Ever wondered how you can deliver security awareness training to staff in your organisation that they will love? In this article, we are revealing the techniques we find useful in our training sessions which should help you get started with your first phishing awareness training session for your organisation.
Iron Bastion delivers tailored phishing awareness training to businesses in Australia to raise awareness around phishing and social engineering. Our experience has garnered insights into and how raise awareness in organisations in effective, fun and informative ways.
Why Phishing Needs Special Attention
Phishing is the foot in the door to an organisation and usually the initial step in payment redirection scams and Business Email Compromise (BEC) fraud. Cybercriminals see small businesses as low hanging fruit because they lack dedicated IT security personnel, immature and ad-hoc business process and staff who do not have the training or experience to deal with computer-based fraud.

According to the latest Telstra Security Report, the two most common types of cyber attacks targeting businesses in Australia are phishing attacks and Business Email Compromise (BEC). The Office of the Australian Information Commissioner (OAIC) also reinforces the fact that the majority of data breaches are attributable to phishing.
The good news is that the risk of phishing is solvable with the right combination of education, business process changes and anti-phishing technology.
Our in-house Experience with Phishing Awareness Training
We have probably all participated in new hire inductions or security awareness training sessions that bore everyone to death with irrelevant and boring facts, platitudes, and outdated tips.
Even though the topic of security awareness may not sound exciting at first, good content will grab your audience’s attention. Just think of the TV series ‘The Office’, a successful show built around the daily errands of a boring paper company in the sleepy town of Scranton.
In a similar way to the show, your employees will find your sessions captivating if your content is well written. Remember, “Content is king”, wrote Microsoft founder Bill Gates in 1996, and it is very applicable to in-house training as well.
We find the following to tips help us capture the attention of audiences:
#1. Make Your Content Relatable
First, make your content as familiar as possible. There is nothing more detaching than parroting:
- old, stale facts of about multi-million dollar cyber heists from over two years ago;
- case studies, stories from other countries, or unrelated industries.
Instead, use a recent article from the local news in the same or similar industry to illustrate why the latest cyber threats are relevant to your organisation. For instance, if your industry is legal services, tell them the fascinating story of how a cyber attack brought the law firm DLA Piper to its knees, globally.

Similarly, when a new wave of payment redirection fraud hit the legal sector in Australia last year, we often cited the SMH article elaborating how a particular case of electronic conveyancing fraud left the client, a former MasterChef contestant and her family, homeless. The story piqued our client’s interest because many of them were also using the same e-conveyancing platform and had security concerns.
#2. A Picture Is Worth a Thousand Words
Obtain screenshots of actual phishing emails which have targeted your business. Real emails will illustrate why a high-level of vigilance is required, and how outdated tips like ‘always be suspicious of emails written in poor English’ rarely work.
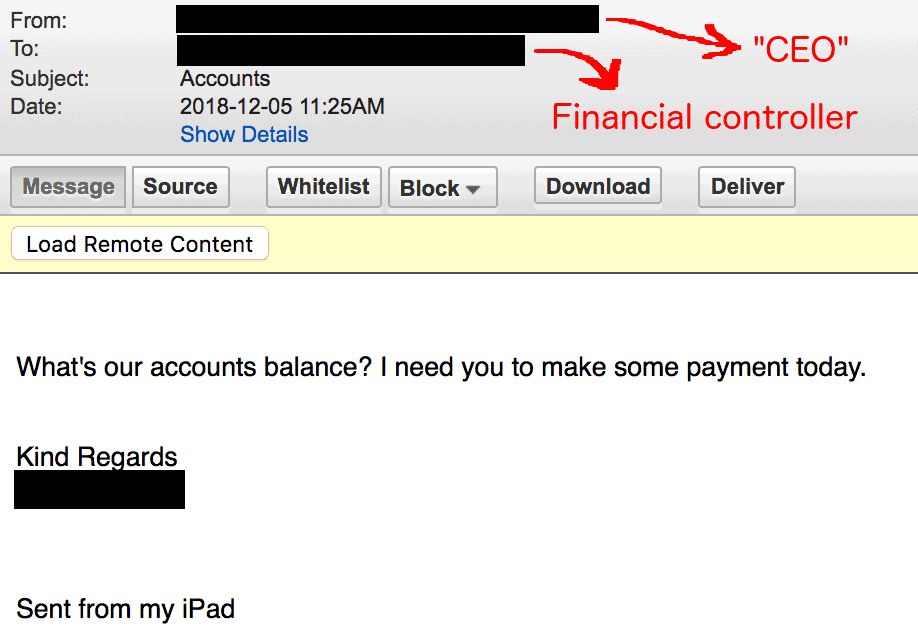
A fake email impersonating the CEO (Source: Iron Bastion)
A good source of these highly-sophisticated emails can be the email administrators of your company’s IT team.
#3. Make Everyone Comfortable
Book in a quiet and spacious room for classroom training and allow plenty of time for the Q&A session at the end. We reckon that the best time to start the training is around 10 am, which is the most productive time of the day according to studies.
Provide snacks and refreshments to hold everyone’s attention throughout the session. Your presentation segment should not be longer than 45 minutes to prevent the participants from drifting off even though your content is genuinely engaging.

A little treat can make a big difference
As for the delivery of your content, do not lecture. Be a mentor instead. We find it more engaging when the participants can interrupt us with questions throughout the session. In case you feel overwhelmed by the interruptions or get behind the schedule, politely ask your audience to keep the remaining questions to the end. Remember, your attitude is a little thing that can makes a big difference.
Regarding the Q&A session, try to foster a friendly discussion. Your audience will be eager at this point to ask questions. If you cannot answer some of them, do not worry! Perhaps someone else can from the audience. Otherwise, tell the person you will get back to them with your answer within a day.
#4. Implement Positive Change the Easy Way
Change management is a topic that is broad enough to fill a book. Even with the best of intentions, employees may still resist a positive change if they hate it. To deal with this type of resistance, we like to encourage our class to follow good security practices at home first.

Source: changedynamics.biz
For instance, credential stuffing is one of the methods criminals get into work mailboxes to commit business email compromise fraud. In short, bad actors take passwords of your staff leaked from previous data breaches and use them to access work emails en masse. Your staff should choose unique passwords everywhere and use password managers to remember them.
We like to demonstrate how anyone can protect their personal user accounts. Once everyone sees the value of a variety of good security practices at home, they will follow the same practices in the office as well.
For example, personal social media accounts (e.g. Facebook) and game accounts like PlayStation Network and Fortnite are often hijacked with the credential stuffing technique and then sold on the dark web for as low as $2. They are easy targets as people tend to reuse their favourite passwords even when they have been leaked in data breaches.
https://www.youtube.com/watch?v=VIymJH3PFNA
For an individual, it is devastating to lose access to a personal account. So once we establish the dangers of password reuse in the training, we explain how they can prevent this from happening to them and their family. Namely, they should:
- not reuse any favourite passwords across websites;
- rely on password managers to remember these unique passwords; and
- turn on two-factor authentication where the feature is supported.
To familiarise the audience with unique passwords and password managers, we hand out vouchers for products like 1Password and let them discover the benefits themselves.
Password managers allows anyone to remember hundreds of passwords
Similarly, you should demonstrate how two-factor authentication (2FA) can further protect personal accounts from hacking. We like to point the audience to TwoFactorAuth.org, a website showing how to enable 2FA on the most popular online services. A free handout could be a YubiKey device, which makes two-factor authentication easy compared to SMS-based one time codes.
The idea is that when you decide to introduce 2FA in the office, you will not be met with any resistance, because everyone is already familiar with the concept of robust authentication technologies and happy with them.
#5. Validate Your Results with Phishing Simulation
Finally, the proof of the pudding is in the eating. Before the training, phishing simulation is a great way to measure your organisation’s exposure to phishing attacks.
The benefits are twofold:
- you can identify members of your staff vulnerable to social engineering; and
- measure the effectiveness of your training.
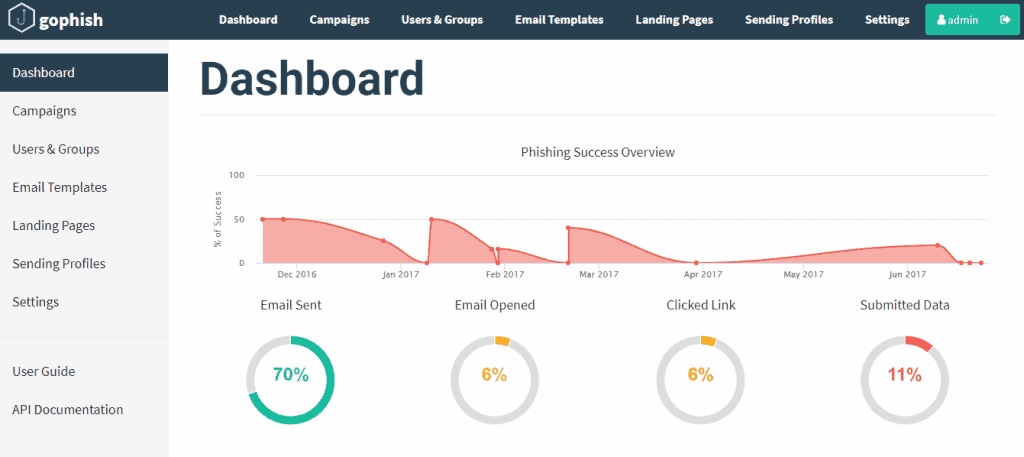
GoPhish phishing simulation tool is showing the results of a recent campaign (Source: GitHub)
We prefer to use actual phishing emails as templates to mimic real-world attacks as close as possible. It is easier than you think to be inspired to develop emails for your phishing campaign because good email templates can be found right in your junk/spam folder.
Apart from your mailbox, GitHub is also an valuable source of fresh email templates:
- https://github.com/securestate/king-phisher-templates/tree/master/Email_Templates
- https://github.com/criggs626/PhishingTemplates/tree/master/emails
- https://github.com/rfdevere/templates
To run lifelike simulation campaigns, you can either rely on open source tools (GoPhish, King Phisher) or paid products. The benefit of the latter is the free templates which come with the tools. The paid products also feature phishing awareness e-learning material such as videos and interactive quizzes.
Our experience is, however, that nothing beats the face-to-face classroom delivery format for effectiveness. This is why we prefer relying on open source tools and provide real value with the classroom-based training instead.
#6. After the Awareness Training
Your job is not done when the classroom session ends. We have all participated in meetings where we forgot what everything was about at the moment we leave the room. The good news is that we have a few tricks up in our sleeves to help you achieve a long-term impact.
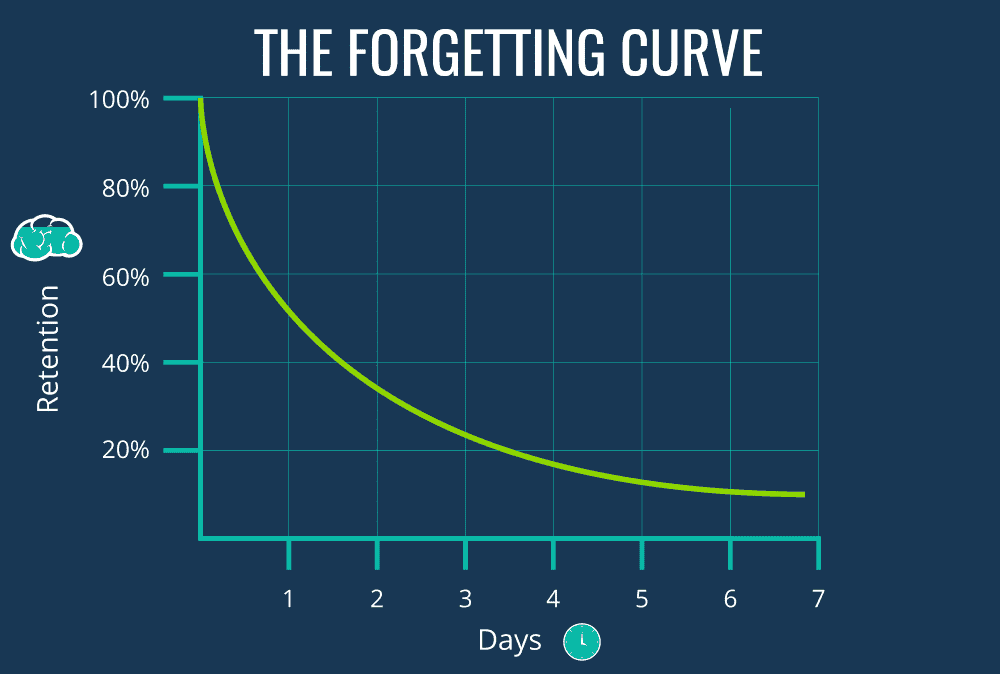
The “forgetting curve” explains why learning is hard (Source: growthengineering.co.uk)
Once the awareness session is delivered, we found that a follow-up phishing simulation exercise is an effective way to measure the success of the course. The results are usually staggering, as we typically see a massive drop in the number of people tricked by our fake email versus the numbers before the training. Similarly, you can demonstrate the value of your efforts with a follow-up phishing simulation campaign.
Also, you can solidify good security practices by rewarding staff. For example, employees reporting phishing emails to your IT department within the first two weeks should have a chance to win an Amazon gift card. With little incentives like this, you have the best chance of keeping the awareness levels of staff up after training.

Everyone loves free gifts (Source: cnet.com)
In addition, the security awareness training sessions should be repeated on a regular basis as the positive effects fade away over time. Also, phishing simulation campaigns should be a routine exercise (beside the follow-up exercise) to:
- keep a general level of security awareness and vigilance;
- identify new employees (e.g. new hires, contractors, vendors) with challenges to withstand social engineering attempts;
- identify existing members of staff who may require further education; and
- raise staff awareness of new types of phishing emails they are likely to receive.
Finally, share your slides within your organisation and encourage everyone to use them as a reference guide. If you have the time, you can even write the slides up as an article for the company intranet, which makes your content more accessible for those who could not attend.
Conclusion
The cybersecurity challenges of today require three key elements be addressed: people, process and technology. Your last defence line when it comes to social engineering is people. Hence, a security awareness training program is an integral part of your cybersecurity efforts. In our experience we recommend:
- face-to-face classroom training where possible;
- make the content relatable and use examples of actual phishing emails your organisation has received;
- encourage positive security practices at home as well as the office; and
- validate the effectiveness with phishing simulation before and after classroom training.
About the Writers
This article was co-written with Nicholas Kavadias and first published on the Iron Bastion Security Blog. Iron Bastion is a cybersecurity company offering phishing awareness training services. We provide a range of services protecting Australian businesses from cyber criminals and digital threats.