A major cyber threat to Australian businesses is email-based impersonation scams targeting key personnel. The scheme involves cybercriminals mimicking business owners and executives through the use of phishing emails. Criminals typically pose as personnel in positions of authority and ask victims to perform money transfers, pay invoices, or to send the attacker sensitive data.
The ACCC’s Scamwatch reveals that Australians reported over $4.7 million in losses caused by impersonation attacks in 2017, and estimates that 2,800 Australians were tricked into giving up personal information. In the same year, Mimecast reported that impersonation attacks were the fastest growing email-based cyber attack causing victims to lose on average $180,000. The good news is that you or your IT staff can take some simple (and free) measures to protect your business from email-based impersonation attacks. This article explains why and how.
Impersonation Attacks Rely on Email Spoofing
Email spoofing is when an attacker (cybercriminal) forges an email so that it appears the email has been sent by someone else. This is either done so that the entire name and email address of the sender is a forgery, or in more straightforward cases, just the name of the sender.
The typical intention of the attacker is tricking their victims into:
- making money transfers, or paying fake invoices to defraud your business;
- sending back sensitive data related to your business or your clients;
- clicking on hyperlinks to take over the victims computer and/or steal user credentials to facilitate fraud in what is called a BEC (Business Email Compromise) attack; or
- opening a file attachment to install ransomware on the victim’s computer to encrypt all files on the victim’s internal network and hold them for a ransom.
Email Is an Insecure Service by Default
The core email protocols used by email were developed in the 1980s when abuse was not an issue like it is today. Back then, the internet was a quaint and friendly place. Email servers were explicitly configured as open relays meaning they allowed anyone connecting to them to send emails to anywhere. This common practice was abandoned years later when spammers and criminals began exploiting open relays.

A user dials up an online connection before sending an email in 1984 (Source: ThamesTV)
This legacy of permissive design in email protocols why email spoofing is quite simple to do. Email services by default are not capable of identifying and blocking deceptive emails with a forged sender name or email address, which leaves businesses vulnerable to impersonation cyber attacks.
For example, the following email was intercepted by our anti-phishing services. The attacker was attempting to scam our client by tricking them into making a financial transfer to their bank account. Interestingly, the criminal knew which employee in the business was responsible for managing payments, and targeted her specifically.
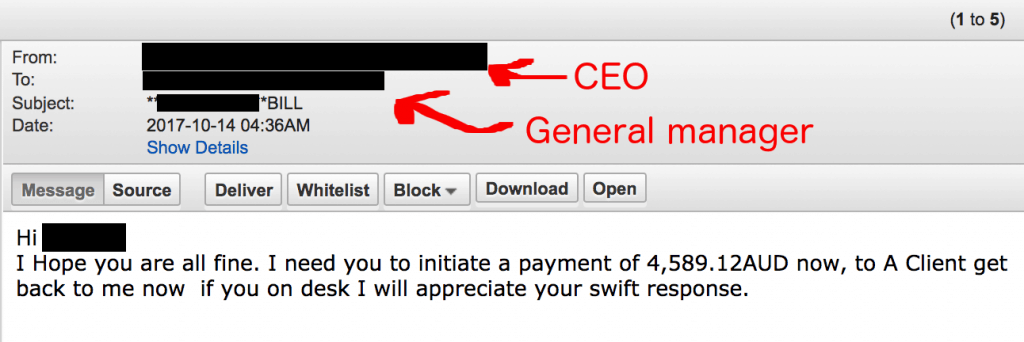
The Mechanisms of Email Spoofing
There are two common impersonation methods frequently used by cybercriminals. For illustrative purposes, let us say our person in a position of authority we wish to impersonate is Saul Goodman, and his email address is [email protected]:
- Method #1 – Email Address Spoofing: Saul’s email address and his name are spoofed on an incoming email so that the sender appears to be:
Saul Goodman <[email protected]>. - Method #2 – Display Name Spoofing: Only Saul’s name is spoofed, but not the email address:
Saul Goodman <[email protected]>.
With the availability of web-based free email, Method #2 is a very simple and low-tech attack to carry out. An attacker finds out the name of a person in your business who is in a position of authority and then signs up to a free email service such as Gmail, Outlook.com or Yahoo Mail using their name. The attacker then uses publicly available information on your business from sources such as LinkedIn, or your business website to target people in your organisation.
On the positive side, your IT staff can make a few simple changes to your email service to protect your business from both Method #1 and #2 above.
The following two sections feature detailed instructions which make changes to your mail service so that your business can help identify and block spoofed emails and help prevent impersonation attacks. The instructions are written with a technical audience in mind. If this is not you, we recommend you send this article to your IT staff, or contractor responsible for your email service and ask them to implement the changes below.
Preventing Email Address Spoofing (Method #1) With a Ten Minute Effort
Did you know that every email has two different senders? One email address is called the ‘envelope sender’, and the other is set in the email header. The latter is known as the ‘From:’ header, which is normally displayed by the email clients, like Microsoft Outlook. Unfortunately, cybercriminals can forge the ‘From:’ header to trick email clients into displaying a name and email address which belong to your business.
You or your IT staff can make changes to your email service settings to help block deceptive emails coming into your organisation, and put other email services on notice as to what a legitimate email coming from you should look like. This is done by adding what is known as SPF, DKIM and DMARC DNS records to your company’s domain name.
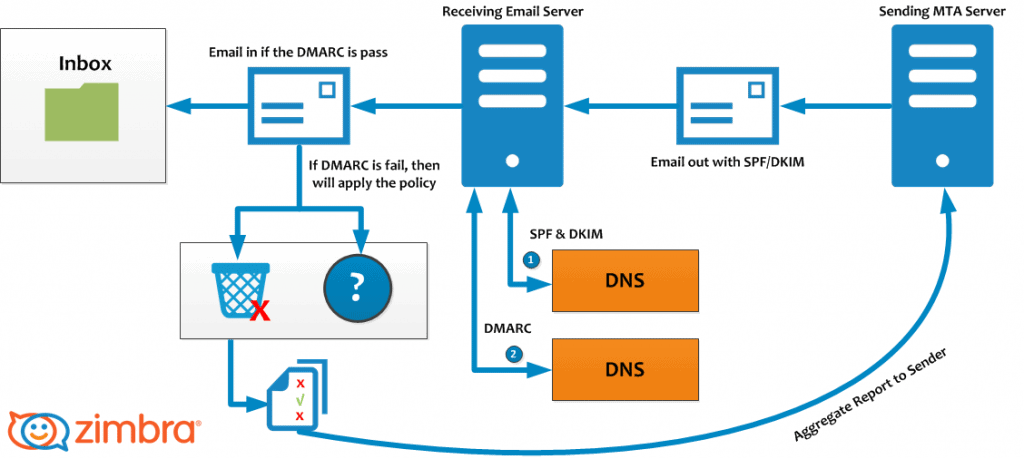
The Three DNS Records That Combat Email Address Spoofing
Adding SPF, DKIM and DMARC to a business’s domain name record is not as complicated as it sounds. In cases where your business uses Office 365 or G Suite you only need to follow the instructions set out below for your mail provider.
Creating an SPF record:
Creating a DKIM record:
Remember what we said about email having email sender addresses? We have yet to create one final record: DMARC. Contrary to popular belief, SPF alone cannot prevent spoofing. Without the DMARC record, cybercriminals can still forge the email address of your business as SPF is only verified against the invisible ‘envelope sender’, but not the ‘From:’ header. In other words, the criminals can spoof the sender’s email address, and it will still pass the SPF checks – and this is why you need the DMARC record.
You can use an online DMARC generator to craft the perfect DMARC record for your organisation, or you can just take our word for it and add the following DNS record to your company’s DNS. It is by no means perfect, but it is a great start:
_dmarc.mycompany.com.au. 3600 IN TXT "v=DMARC1; p=quarantine; pct=100;"
Congratulations, time to reward yourself with a nice cup of tea. If you have created all three records, emails from your domain with a forged sender will go straight into peoples junk email folder from now on. That is for your own email service, and any other email service which use DMARC. If you want to be harsher about how to treat emails with forged senders, then you should investigate setting DMARC to ‘p=reject’.

How to Combat Display Name Spoofing (Method #2)
Although Display Name Spoofing is a less sophisticated technique than email spoofing, it is much more dangerous. Because the sender’s email address is not forged per se, it is more difficult to block emails with forged display names as opposed to the first scenario, where the mere addition of three simple DNS records was sufficient to stop spoofed emails.
With Method #2 cybercriminals simply register a new email address with a free email provider using the same name as an executive from your organisation (e.g. Saul Goodman <[email protected]>). Technically, the email address is valid, so emails sent from these accounts will slip through anti-spam filtering. Similarly, the SPF/DKIM/DMARC records will not block these phishing emails either, because the email address is not forged.

Display Name Spoofing attacks are not stopped by regular anti-spam filter
As a result, the first and last line of defence is your employees. They need to be vigilant and be prepared to identify emails using the Display Name Spoofing technique. Sadly, this is prone to human error as your employees may not verify the full details of every single incoming email under certain circumstances – like in stressful situations such as fast-approaching deadlines or lack of attention to detail.
Also, employees may believe that because the email looks like it has come from someone they are familiar with and with the standard company email signature signoff from that person, that the email is legitimate. Unfortunately, attackers can also use the same email signatures at the bottom of emails sign-offs as legitimate senders.
To add insult to injury, many email clients – especially smartphone email clients – only display the sender’s name by default, but not the email address. For example, the Mail app on the iPhone requires you to tap on the sender’s name to reveal an email address.
Employees should be trained to identify deceptive emails with the forged display names and should receive as many visual aids as possible to detect if something is off. Luckily, Office 365 and G Suite can be configured to help combat display name spoofing by providing employees with visual clues.
Adding Visual Clues to External Email in Office 365
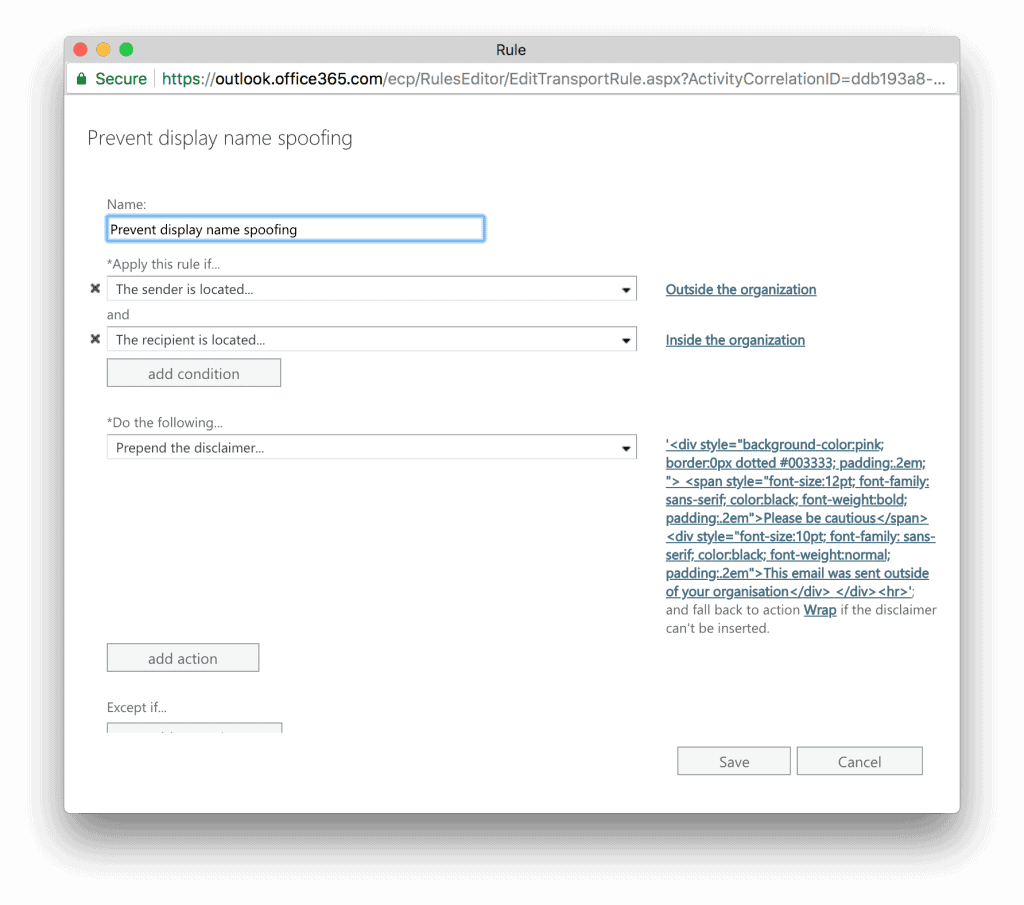
With Office 365, we can inject highly-visible warning banners at the top of messages if they were sent from an email address external to your business. The aim is to provide a visual warning to your employees when an email was not sent from someone within your organisation.
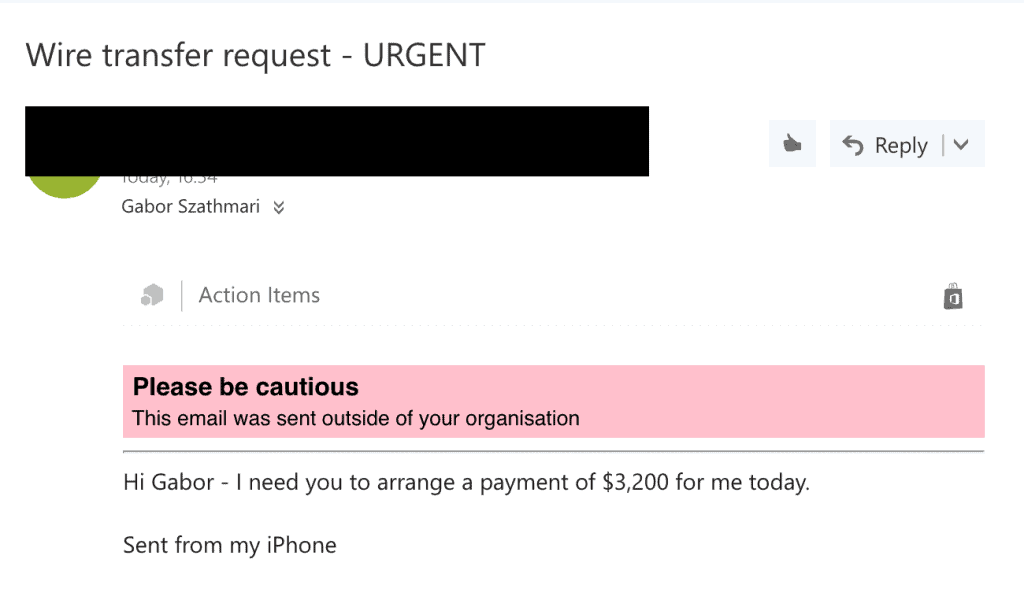
An external email with a highly-visible warning label
To turn the warning banners on, visit the Office 365 Exchange Admin Center on https://outlook.office365.com/ecp, and navigate to mail flow -> rules.
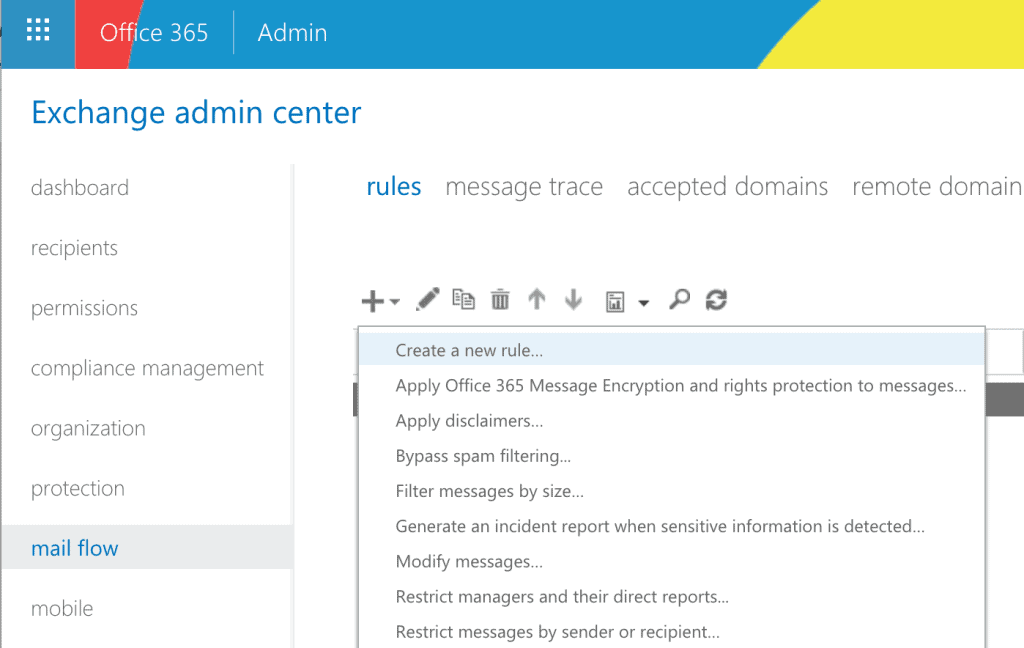
Click on the ‘+’ sign then select ‘Create a new rule…’. In the popup window, choose ‘The sender is located’: ‘Outside the organization’, and ‘The recipient is located’: ‘Inside the organization’. Under the ‘Do the following’, choose ‘Apply a disclaimer to the message’ -> ‘prepend a disclaimer’ and insert the following piece of code:
<div style="background-color:pink; border:0px dotted #003333; padding:.2em; ">
<span style="font-size:12pt; font-family: sans-serif; color:black; font-weight:bold; padding:.2em">Please be cautious</span>
<div style="font-size:10pt; font-family: sans-serif; color:black; font-weight:normal; padding:.2em">This email was sent outside of your organisation</div>
</div>
<hr>
The fallback action should be ‘Wrap’. Click on ‘Save’ and wait for a few minutes for the rule to activate.
G Suite Settings for Flagging External Emails
Although G Suite too can inject highly-visible warning banners like Office 365, the service offers a somewhat more sophisticated technique to combat Display Name Spoofing.
The first setting we recommend is turning on is the external recipient reply warning. This option adds a warning at the top of an email in the Gmail web interface if we attempt to reply to a message from someone outside of our organisation.
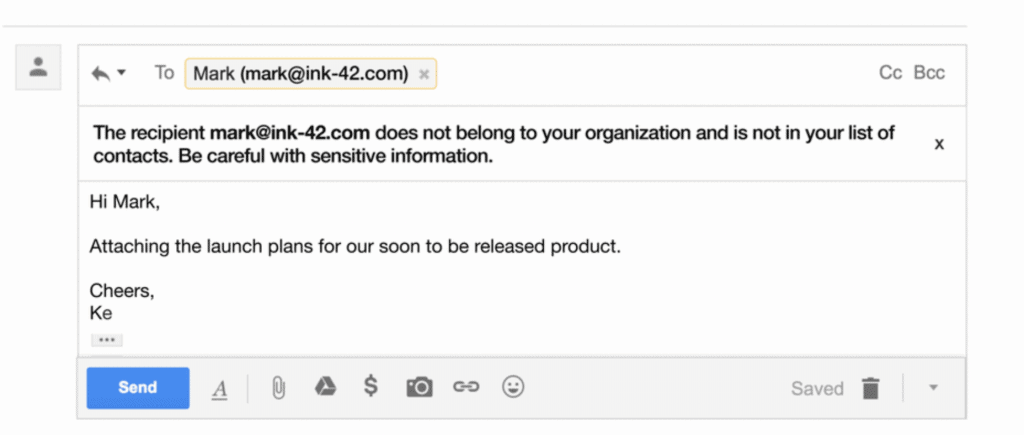
Banner warning us that the recipient is not part of the organisation
A more exciting feature though is one of the new G Suite anti-phishing and malware settings that Google has rolled out recently. This feature can display warning banners against emails that try to spoof employee names, or come from a domain that looks similar to your business’s domain name.
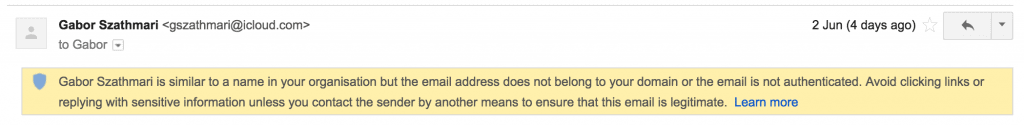
Warning banner added by G Suite’s new Safety settings
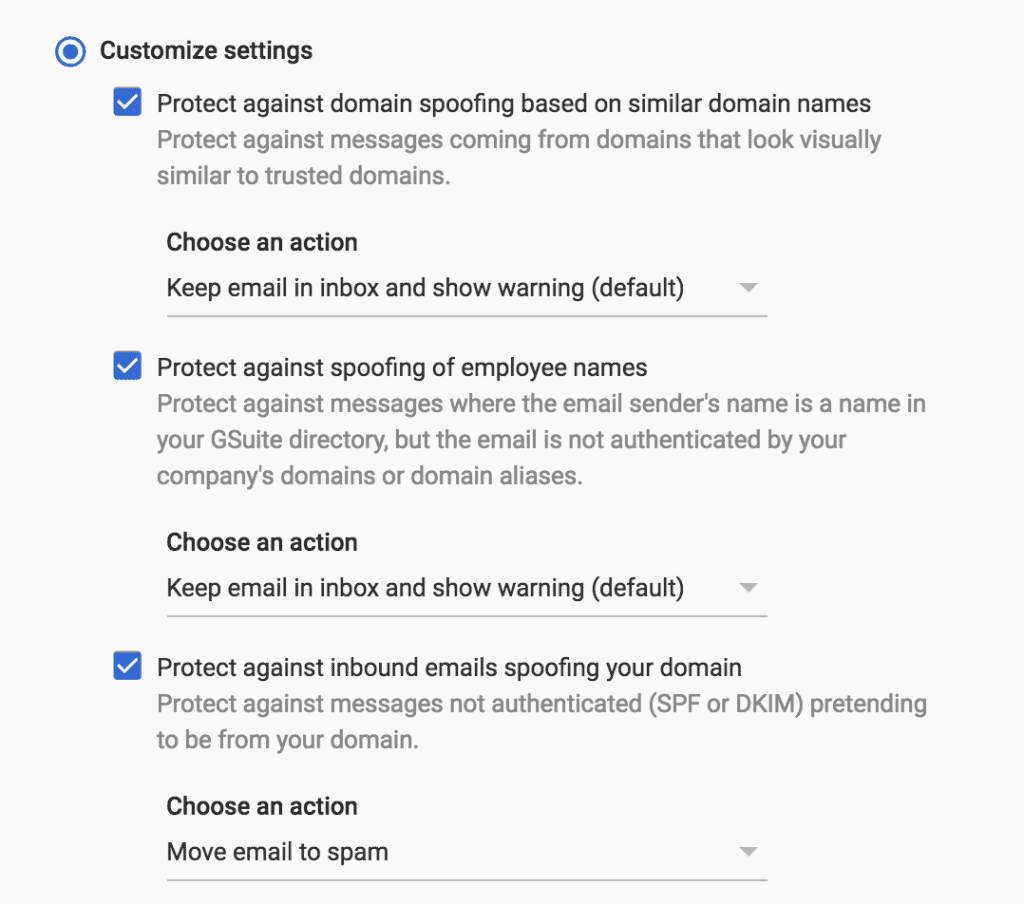
To turn on this setting, go to the G Suite Admin Portal (https://admin.google.com/) and navigate to Apps -> G Suite -> Gmail. Then scroll down to the Safety section and expand it. Go to the Spoofing and authentication section and turn on the followings:
- Protect against domain spoofing based on similar domain names
- Protect against spoofing of employee names
- Protect against inbound emails spoofing your domain (covers the first scenario)
Keep in mind that warning banners will only appear when using the webmail interface. Your employees will not receive any visual clues if they are accessing their mailbox with a classic email client such as Microsoft Outlook. Hence we recommend altering the subject line of the incoming emails as well in case emails are sent from the outside of your organisation.
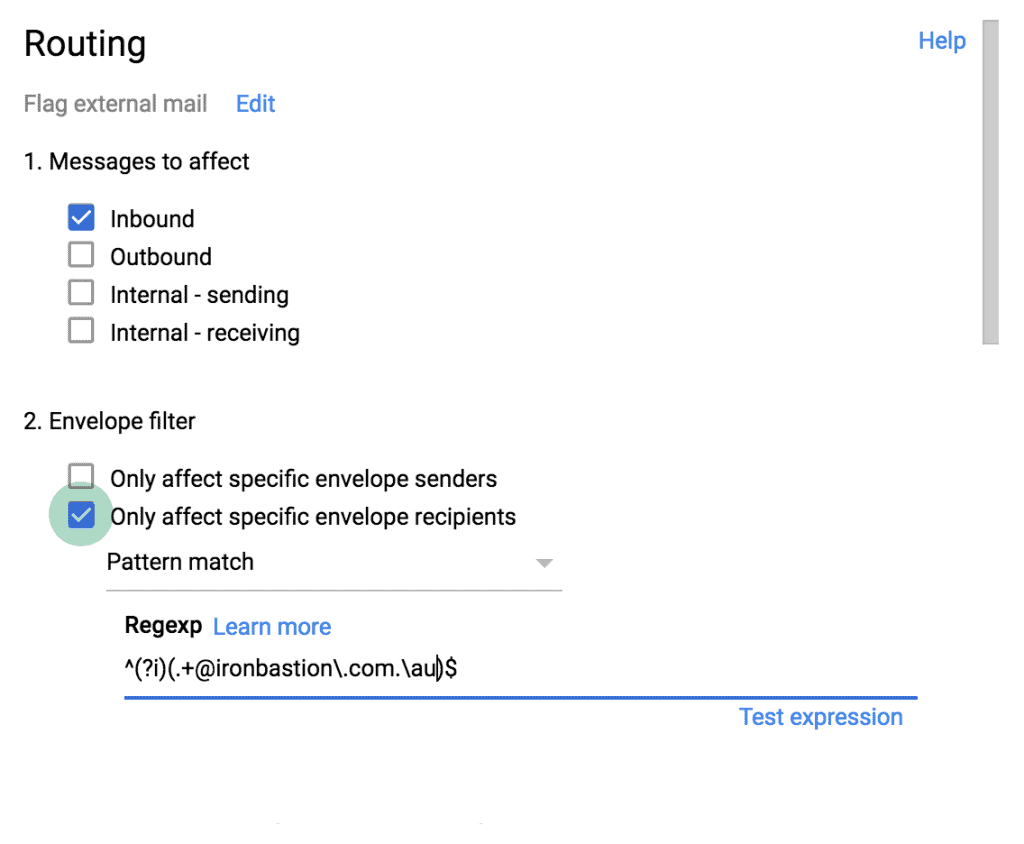
To change the subject lines of incoming emails, go to Apps -> G Suite -> Gmail -> Advanced Settings on the Admin Portal again. Scroll down to Routing and add a new entry as the following. Choose ‘Incoming’ under ‘Messages to affect’. Pick ‘Only affect specific envelope senders’ and select ‘Pattern match’ from the drop-down menu. Enter ^(?i)(.+@yourdomain\.com.\.au)$ into the regexp field.
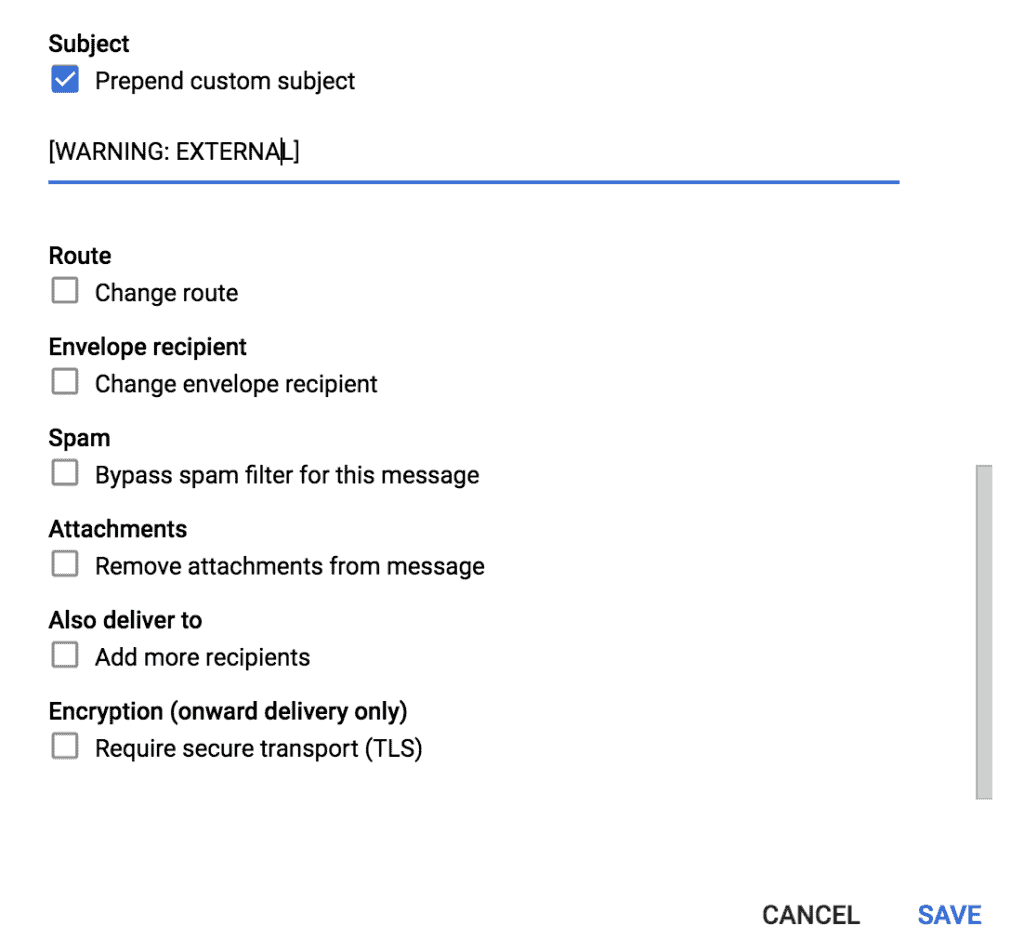
 Finally, scroll down near the bottom and pick ‘Prepend custom subject’ to add your preferred warning label, then click Save.
Finally, scroll down near the bottom and pick ‘Prepend custom subject’ to add your preferred warning label, then click Save.
Voilá! The subject line of the external emails will now feature a warning prefix.
Using Anti-phishing Services to Detect Email Spoofing
The third option to combat impersonation attacks (both Email Address Spoofing and Display Name Spoofing) is pre-screening your incoming emails using anti-phishing services. These services feature technologies that are specifically designed to protect organisations from phishing threats including Email Address Spoofing and Display Name Spoofing attacks.
Why Anti-Phishing Services Are Superior
Anti-phishing services can meticulously analyse the entire content of the inbound emails looking for any red flag indicating a phishing attempt, such as typical wording and text semantics, invalid digital signatures, and poor sender reputation. The built-in anti-phishing algorithms are supported by Machine Learning, Artificial Intelligence (AI) and Threat Intelligence Networks. Secondly, file attachments are also analysed in safe environments for known and unknown threats, and embedded hyperlinks are modified to perform real-time analysis (and block) any malicious URL when the recipient clicks on them.

Anti-phishing services are effective in protecting your business from email spoofing attacks
Anti-phishing services are compatible with all email service providers. No matter if your firm is using G Suite, Office 365, on-premise Microsoft Exchange or an email platform provided by your IT service provider, anti-phishing services can seamlessly integrate with any of them. If you are interested in the types of anti-phishing services the top 100 law firms are using in Australia, please refer to our research article on the subject.
Summary
Email Address Spoofing and Sender Name Spoofing are techniques that cybercriminals rely on in email-based impersonation attacks. The goal of these scams is to deceive personnel in an organisation and trick them into making payments or sending sensitive information to an attacker. Due to the design decisions made in the 1980s, email cannot guarantee the authenticity of the sender. Various practices are used by criminals to falsify the sender of an email, and each of them needs to be dealt with differently. While a simple change to a business’s DNS to include SPF, DKIM and DMARC records can combat Email Address Spoofing attempts, Display Name Spoofing attacks require you to train employees to be more vigilant. Visual clues can be added to incoming emails to warn employees when an email has not come from someone internally. In addition, anti-phishing services can screen emails for phishing using advanced technologies to minimise your organisation’s risk of becoming a phishing victim.
* * *
This article has first appeared on the Iron Bastion Security Blog and was co-written with Nicholas Kavadias.



