Cyber Media
Our team of Contributors are independent experts from the fields of academia, research & development, military, government, and other similar fields, designed to bring unbiased and insightful perspectives to the forefront of cybersecurity discussions.
We understand the importance of fostering a diverse range of opinions and insights in the rapidly evolving landscape of cybersecurity. As such, our program exclusively features experts who operate independently of commercial affiliations, ensuring an objective and impartial viewpoint.
By participating in our Independent Expert Guest Writer Program, cybersecurity professionals, academics, and thought leaders have the opportunity to contribute to a platform dedicated to fostering open dialogue and advancing the collective understanding of cybersecurity issues.
Most Recent Articles
From The Archives

LinkedIn DMs are not a Business Continuity Plan

Tool Sprawl a Silent Sabotage?

Enough with the Optics: It is Time for Cyber Accountability, Not Publicity Stunts

Why Does Recovery Take So Long? But It Doesn’t Have To
Qantas Breached and Customers are Fuming

What Happens When the World’s Biggest Vulnerability Database Goes Dark?

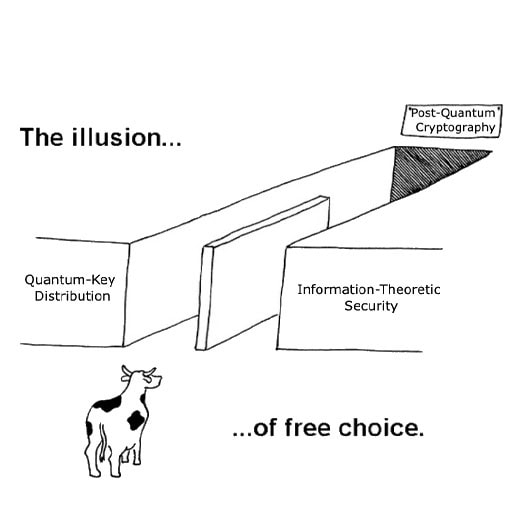
The Cybersecurity Paradox: Mastering a Game That Has Already Changed

The Top Cyber Movies that Shaped our View for Better or for Worse?
Meet Our Contributors & Editors
What We Do
KBI.Media is The Voice of Cyber.
We broadcast some of the most important and informative cyber content from some of the largest organisations, governments, and promising start-ups from around the world.
We're also responsible for creating a lot of it..

Become a Contributor
Unbiased Expertise: Our guest writers are carefully selected based on their expertise and independence from commercial interests. This ensures that the content they contribute is free from any potential bias, providing our audience with a well-rounded and objective understanding of cybersecurity topics.
Diverse Perspectives: We believe in showcasing a variety of perspectives to enrich the discourse surrounding cybersecurity. By featuring independent experts with diverse backgrounds, experiences, and viewpoints, we aim to present a comprehensive and inclusive narrative that reflects the complexity of the cybersecurity landscape.
Rigorous Selection Process: To maintain the integrity of our program, we employ a rigorous selection process for guest writers. Prospective contributors undergo thorough vetting to ensure their independence and commitment to delivering high-quality, unbiased content.
Cutting-Edge Insights: Our guest writers are at the forefront of cybersecurity developments, providing our audience with timely and relevant insights. Their independence allows them to delve into emerging trends, technological advancements, and policy changes without the constraints of commercial interests.
Commitment to Transparency: We prioritize transparency in our program, clearly outlining the independence criteria for our guest writers. This commitment ensures that our audience can trust the authenticity and objectivity of the content presented.