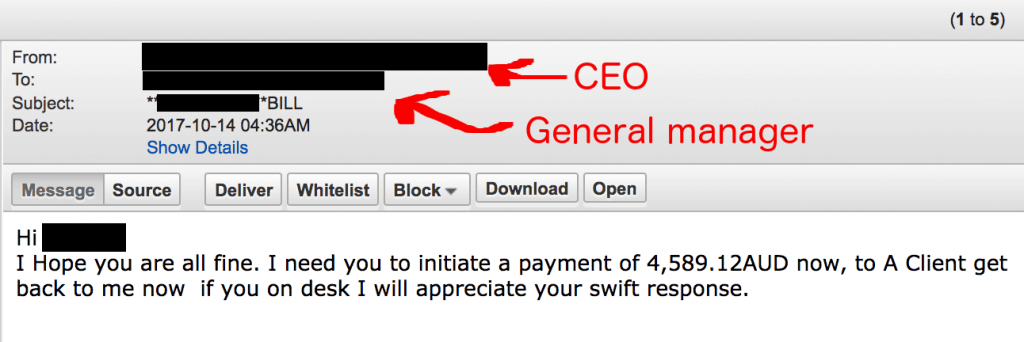
This targeted phishing email was intercepted by our anti-phishing service
So What We Can Do Then?
There is a handful of common anti-phishing tips which are regularly circulated on the internet. These decade-old tips are behind the times as the cyber threat landscape has changed significantly since the 2000s. Cybercriminals now have strong financial motivations to invest in tools, techniques and research to scam Australian businesses out of their assets and do so with a high success rate. Industry reports show that one in every twenty employees click on everything in their mailbox, which cybercriminals happily exploit for monetary gain.
How Businesses Can Protect Themselves
One way to prevent businesses from becoming a victim of fraud is to stop the deceptive emails from landing in the employee’s mailbox. Professional anti-phishing technologies will pre-screen incoming emails for specific red flag indicators of phishing, such as typical wording and text semantics, invalid digital signatures, and poor sender reputation, much of which is indistinguishable to the human eye. File attachments are analysed in safe environments for known and unknown threats, and the embedded hyperlinks are modified to perform real-time analysis when the recipient clicks on them. These advanced technologies are only available in anti-phishing services that are specifically designed to protect organisations from phishing threats.
Cybercriminals, knowing email is protected with anti-phishing technology may try to target your employees through their private mailboxes or instant messengers to circumvent corporate email protection. Businesses can defend themselves from these threats by blocking the employees from accessing malicious websites with web proxies and DNS-based blocking. These enterprise-grade services are now available to small and medium-size businesses as well.
What Individuals Can Do
Individuals can take steps to defend themselves from phishing attacks. Some of the better anti-virus products include protection against phishing and malicious file attachments in email. Browser extensions, like Windows Defender, Netcraft Extension or Blockade can block malicious websites from being loaded inside a web browser. Google’s Password Alert extension can warn you if you just entered your Google (or G Suite) password on a fake login page. Malware-blocking DNS services or software like the Pi-hole can also prevent phishing websites from being accessed, even if the victim is tricked into clicking on a hyperlink.
About Iron Bastion
Iron Bastion are Australia’s anti-phishing experts. We offer all businesses the same anti-phishing technology used by big businesses, without the big-business pricing.
Our range of services are cloud-based, fully managed and easily integrate with your existing infrastructure. Our team feature qualified cybersecurity experts, and all our staff and operations are based in Australia.
Contact us for a free consultation, or sign up for a 14-day free trial of our services today.
* * *
This article has first appeared on the Iron Bastion blog and was co-written with Nicholas Kavadias.





