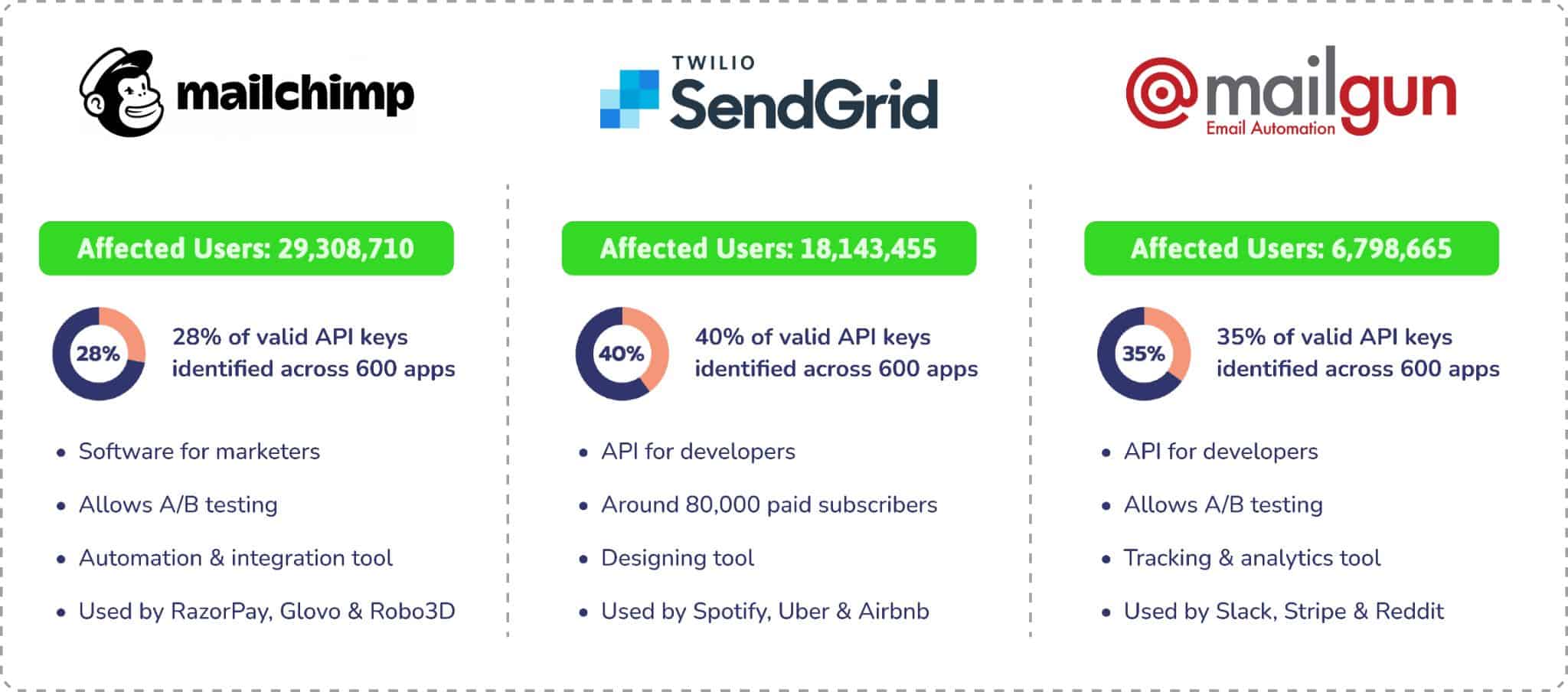
CloudSEK’s BeVigil, the world’s first security search engine for mobile apps, uncovered about 50% of the analyzed (600) apps on the Google play store, leaking API keys of three popular transactional and marketing email service providers; Mailgun, MailChimp, and Sendgrid.
Key Findings
- The USA was the country with the highest number of downloads followed by the UK, Spain, Russia, and India, leaving over 54 million mobile app users vulnerable.
- Leaked API keys allow threat actors to perform a variety of unauthorized actions such as sending emails, deleting API keys, and modifying two-factor authentication.
What are API & API Keys
An API (Application Programming Interface) is a piece of software that allows applications to communicate with each other without any human intervention. An API key is a special identification used by users, developers, or calling programs to authenticate themselves to an API.
What is Mailgun and how can it be exploited?
Mailgun provides email API services enabling brands to send, validate, and receive emails through their domain at scale. An API key leak would allow a threat actor to:
- Send Emails
- Read Emails
- Get SMTP Credentials
- Get IP Address
- Get Statistics
- Allow creating, accessing, and deleting Webhooks
- Retrieve mailing lists of customers and launch a phishing campaign
- List members in a mailing list and show all the subscribed or unsubscribed emails.

What is Mailchimp and how can it be exploited?
Mailchimp is a transactional email service first introduced in 2001 and later launched as a paid service with an additional freemium option in 2009. An API key leak would allow a threat actor to:
- Read Conversations
- Fetch Customer Information
- Expose email lists of multiple campaigns containing PII
- Authorize 3rd party applications connected to a MailChimp account
- Manipulate Promo Codes
- Start a fake campaign and send emails on behalf of the company

What is SendGrid and how can it be exploited?
SendGrid is a communication platform intended for transactional and marketing emails. They provide cloud-based services to assist businesses with shipping notifications, friend requests, sign-up confirmations, email newsletters, etc. An API key leak would allow a threat actor to:
- Send emails
- Create API Keys
- Control IP addresses used to access accounts.

Conclusion
In modern software architecture, APIs integrate new application components into existing architecture. So its security has become imperative. Software developers must avoid embedding API keys into their applications and should follow secure coding and deployment practices like:
- Standardize Review Procedures
- Rotate Keys
- Hide Keys
- Use Vault
Responsible Disclosure
CloudSEK has notified the involved entities and the affected apps about the hardcoded API keys.
About CloudSEK
CloudSEK is a contextual AI company that predicts Cyber Threats.
At CloudSEK, we combine the power of Cyber Intelligence, Brand Monitoring, Attack Surface Monitoring, Infrastructure Monitoring and Supply chain to give context to our customers’ digital risks.
To learn more about CloudSEK, visit https://cloudsek.com/.
Media Contact:
Shashank Shekhar
+91-9811379924





