You may have heard of the recent cybercrime perpetrated against the Australian e-conveyancing platform PEXA. A former MasterChef finalist and her family had $250,000 stolen from a property purchase transaction on the platform at settlement. In the following article, we explain the likely ways the fraud occurred and what practical things you can do right now to protect your business from similar attacks.
According to this Fairfax news article, the victim’s conveyancer transferred money for the property settlement into the ‘wrong’ bank account. As it turns out, the conveyancer’s email had been compromised allowing their PEXA account to be hijacked. The cybercriminal then tampered with bank account details on the PEXA platform. As a result, the conveyancer signed off on $250,000 of the purchaser’s funds which were meant to go to the vendor but instead went to a bank account controlled by the cybercriminal.
How A Hacked Email Account Can Lead to a $250,000 Fraud
The PEXA attack is nothing new to cybersecurity experts. The attack is a well-known class of cybercrime known as BEC (Business Email Compromise), whereby cybercriminals hijack email accounts to commit fraud by misdirecting payments either from a client to the business , or from the business to a supplier. Organisations which act as agents for people and businesses in large financial transactions, such as solicitors, conveyancers, and accountants are lucrative targets for cybercriminals. According to the latest ACCC’s Scamwatch report, Australians lost at least $22.1 million in 2017 through BEC. In 2017, the New South Wales Law Society and the Queensland Law Society both issued various scam alerts to its members warning of cyber-attacks explicitly targeting Australian law firms.
What the hacker did in this instance would have been a two-step process.The first step would have been to hijack the business email of the conveyancer.
Hackers can take over business mailboxes by crafting a specially designed email with a hyperlink pointing to a password-stealing fake login page, or a malicious file attachment. The attacker emails the victim in a variety of ways to try to trick them into clicking the link. Once the victim clicks, the email password is in the hacker’s hands. This technique is what is known to cybersecurity experts as phishing. For a more detailed definition of phishing, refer to our previous report.
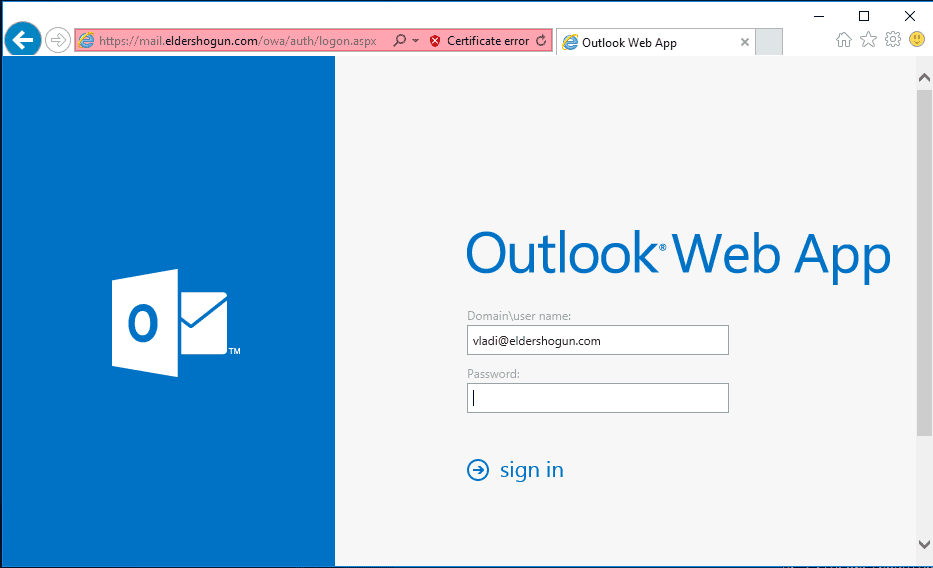
A pixel-perfect clone of the Outlook Web Access login page stealing passwords
In this instance, the hacker may not have even needed to send the conveyancer an email to hijack their mailbox. According to data breach website HaveIBeenPwned the conveyancer’s Bigpond email account was on the list of hacked credentials involved in an August 2017 data breach. If the conveyancer had reused the same password for their mailbox account as in the breach data, the hacker could simply log into their email service. According to a recent study, over 80% of people online reuse passwords on multiple cloud services. With over 1.7 billion hacked credentials from data breaches such as LinkedIn, Netflix and Adobe, this is a very real scenario.
The second phase of this scam, which is what makes this novel, is that the attacker gained access to the conveyancer’s PEXA account. The hacker was able to reset the conveyancer’s password via the PEXA Workspaces login page by using the ‘Forgot Password’ feature. The attacker then used the password reset link, logged into PEXA and created themselves a new account for the conveyancer’s organisation and waited surreptitiously for transactions where they could change bank account details. These details were then signed off by a conveyancer in the organisation, being none the wiser that the bank details had changed on the platform.
What You Can Do Today to Prevent BEC Scams at Your Firm
This fraud could have been prevented by PEXA mandating the use of Two-Factor Authentication (2FA) for logging into a workspace. 2FA is a technique used to prevent unauthorised access to cloud services. As of today, 2FA is not available at PEXA, albeit the company has promised to add the additional layer of security soon, at least for password resets.
Hey @softveda @jpwarren one of our clients has forwarded us this email which was sent to PEXA users. Looks like they just realised they need 2FA
full newsletter here? #auslaw https://t.co/kDJlTIzd99 pic.twitter.com/PPlbHJXoM2— Iron Bastion (@IronBastionAu) June 22, 2018
While PEXA is busy with adding 2FA, you can make changes to your email service to protect your firm from email hijacking and BEC fraud.
The conveyancer is ultimately at fault for not confirming what the bank account details should have been on PEXA before signing. The conveyancer could have implemented a number of cybersecurity best practices to prevent the fraud.
Iron Bastion advises you make the following changes to the IT of your business. If you are a business owner, then do yourself a favour and ask your IT staff or provider to set up the following security features:
Two-factor Authentication: Protecting Your Email Service
The most effective way of preventing a business email hijacking is to have two-factor authentication (2FA) protecting your email. Two-factor authentication is an extra layer of security that requires you to key in a one-time PIN when logging in to an email account every once in a while or when the login request has come from a new device, browser, or location.
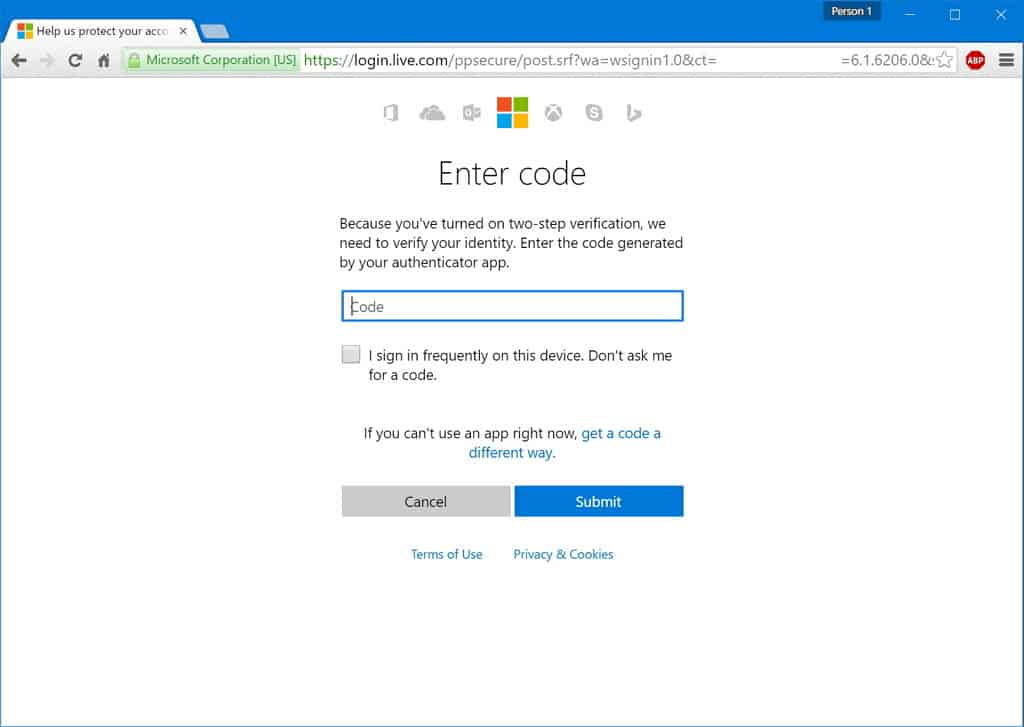
Two-factor authentication on the Office 365 platform
This may sound tedious, but it is a powerful security measure to prevent hackers from hijacking your mailbox and using it to reset passwords on cloud services such as PEXA. Services like G Suite and Office 365 already support 2FA features for free, they just need to be turned on and configured for your email service.
Tune your Email Service To Preventing Email Impersonation Attacks
Cybercriminals often rely on two distinct email spoofing techniques for taking over email. Criminals typically pose as a person of authority from the victim’s organisation and lure them into clicking on web links leading to fake login pages, opening file attachments containing malware, or giving away passwords and sensitive information.
The good news is that you (or your IT staff) can make changes to your email service to reduce the risk of email-based impersonation attacks. In a recent article, we published how you can combat Email Address Spoofing and Display Name Spoofing impersonation attacks.
Not Every Antivirus Product Is Made Equal
Secondly, you should ensure you are using the right anti-virus suite and that all your devices have an up-to-date antivirus installed. Better antivirus products can not only protect your computer from viruses, but they can also safeguard you from phishing and ransomware attacks.
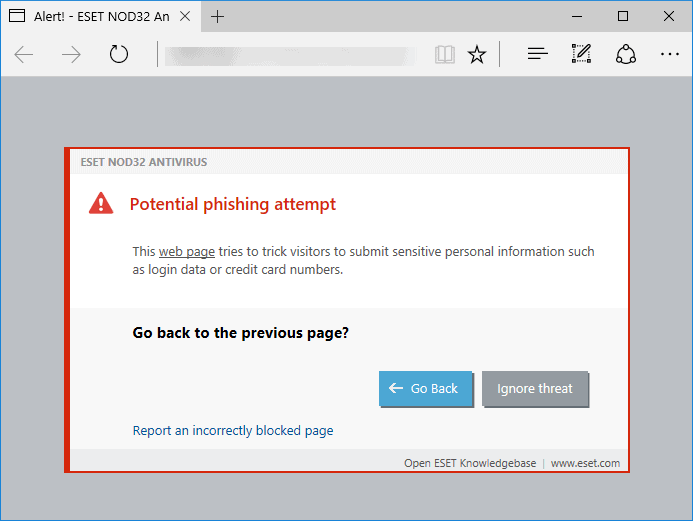
How certain antivirus products block phishing sites
Sadly, many IT service providers do not deploy the right antivirus for your business needs. They often resell you products that come in heavily-discounted software bundles or offer the best resale margin, rather than picking a product that provides superior protection based on independent software testing.
Ensure that every device in your business has an antivirus product and that the product features include phishing protection, safe browser plugins, ransomware protection and sandboxing.
Anti-Phishing Protection For Your Email Service
To prevent cybercriminals from luring your employees into email account hijacking, your incoming emails should be pre-screened for phishing attempts.
You should be aware that neither built-in spam filters in Office 365, G Suite nor previous generation anti-spam services feature advanced anti-phishing techniques to pre-screen emails for phishing. Hence, these old technologies will leave your firm unprotected from today’s cyber-threats.
Anti-phishing services, on the other hand, feature techniques like Machine Learning and Artificial Intelligence (AI) algorithms to identify phishing attempts. Special algorithms look for the specific red flags indicating a phishing attempt, such as typical wording and text semantics, invalid digital signatures, and poor sender reputation. File attachments are also analysed in safe environments for known and unknown threats, and embedded hyperlinks are modified to perform real-time analysis (and block) any malicious URL when the recipient clicks on them. These technologies are only available in anti-phishing services that were specifically designed to protect organisations from phishing threats.
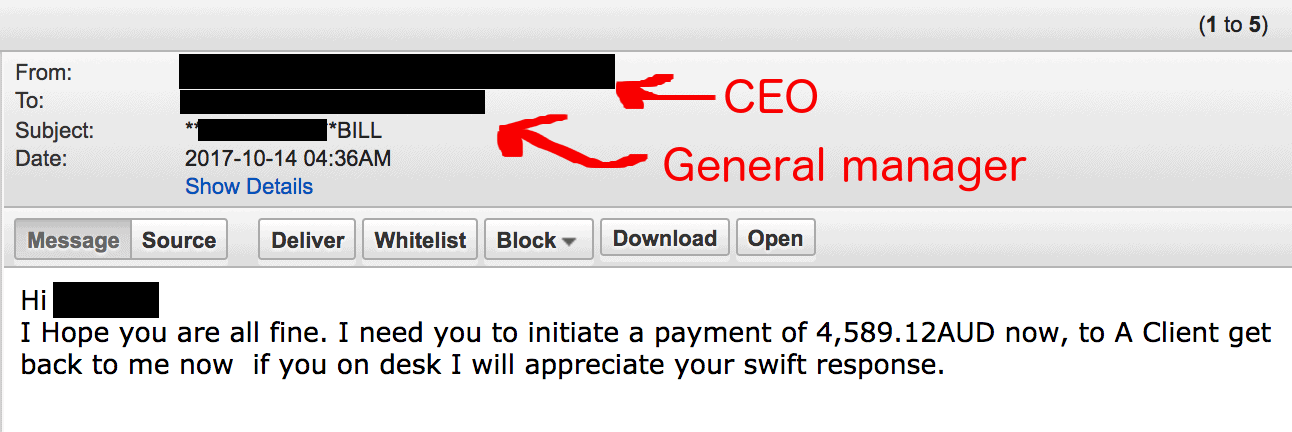
Advanced anti-phishing algorithms can catch spear phishing attempts like this
Advanced Anti-phishing protection is available as an add-on to and works in conjunction with your existing email service. You can buy software services or on-premise products to pre-screen your emails for phishing. Many businesses subscribe to a managed service provided by IT or cybersecurity service providers like Iron Bastion. If you are interested in the types of anti-phishing services the top 100 law firms in Australia are using, please refer to our research article.
Managed Web Browsing Protection
More sophisticated cybercriminals may try to outsmart these advanced anti-phishing technologies used in business email by targeting staff through their private email and instant messenger accounts instead.
Free email providers such as Gmail, Yahoo Mail, etc. do not have advanced anti-phishing protection that your corporate email service may have. Criminals may also try to contact your employees via Facebook Messenger, WhatsApp or iCloud Messenger. These services are not capable of identifying and blocking these targeted attacks on your employees, but you can protect your staff with what is known as a DNS firewall, which can be set up on all of your employee devices, protecting them even when they are not in the office.
Web browsing protection can block your browser from loading phishing websites
DNS-based web browsing protection services can block your employees from accidentally visiting websites hosting fake login pages or hosting malicious password-stealing software and malware. Web browsing protection services are not only for big businesses, services such as ours are available for even a sole practitioner protecting a single device. We suggest subscribing to such as service to get comprehensive protection for your business.
Phishing Awareness Training
Phishing is not merely a technology problem but is a human problem too. The last line of defence are your employees. Hence they need to be vigilant and trained to identify phishing attempts.
In covering the human element, phishing simulation is an effective way to test and train employees’ cybersecurity awareness and susceptibility to social engineering tactics, spear phishing and ransomware attacks. With the right tools, you can simulate a phishing attack against your own business. You can then identify vulnerable employees (i.e. those who fell for the attack) and train staff with appropriate education. There is both free and paid security awareness training materials available to your staff to help them recognise and respond to phishing attempts.
Summary
Cybercriminals targeting the legal and conveyancing sectors in Australia are likely to hack businesses not using Two-Factor Authentication (2FA) or without anti-phishing protection in place. Based on publicly available data, they can quickly assess which firms are utilising anti-phishing technologies and which are not. Hackers rely on various phishing techniques to compromise corporate email accounts first, which they then use to commit payment redirection scams.
In this recently publicised story, a cybercriminal tampered bank account details on the PEXA platform after hijacking a conveyancer’s email. The conveyancer later signed off on the bank details not realising they have been changed. Although PEXA does not support robust authentication methods such as two-factor authentication yet, you can still take security measures to prevent your business from becoming a victim of fraud. By applying simple changes like turning on two-factor authentication on your email platform can reduce the chances of your business becoming a target.
For more information, please visit Iron Bastion to see their range of services and solutions.
* * *
This article has first appeared on the Iron Bastion Security Blog: Australia’s anti-phishing experts, and was co-written with Nicholas Kavadias.





