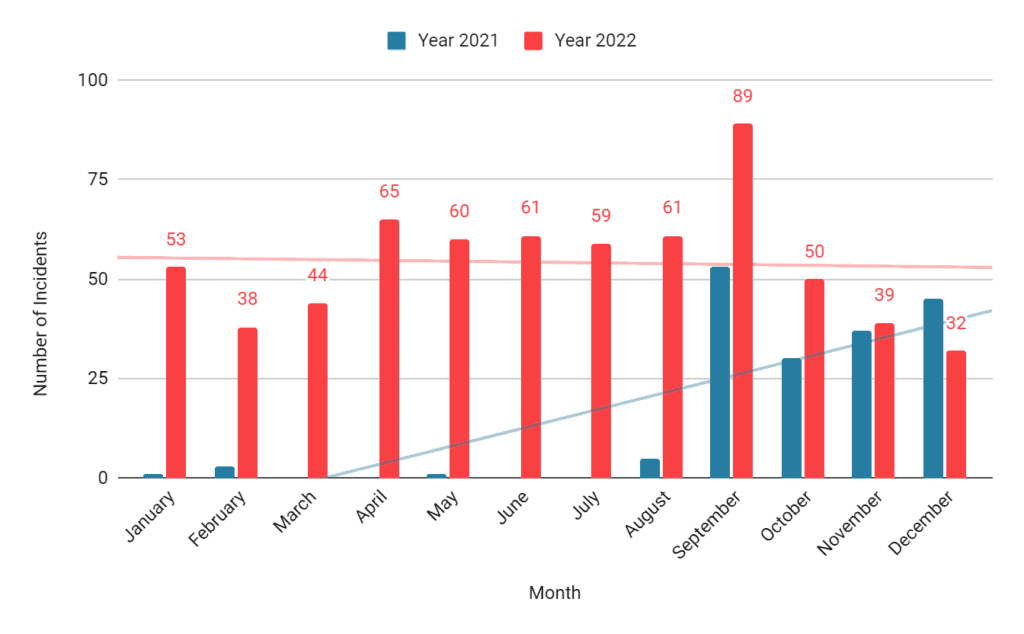
BENGALURU: Data gathered by CloudSEK’s contextual AI digital risk platform XVigil show that the number of attacks targeting the government sector has increased by 95%* in the second half of 2022, as compared to the same period in 2021.
India, USA, Indonesia, and China continued to be the most targeted countries in the past two years. Together these four countries accounted for ~40% of the total reported incidents in the government sector. There are three interesting findings observed in the variations in the number of attacks from 2021 to 2022.
Number of cyber incidents targeting the government sector recorded in the past two years
*Note: The insights and distribution of threats by region are contingent on the presence of our clients in those regions.
China Emerges As The Most Targeted Country In 2021
The significant hike observed in the number of attacks targeting the Chinese government can be attributed to APT groups. Almost 96% of attacks against China were initiated by the AgainstTheWest threat group under their campaign Operation Renminbi which began as retaliation to China’s activities against Taiwan and the Uyghur community. It is also speculated that conspiracy theories about China being responsible for the outbreak of COVID-19 may have contributed to the increase in attacks. (For more information check the full report).
“XVigil data indicates that the number of attacks targeting the government sector has increased by 95% in the second half of 2022, as compared to the same period in 2021. About 40% of this growth is attributed to India, USA, Indonesia and China; which remained the top most targeted countries in both the years,” said a CloudSEK researcher.
More Than Double Attacks Against India Making It Most Targeted Country in 2022
In 2022, attacks on the Indian government intensified to the point where it became the country that was most frequently targeted in this sector. This expansion is the result of the hacktivist group Dragon Force Malaysia’s #OpIndia and #OpsPatuk campaigns. Numerous hacktivist groups joined and supported these campaigns, which laid the path for subsequent ones. However, this increase has other causes besides the growing hacktivism. Government agencies in India have become popular targets for extensive phishing campaigns.
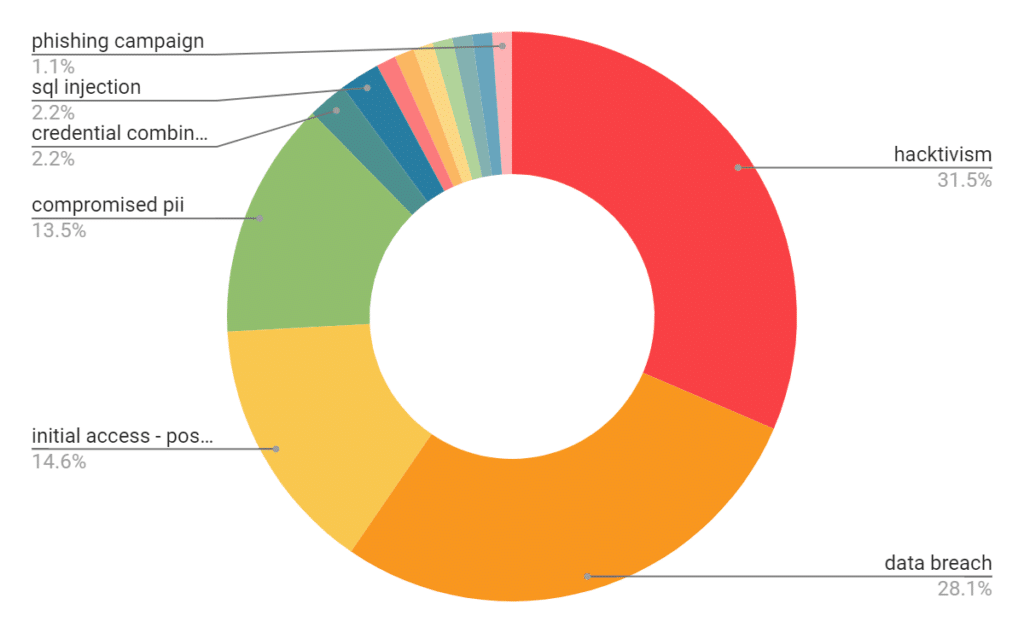
Threat actors’ favoured attack vector against India in 2022
Sudden Spike in Attacks on Russia
Attacks on Russia went up by over 600% owing to the ongoing Russia-Ukraine war. Russia’s sudden invasion on Ukraine fueled the fire between the two countries and eventually led to a global change in the political sphere. Both governments and hacktivists from different countries started showing their support for Ukraine by targeting Russia, thus converting it into a widespread cyber war.
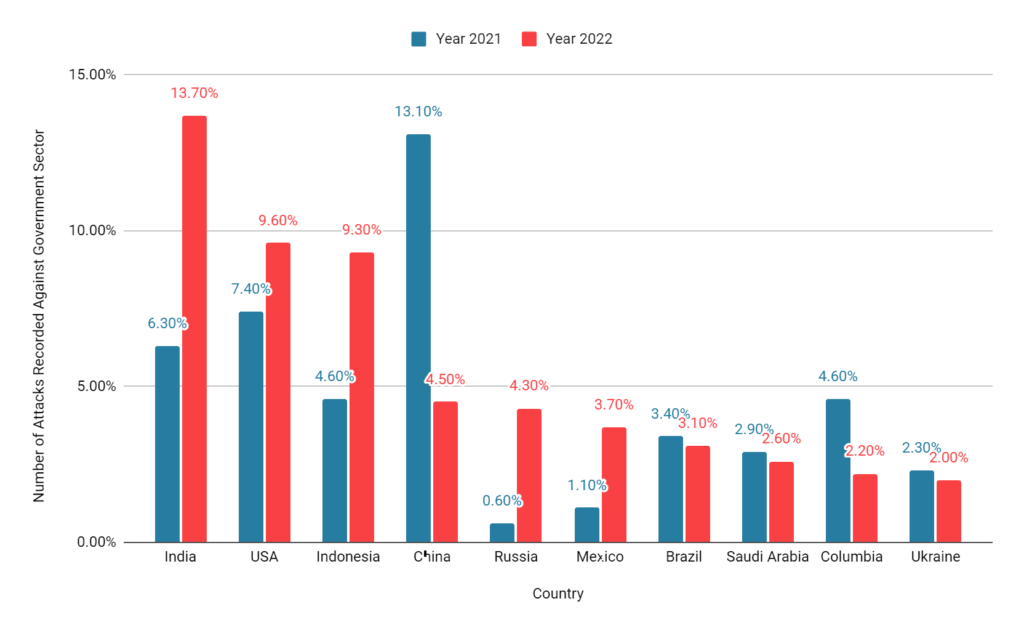
10 most targeted countries in the government sector in 2022
Motives & Factors Behind Attacks
The primary motive of most of the threat actors is exfiltrating data and selling it for monetary benefits, yet it is not the only reason they target governments. This change is clearly evident from the emergence of various APT groups and hacktivist campaigns over the last decade.
The year 2022 saw a significant increase in hacktivist activity accounting for about 9% of the recorded incidents reported in the government sector. These statistics are clearly suggestive of the fact that cyberattacks in this particular industry are no longer limited to financial gains; rather, they are now used as a means of expressing support or opposition for a certain political, religious, or even economic goal.
Ransomware groups were also very active in this industry accounting for 6% of the total incidents reported, with LockBIT as the most prominent ransomware operator.
While a majority of attacks were essentially on the same old theme, focused on compromised data and access, there were also a few attacks conducted to help highlight the various flaws in the country’s security posture and help improve it. A series of such attacks was observed against Indonesia. The ratio of government-sponsored attacks has also multiplied; however, there is no exact figure for this increase since these attacks are mostly untraceable. This growth can be primarily attributed to the advent of RaaS models. Threat actors have started developing and advertising services of dedicated criminal infrastructure which can be bought by the government (or individuals) and used for various nefarious purposes.
Prominent Threat Actors
Given the various ups and downs faced by this sector, it is intriguing to note that the top two threat actors targeting this industry have remained the same in 2021 and 2022.
KelvinSecurity: Mostly seen operating under the handle Kristina this group is in the top two actors in both the years 2021 and 2022. The group uses targeted fuzzing and exploits common vulnerabilities to target victims. Being highly skilled in the use of tools and having a wide knowledge of various exploits, they share their list of tools and payloads for free. (For more information check the full report)
AgainstTheWest: Emerged in October 2021, this group identifies itself as an APT49 operator. They have been highly focused on exfiltrating region-specific data and selling it on the dark web. Based on their previous activity they appear sophisticated, skilled, and organized. The group has been targeting various countries under different campaigns including Operation Renminbi, Operation Ruble, Operation EUSec, etc. The group has been constantly exploiting a common set of vulnerabilities and exploits to target multiple countries.
About CloudSEK
CloudSEK is a contextual AI company that predicts Cyber Threats.
At CloudSEK, we combine the power of Cyber Intelligence, Brand Monitoring, Attack Surface Monitoring, Infrastructure Monitoring and Supply chain to give context to our customers’ digital risks.
To learn more about CloudSEK, visit https://cloudsek.com/.
Media Contact:
Shashank Shekhar
+91-9811379924




