Introduction
Tenable Research discovered security flaws in a popular transportation management app that allowed access to student location data. While these issues have been fixed, the findings again prove the importance of strong authentication and access control.

On December 13, 2023, Tenable Research publicly disclosed security flaws uncovered in Edulog’s Parent Portal suite of products. These flaws allowed access to potentially sensitive information involving K-12 students including student names and assigned bus routes, parent contact information, GPS data, and the configuration details – such as usernames and encrypted passwords for third-party integrations – for individual school districts.
The Who & What
Edulog (Education Logistics, Inc.) provides school districts throughout North America with products and services related to managing and optimizing transportation needs. Their offerings aid in bus route planning, GPS tracking and fleet management. In particular, Parent Portal and Parent Portal Lite allow parents and school staff access to real-time information regarding a student’s school bus transportation. This information may include a live view of a bus’s current location, pick-up and drop-off times, and notifications about delays or route changes.
Under normal circumstances, parents or school staff wishing to use one of the Parent Portal applications simply sign up for a free account via one of the apps. The app they use depends on which features their school district is signed up for. Once signed up for an account, a registration code is required to obtain access to bussing information for a particular school or district. These registration codes are provided to parents and staff by the schools themselves.
Edulog Parent Portal Lite login screen
The How
Tenable researchers discovered that the backend services for these products lacked sufficient authentication and access control implementations. After creating a free account, researchers attempted to access the API endpoints for the services directly, rather than using the apps. They soon realized that the access control measures in place were client-side restrictions enforced only by the apps themselves. By submitting requests manually, they had seemingly unfettered access to any information that could be obtained via the Parent Portal API.
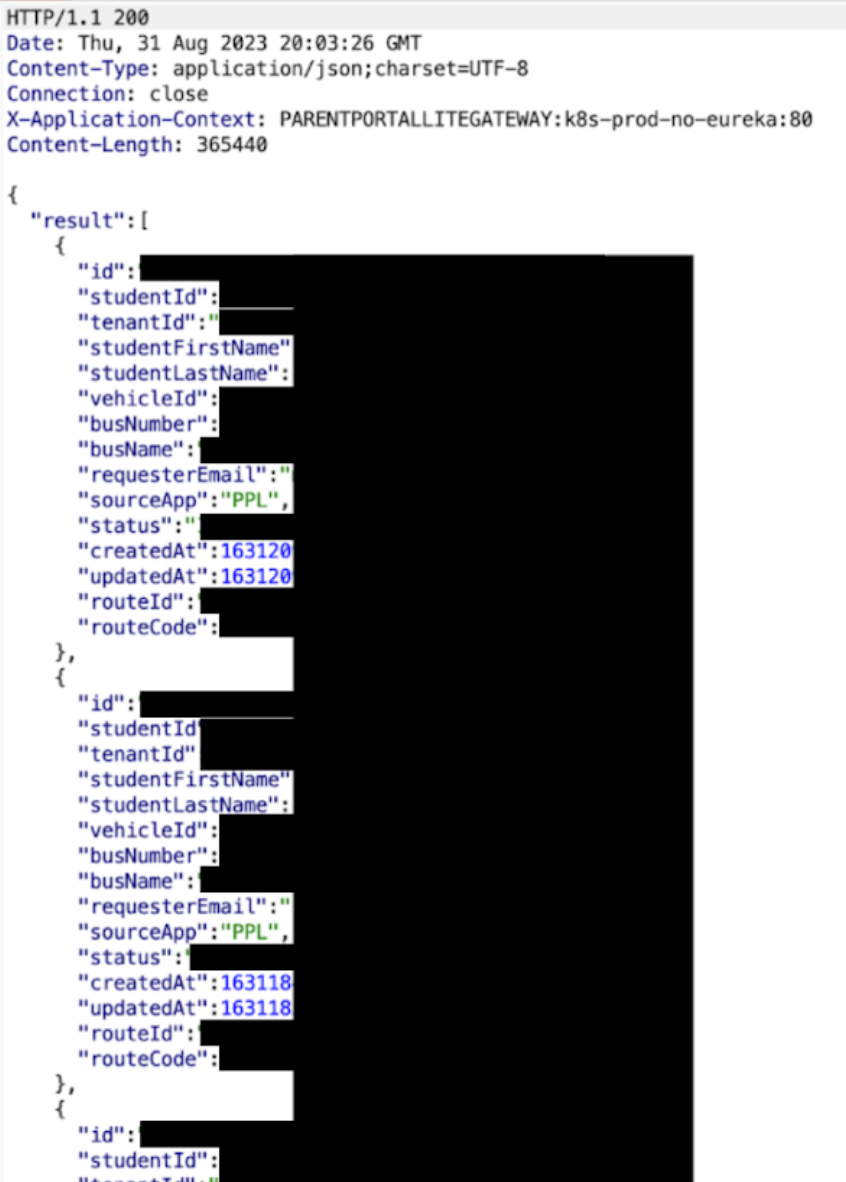
Accessing student bus information
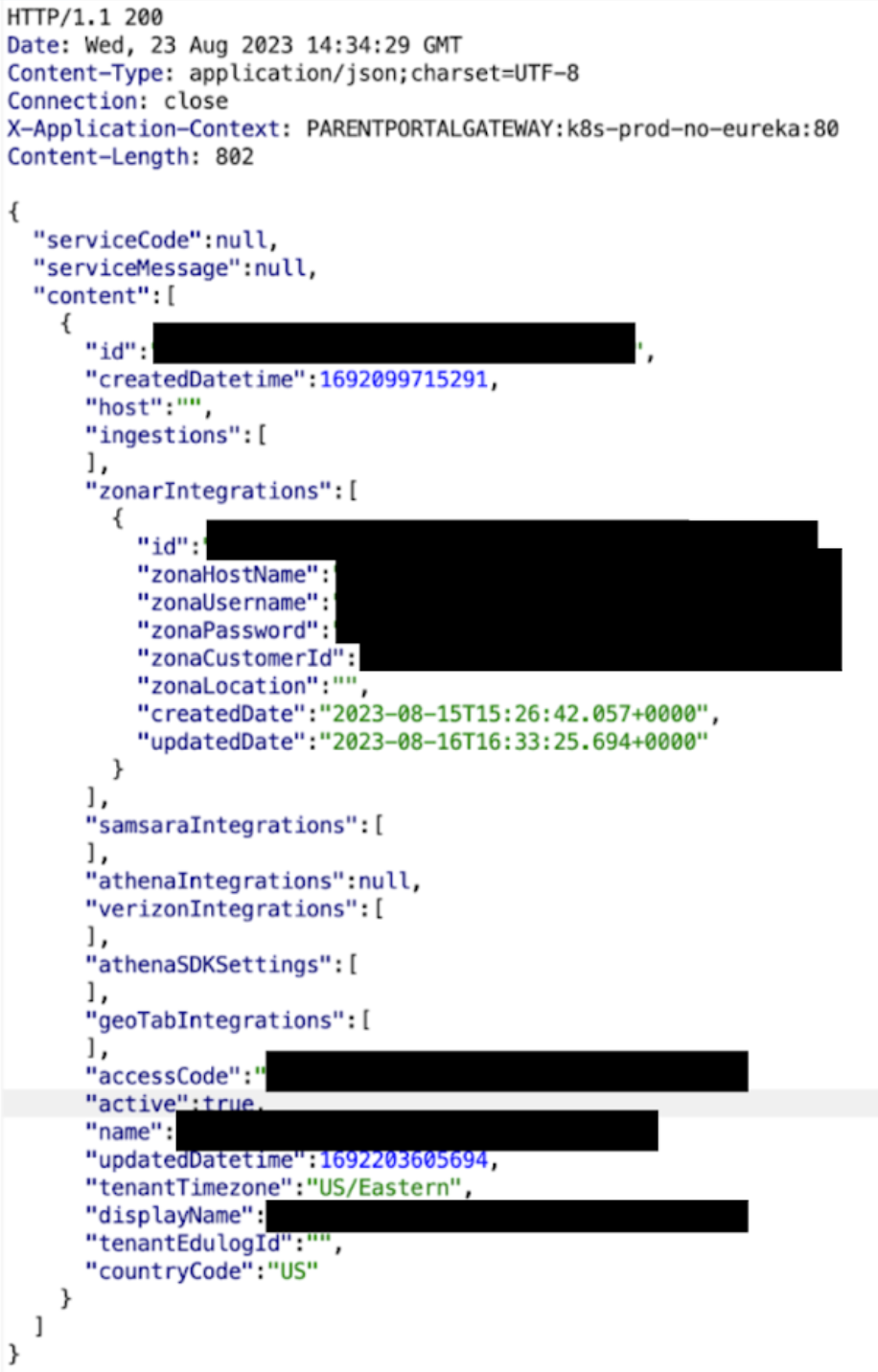
Accessing school district configuration data
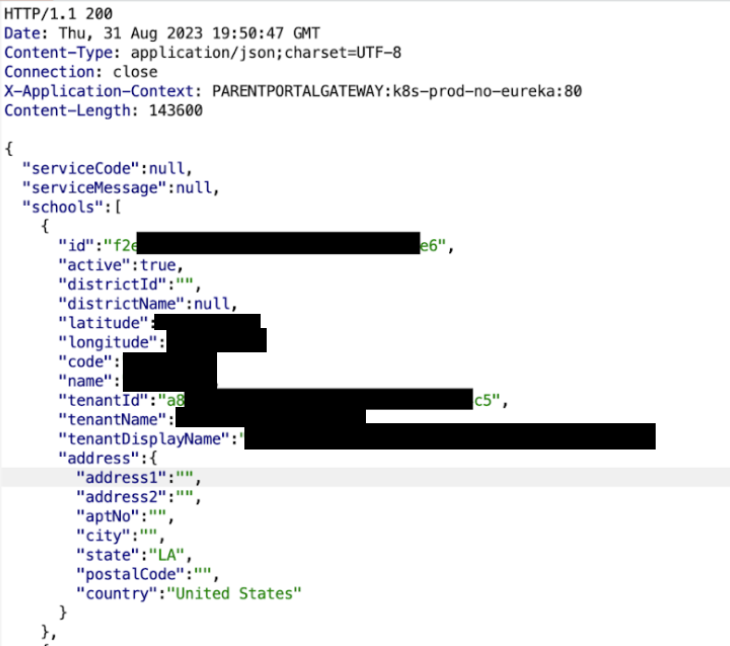
Customer enumeration
The Response
Tenable reported these issues to Edulog on September 13, 2023. As of November 30, 2023, Edulog has stated that all reported issues have been resolved. For further technical details, please refer to TRA-2023-41.
These types of issues are all too common in industries where the concept of data security is often conflated with compliance standards. In fact, it’s likely that much of the information that could have been obtained via the Parent Portal API, such as names and addresses, was already considered open data and complied with regulatory requirements. For example, in the U.S., the Family Educational Rights and Privacy Act (FERPA) states the following:
“Schools may disclose, without consent, ‘directory’ information such as a student’s name, address, telephone number, date and place of birth, honors and awards, and dates of attendance. However, schools must tell parents and eligible students about directory information and allow parents and eligible students a reasonable amount of time to request that the school not disclose directory information about them.”
While it should go without saying that the key element with the Parent Portal flaws was access to information regarding the whereabouts of minors and fleet configuration details, Tenable does not want to advocate that any one party is to blame. While Edulog is ultimately responsible for the bugs in their services, they clearly took Tenable’s report seriously and provided fixes in a timely manner. This is a situation where all those involved – Edulog employees, agents for the school districts, and parents using the services – are responsible for making sure the data relating to these services is handled properly.
For example, even without the vulnerabilities discovered in the Parent Portal services, there isn’t necessarily anything stopping a malicious actor from signing up for an account and obtaining a registration code for a given school through other means. The actor could ask another parent, call the school and pretend to be a parent, or simply search for one on the internet:

School district publishing confidential registration code on their website
Tangentially, it’s worth pointing out that this is another situation where consumers are increasingly reliant on the transparency of the providers of cloud-based products and services. Tenable requested information regarding Edulog’s plans to publish a security advisory, release notes, or some other notification for customers and affected parties to review and received the following response:
“Re the advisory, having looked at similar disclosures on your research page, and that given that the potential vulnerabilities have been mitigated with no action needed on the part of our customers, Edulog feels that a separate advisory is not necessary in this case.”
This means that aside from Tenable’s public disclosure, it’s likely Edulog’s customers and other consumers would never have been made aware of these issues and the potential risks they were exposed to.
Tenable strives to equip its customers with the tools necessary to assess their organization’s security posture and devotes significant resources to discovering and publishing new and novel vulnerabilities such as this. If you’re interested in learning more about our offerings, please reach out.




