Only 3% of Australian organisations claim to be ‘mature’ in their cybersecurity stance, according to Cisco’s 2025 Cybersecurity Readiness Index report. Seventy-five percent expect a major business disruption within two years due to a cyber incident.
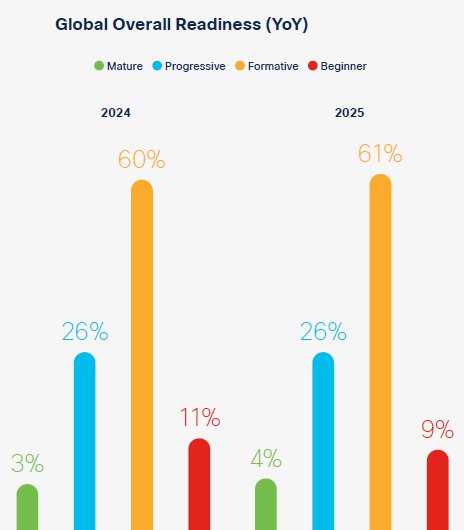
Global Readinesss Index Percentages
From 8000 companies across 30 countries, only ~3% rate themselves as mature. CTO of ANZ at Cisco, who joined me in an interview from Perth, was ready to dissect not just the report, but the realities around its percentages.
“It’s not the 75% that alarms me, it’s the other 25%,” Solder said flatly. That is, one in four organisations here don’t even recognise they’re at risk. They’re not preparing for the inevitable.
…It’s not a case of if, it’s more a case of when.”
The Cyber Readiness Index isn’t just a rudimentary assessment. According to Cisco’s insight across 8,000 businesses in 30 countries, over 300 are from Australia.
The survey is designed around two pillars:
- A temperature check of how businesses perceive their digital peril
- A self-assessment against five core domains, identity, machine, network, cloud, and now, artificial intelligence.
From this, organisations are sorted into four tiers:
- Beginner
- Formative
- Progressive
- Mature
In conversations with security and IT practitioners, Solder admitted that landing in the ‘progressive’ camp is already cause for quiet celebration.
“There’s very few companies I’ve met who actually consider themselves in a position to be mature where they could thwart every single kind of attack… They’ve just got to find one area where they can slip in,” he added.
Comparing year-on-year AI Readiness Index results, the report went on to say it didn’t improve, and actually receded.

Carl Solder, CTO of ANZ at Cisco
Eight in ten organisations Cisco surveyed suffered an AI-related security incident last year. Yet the nature of these attacks is not what you’d typically expect.
“At this point in time, threat actors are not necessarily using AI to craft or invent new forms of compromise” Solder pointed out. “What they’re doing is using AI to augment or to make their existing forms of compromise more effective.”
Phishing emails are now indistinguishable from official correspondence, not just for the C-suite, but for anyone with a login. AI helps attackers fly under the radar, and defenders have no choice but to enlist AI themselves, fighting algorithm with algorithm.
Is this a sustainable strategy? The short answer is no.
“The pace of innovation is moving at breaking speeds,” Solder admitted, describing the effect as both familiar and uncharted. Security teams automate and respond, AI models learn, malware improves, new defensive layers pile atop old ones. In this arena, Solder says, “It just takes one individual” to click the wrong link… and the cascade begins.
While awareness campaigns and simulated phishing tests have increased employees’ baseline savvy, only about half of organisations (46%) feel their staff truly understands AI-driven threats. That leaves the rest vulnerable to what Solder calls, “the weakest link in the cyber defence.”

Karissa Breen, Head of Journalism at KBI.Media
Training programs help, but awareness is not static. “Because the cyber threat landscape is continually evolving, you can’t stand still,” Solder warned. The challenge isn’t just understanding where attacks might come from, but realising you don’t even know what you don’t know, especially as AI becomes less a buzzword and more a tool for misdirection and subversion.
Even the best tools become liabilities in excess. Half of organisations hit by a cyber incident last year struggled with complexity, including patchwork security frameworks, too many point solutions, and data scattered across dozens of vendor products.
One customer, Solder mentioned, informed him that they juggled security software from seventy vendors. This is quite common in many organisations and what we call ‘tool sprawl’.
The result? Paralysis. “It was really difficult…to correlate if an attack or a compromise is in progress.”
Industry consensus is shifting towards platformisation, which is to reduce that tool sprawl. The move toward unified, integrated security platforms. It’s about building a ‘singular unified portal’ or conversely known as ‘single pane of glass’ that can correlate incidents quickly and provide actionable visibility.
If these problems seem solvable, why aren’t organisations attacking them with urgency? Nearly all intend to overhaul their IT infrastructure, yet less than half dedicate even 10% of IT budgets to security.
“Every company…is under cost pressures. It’s all about doing more with less,” Solder reflected. Until a major breach happens, security can feel like insurance, not investment. But when the inevitable occurs, the money appears. The question is how many businesses have to learn this the hard way.
It’s about anticipating the ones that still exist only in theory, such as quantum computing’s potential to shatter encryption as we know it. “Not a lot of companies need to be worried about now, but certainly need to be cognisant of it,” Solder cautioned. Post-quantum cryptography is already gaining traction amongst governments, industry, and media.
At the end of the day, keep your organisation’s basics on point which include: patch, educate, upgrade. And don’t mistake fleeting confidence for real preparation.








