Flashpoint has published its July Cyber Threat Intelligence Index which shows Australia was in the top 10 countries for ransomware attacks last month.
Ransomware
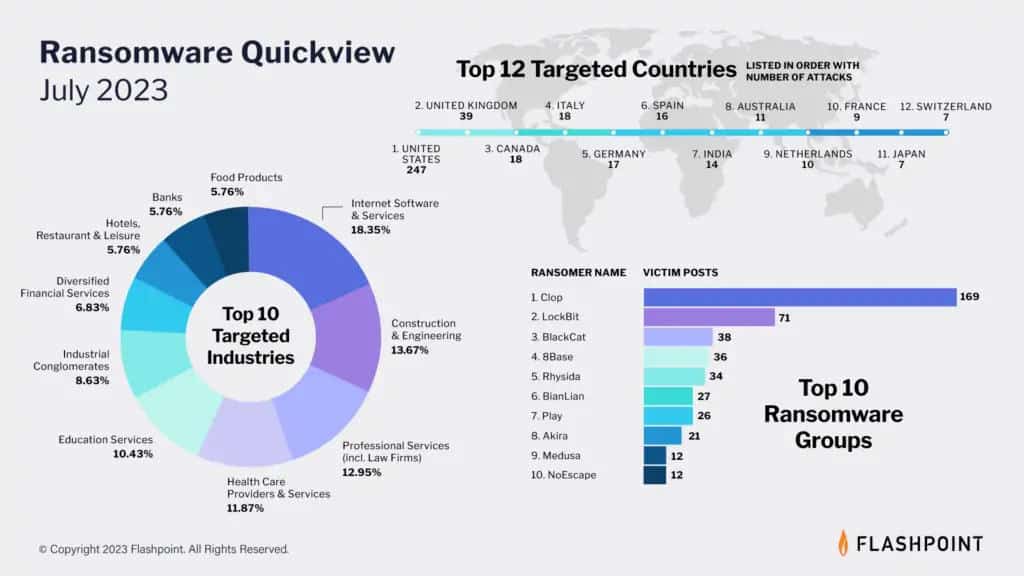
Flashpoint’s latest ransomware infographic paints a sobering picture of the evolving threat landscape, with cybercriminals employing increasingly sophisticated tactics. In July, Flashpoint recorded a total of 515 ransomware attacks.
Clop was the most prolific ransomware group, being responsible for nearly 33 per cent of July’s recorded ransomware attacks. The United States experienced the most ransomware events, accounting for 48 per cent of all July’s recorded ransomware attacks, while Australia ranked eighth. Internet Software and Services continues to be the most targeted industry, followed by Construction & Engineering, and Professional Services.
“We’re consistently still seeing Australia among the most targeted countries in the world for ransomware attacks,” said Ben Gestier, Senior Intelligence Analyst and Team Lead APAC/EMEA, Flashpoint. “Safeguarding company assets from ransomwares is crucial for Australian businesses, who should all implement or constantly update their own threat readiness and response plans in order to prevent loss, service disruptions, and lasting damage.”
Vulnerability Intelligence
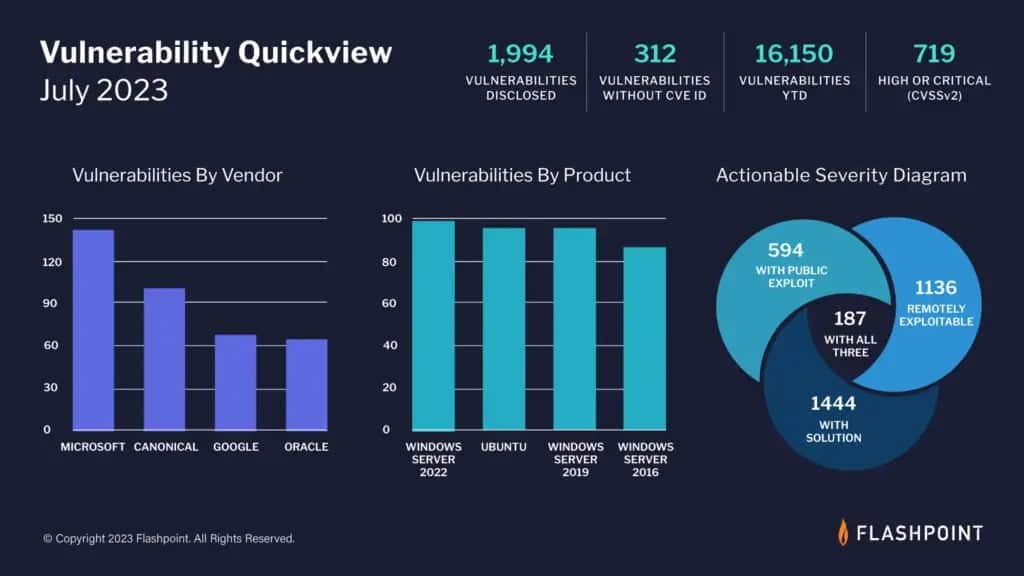
1,994 new vulnerabilities were reported in July, with 312 of them being missed by the Common Vulnerabilities and Exposures (CVE) and National Vulnerability Database (NVD).
36 per cent of July’s disclosed vulnerabilities are rated high-to-critical in severity. If exploited, these issues could pose a significant security risk. Over 56 per cent of last month’s vulnerabilities are remotely exploitable. This means that if leveraged, threat actors can execute malicious code no matter where the device is located.
Vulnerability Management teams can potentially lessen workloads by 90 per cent by focusing on actionable, high severity vulnerabilities. This classification is given to vulnerabilities that are remotely exploitable, that have a public exploit, and a viable solution.
Data Breaches
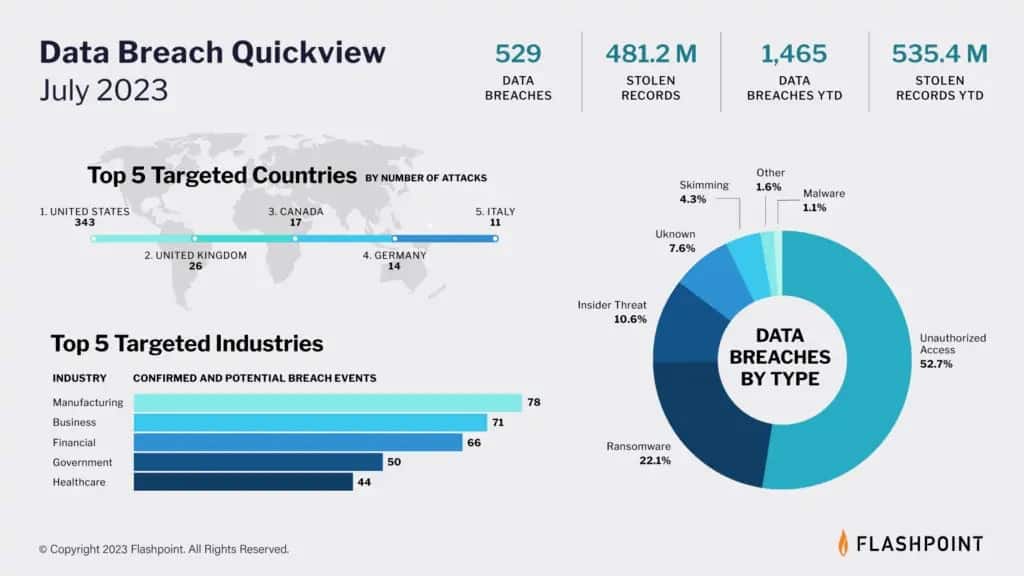
Studying breach events can help CISOs and security teams better understand the goals and motivations of threat actors. In July, Flashpoint recorded 529 data breach events and threat actors stole a total of 481.2 million records.
Organisations in the United States accounted for more than 64 per cent of July’s recorded data breaches. Unauthorised access, or hacking was the leading cause of data breaches in July, being responsible for over half of recorded data breach events.
Malware
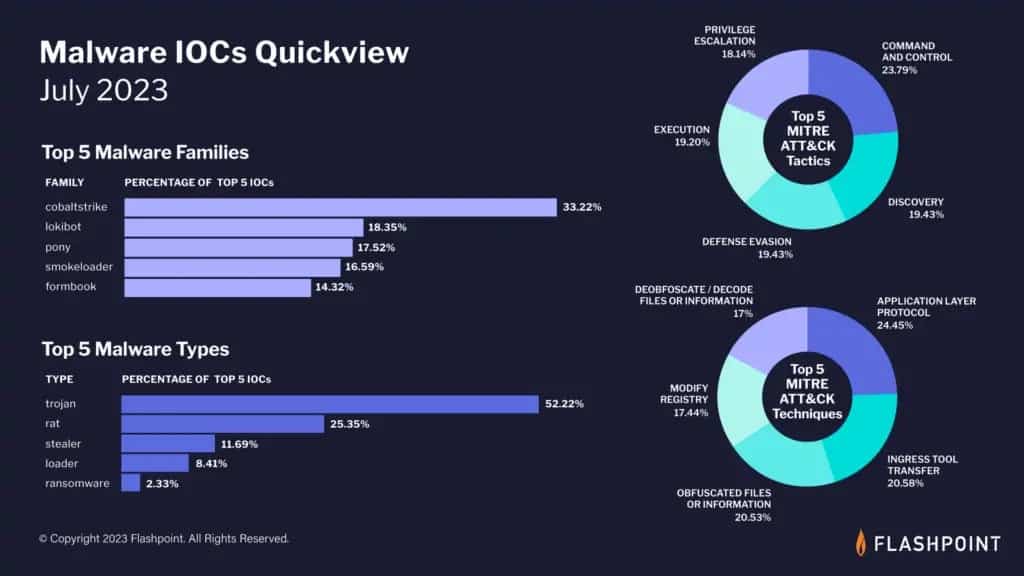
Flashpoint has looked at the latest malware trends: which types of malware threat actors favour, how they get access into a victim’s systems, and what cybercriminals do once they gain a foothold.
Trojans were the most widely used malware type in July’s recorded cyberattacks. In particular, the cobaltstrike malware family accounted for 33.22 per cent of July’s top five indicators of compromise. The most favoured MITRE ATT&CK tactic was Command and Control.
Insider Threat
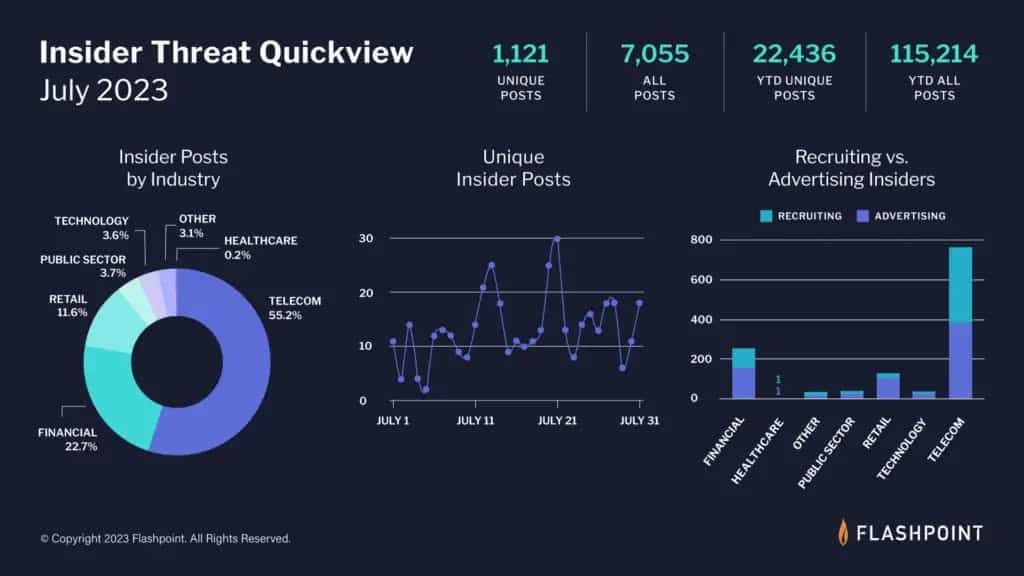
The tactic of recruiting insiders has become immensely popular amongst threat actors aiming to breach systems and/or commit ransomware attacks.
In July, Flashpoint analysts collected 7,055 posts advertising insider services – both from threat actors seeking insiders and malicious employees offering their services. Of those, 1,121 were unique posts from individuals in illicit and underground communities.
The Telecom, Financial, and Retail industries were the most targeted sectors for insider threats in July. The majority of insider threat related postings originated from insiders advertising their services to outside threat actors. Most of this activity came from the Telecom sector.




