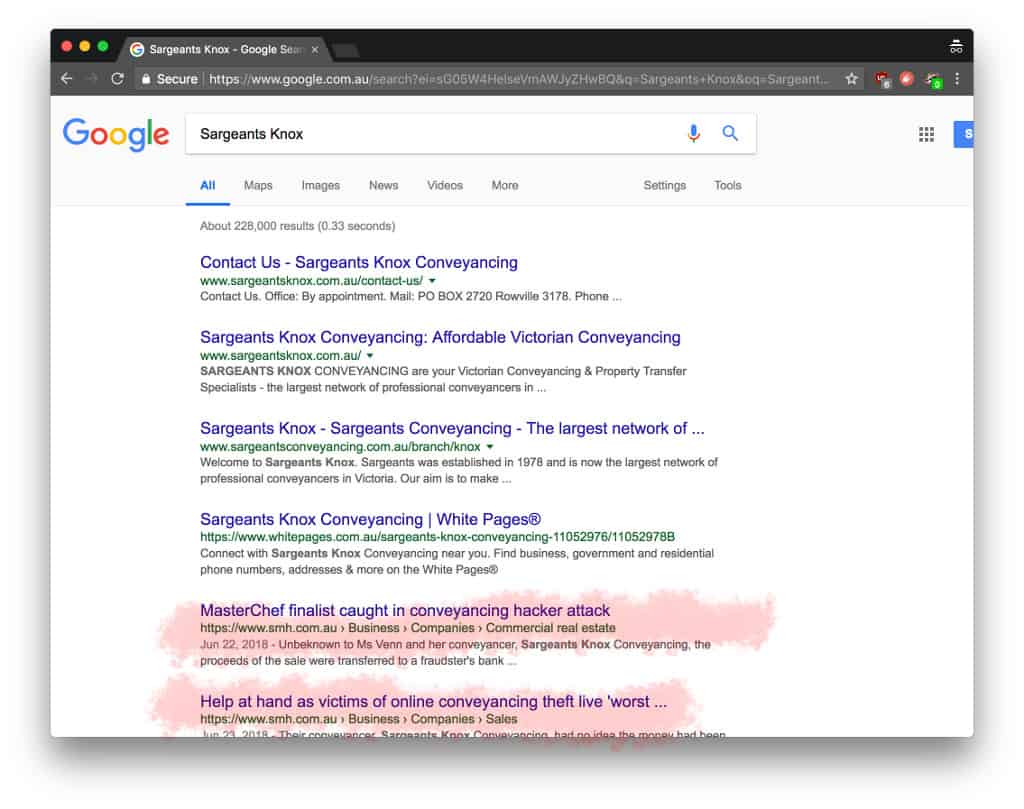
You may have read about the highly publicised PEXA fraud which was reported whereby a Melbourne family was left homeless. As it transpired, the family’s conveyancer had their email hijacked by a cybercriminal. This lead to the conveyancer’s PEXA account being compromised and ultimately the theft of $250,000 by the criminal misdirecting settlement funds. The banks and PEXA have denied liability thus far, putting the responsibility on the conveyancer. This fraud will probably ruin the conveyancer’s practice (or at least the brand name) as you do not have to look far to find their business name in connection with the fraud. The internet never forgets.
As of today, standalone transfers and caveats transactions must now be done with PEXA. In July 2022, all conveyancing transactions will be mandatory on the platform in NSW. Iron Bastion is here to help legal and conveyancing practices protect themselves from cybercrime which can lead to fraud against their clients and their business.
Iron Bastion is publishing a simple questionnaire today (link is at the end of the article) to allow conveyancing and legal practices to assess their cybersecurity posture and therefore their ability to use the e-conveyancing platform safely and securely.
Even though PEXA has promised to make changes to the platform itself to make it more secure, organisations need to have good cybersecurity practices in their business to protect their email and business systems from being hijacked and used to commit fraud. Our assessment provides a simple way to determine your business’s exposure to cybercriminals which are actively targeting the Australian legal industry.
How A Hacked Email Account Led to a $250,000 Fraud
The PEXA attack is nothing new to cybersecurity experts. The cyber attack is a well-known class of cybercrime known as BEC (Business Email Compromise), whereby cybercriminals hijack email accounts to commit fraud by misdirecting payments either from a client to the business or from the business to a supplier.
Organisations which act as agents for people and businesses in large financial transactions, such as solicitors, conveyancers, and accountants are lucrative targets for cybercriminals. According to the latest ACCC’s Scamwatch report, Australians lost at least $22.1 million in 2017 through BEC. In 2017, the New South Wales Law Society and the Queensland Law Society both issued various scam alerts to its members warning of cyber-attacks explicitly targeting Australian law firms.
What the hacker did in this instance would have been a two-step process. The first step would have been to hijack the business email of the conveyancer.
Hackers can take over business mailboxes by crafting specially designed emails which entice victims to click. Once clicked, your password or the control over your computer is in the hacker’s hands. This technique is what is known to cybersecurity experts as phishing. For a more detailed definition of phishing, refer to our previous report.
The second phase of the e-conveyancing fraud was that the attacker gained access to the conveyancer’s PEXA account. The hacker then waited and surreptitiously changed bank account details for payment directions, which were then signed by the conveyancer meaning the criminal made off with a portion of the settlement funds before anyone realised what was going on.
Is Your Practice Secure Enough for e-Conveyancing?
We have carefully examined the methods of cybercriminals involved in BEC and e-conveyancing fraud. Theses scams require a specific combination of cybersecurity weaknesses to succeed. Our assessment has narrowed down these weaknesses to nine questions. The questionnaire also provides you with a report that not only allows you to identify areas for improvement in your business but can help your IT staff (or IT service provider) to fix the identified cybersecurity issues.
To assess how vulnerable your business is to e-conveyancing scams and BEC fraud, complete our PEXA cybersecurity readiness questionnaire here.
* * *
This article has first appeared on the Iron Bastion Security Blog and was co-written with Nicholas Kavadias.





