By Jonathan Knudsen, Head of Global Research, Synopsys Cybersecurity Research Center
The Synopsys Cybersecurity Research Center (CyRC) recently published a vulnerability advisory related to Open5GS, which is full of dense technical detail. But what does it all mean for organizations? What’s the potential impact? To answer that, let’s take a step back.
About 5G
Let’s start by talking about the software itself. Open5GS is an open source implementation of 5G, which is the current generation of network technology used by mobile phones. It encompasses all the internals of the networks that carry voice and data all around the world.
5G is complicated. If you’ve ever seen a diagram of a 5G networks, it has a profusion of boxes and lines connecting them. Each box has a specific purpose—some for authorization, some for billing, some for controlling which data goes where. The boxes communicate with each other using protocols. A network protocols is simply a set of rules about what data will be exchanged and how, much like rules for a conversation between two pieces of software.
As with any complex software, it feels like a minor miracle just to get it working. But security is equally important. You want the system to work, but you also want it to be difficult to attack. Implementing security testing during development helps locate vulnerabilities that can subsequently be fixed before release.
About Open5GS
Open5GS is an open source implementation of the 5G specifications. It is used as a connectivity test tool by some mobile telecom related companies. For example, ng-voice is a sponsor of Open5GS.
As it described in the documentation of Open5GS, it can be used to build a private network. The support page shows it is under both AGPL-3.0 and a commercial license, which means it could be commercially deployed as a 5G core network.
About Fuzzing
Fuzz testing, or fuzzing, is especially well-suited to network protocol testing. Fuzzing means delivering deliberately malformed and unexpected inputs to software and checking to see if something goes wrong. Attackers often use fuzzing because it is a very effective method for locating vulnerabilities in software.
A generational fuzzer, such as Defensics, already know all the rules of the protocol. It knows which messages will be exchanged and what their contents should be. Because it knows how everything should look, it is very effective at generating inputs that are mostly correct but messed up in some specific way.
About Denial of Service
Synopsys CyRC research Qiang Li used Defensics to locate a vulnerability in one of the components (UPF) of Open5GS. As the advisory states, a malformed protocol message can cause a process to crash, halting one component of the 5G network.
When something is no longer available, we call it a Denial of Service, but really it just means that something has broken.
What are the consequences?
If the UPF component of the network is disabled, end users (people) are unable to use the network with their phones. Neither data nor calls will work.While the attack would be trivial to launch, the real challenge for an attacker would be finding an appropriate insertion point, i.e. being able to access the core of a 5G network in the first place. Security should always be implemented in layers, so we would hope that the 5G network components would be deployed in a way that’s difficult for an attacker to access.
About the Vulnerability
Open5GS is written in the C programming language. The vulnerability we uncovered is a classic buffer overflow vulnerability, in which too much data is written to too little memory. An attacker might be able to exploit this vulnerability to run their own code in the 5G network, possibly pivoting to compromise other components of the network, eavesdrop on data, steal sensitive information, or cause other kinds of trouble.
Vulnerabilities like this can be a serious problem if they are lying dormant in released software. By incorporating fuzzing and other security testing tools into a secure software development life cycle, development teams can find and fix vulnerabilities before releasing software. This results in lower risk for development teams and their downstream customers.
What’s it All Mean?
Software security continues to be critically important. In a world where software itself is the critical infrastructure for all other critical infrastructure, security must be built into software, infused into every phase of development. Just as nobody would consider designing and building an airplane without thinking about safety at every phase, nobody should be designing and building software without thinking about security at every phase.
Please find the Denial-of-service vulnerabilities (CVE-2022-39063) in Open5GS discovered by Qiang Li from the Synopsys Cybersecurity Research Center (CyRC) in Wuhan, China in they CyRC vulnerability advisory below:
CVE-2022-39063 is a vulnerability in the Open5GS project, an open source implementation of 5G components.
The Synopsys Cybersecurity Research Center (CyRC) has exposed a denial-of-service vulnerability in Open5GS. Open5GS is an open source project that provides LTE and 5G mobile packet core network functionalities with an AGPLv3 or commercial license. It can be used to build private LTE/5G telecom networks by individuals or telecom network operators.
When Open5GS UPF receives a PFCP Session Establishment Request, it stores related values for building the PFCP Session Establishment Response. The following source code in open5gs/lib/pfcp/handler.c causes this issue.
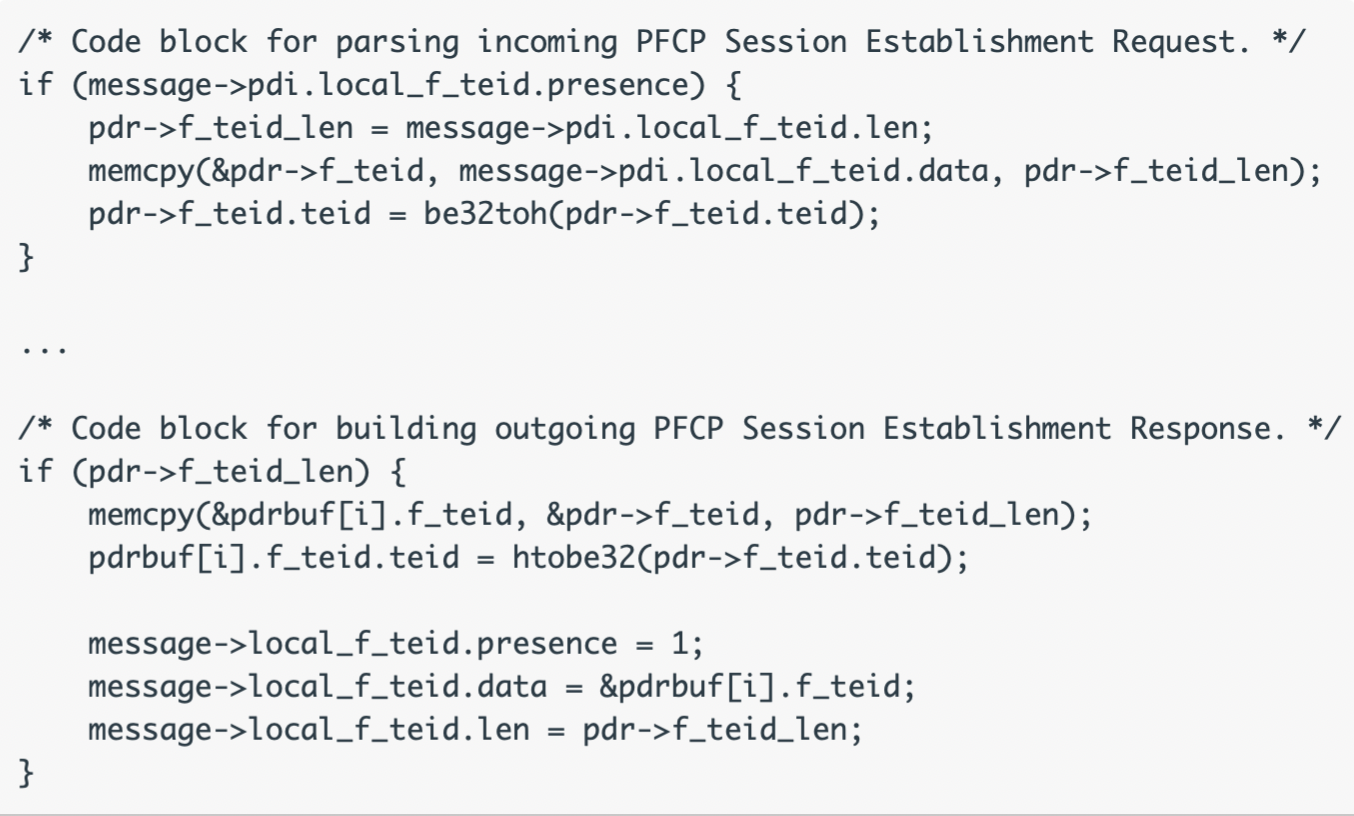
This vulnerability is caused by a memcpy() that doesn’t have the maximum length of the source and target structure validated, so a buffer overflow attack exploit is possible.
Exploitation
When connecting to the Open5GS UPF port (8805) for the PFCP protocol and sending an PFCP Association Setup Request followed by a PFCP Session Establishment Request with PDR.F-TEID.IPv6-Address set to a duplicated IPv6 address [e.g., 16(0xff) 16(0xff)], this buffer overflow attack causes a segmentation fault in Open5GS.
Affected software
Open5GS 2.4.9 and earlier versions
Impact
Exploitation of this vulnerability would lead to a denial-of-service for the LTE/5G mobile packet core network.
CVSS 3.1 base score: 8.2 (high)
CVSS 3.1 vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/
Remediation
Synopsys recommends upgrading to Open5GS commit 444e182 or later. The vulnerability is patched as of commit d99491a on August 12, 2022, and commit 444e182 on August 14, 2022.
Discovery credit
Qiang Li from the Synopsys Cybersecurity Research Center (CyRC) in Wuhan, China, discovered the issue using the Defensics® fuzz testing tool.
Timeline
- August 10, 2022: Initial disclosure
- August 16, 2022: Open5GS confirms vulnerability
- August 17, 2022: Synopsys validates the fix
- September 9, 2022: Open5GS version 2.4.10 is released – fixing the bug
- September 14, 2022: Synopsys publishes advisory
About CVSS
FIRST.Org, Inc (FIRST) is a non-profit organization based out of US that owns and manages CVSS. It is not required to be a member of FIRST to utilize or implement CVSS but FIRST does require any individual or organization give appropriate attribution while using CVSS. FIRST also states that any individual or organization that publishes scores follow the guideline so that anyone can understand how the scare was calculated.
About the Synopsys Software Integrity Group
Synopsys Software Integrity Group helps development teams build secure, high-quality software, minimizing risks while maximizing speed and productivity. Synopsys, a recognized leader in application security, provides static analysis, software composition analysis, and dynamic analysis solutions that enable teams to quickly find and fix vulnerabilities and defects in proprietary code, open source components, and application behavior. With a combination of industry-leading tools, services, and expertise, only Synopsys helps organizations optimize security and quality in DevSecOps and throughout the software development life cycle. Learn more at www.synopsys.com/software.
About Synopsys
Synopsys, Inc. (Nasdaq: SNPS) is the Silicon to Software™ partner for innovative companies developing the electronic products and software applications we rely on every day. As an S&P 500 company, Synopsys has a long history of being a global leader in electronic design automation (EDA) and semiconductor IP and offers the industry’s broadest portfolio of application security testing tools and services. Whether you’re a system-on-chip (SoC) designer creating advanced semiconductors, or a software developer writing more secure, high-quality code, Synopsys has the solutions needed to deliver innovative products. Learn more at www.synopsys.com.