The Internet of Medical Things (IoMT) is transforming healthcare with its rapidly expanding ecosystem of interconnected devices. As this technology advances, its impact extends beyond traditional clinics and hospitals, projecting the IoT in healthcare market to reach $312.7 billion by 2030, growing at a CAGR of 15% from 2024 to 2030. However, with increased digitalization and a shift away from traditional network boundaries, securing these devices has become a complex challenge.
Understanding IoT and Zero Trust in Healthcare
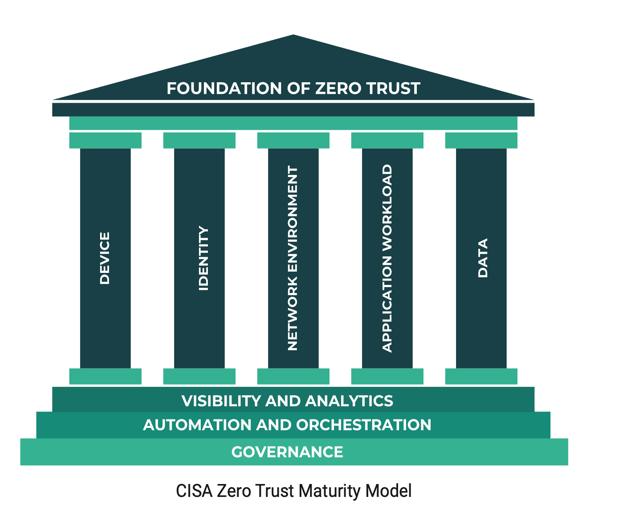
According to the Cybersecurity and Infrastructure Security Agency (CISA), Zero Trust is a security model designed to minimize risks by enforcing strict access controls and continuously validating trust. Zero Trust shifts from a location-centric model to a data-centric approach, focusing on fine-grained security controls that adapt as users, systems, and data evolve. The Zero Trust Maturity Model comprises five pillars and three foundational steps that guide organizations in developing, implementing, and refining their security policies.
In healthcare, IoT devices like sensors and connected medical equipment collect and share critical data to enhance patient care and streamline operations. The COVID-19 pandemic has accelerated digital transformation, highlighting the need for robust security measures to protect these interconnected devices. Traditional perimeter defenses are insufficient for today’s distributed, cloud-based environments. Zero Trust offers a crucial framework by operating on the principle that no device, user, or network can be inherently trusted, enforcing granular policies and continuous evaluations to safeguard systems.
Risks in IoMT
IoMT devices play essential roles in remote patient monitoring, asset tracking, and smart hospital solutions. Despite their benefits, they face considerable security risks and challenges. Many IoMT devices lack built-in security features, making them susceptible to attacks. Key issues include vulnerabilities, data privacy concerns, malware and ransomware threats, interoperability challenges, and outdated systems. For instance, a study of infusion pumps revealed that 75% had known vulnerabilities, posing serious risks such as patient safety threats, data breaches, and compliance issues. The FDA has even issued recalls due to security concerns. The long lifespan of many medical devices further complicates security enhancements.
Key Steps to Implement Zero Trust for IoMT Devices
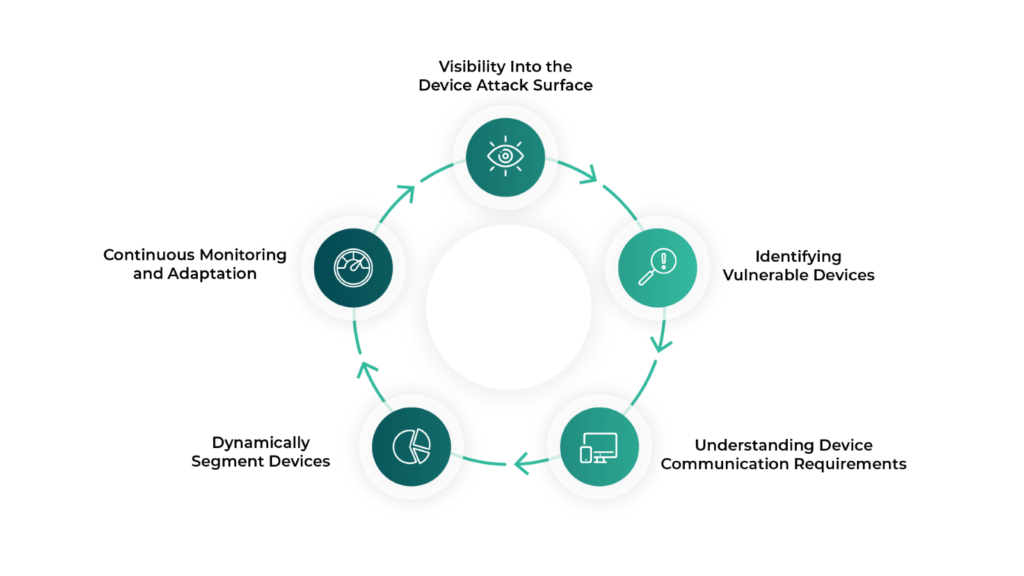
Zero Trust for IoMT: Key Steps
To build a robust Zero Trust framework for IoMT devices, organizations must implement a comprehensive strategy that covers visibility, risk assessment, communication requirements, dynamic segmentation, and continuous monitoring. Let’s explore each of these components in detail:
1. Visibility Into the Device Attack Surface
Before implementing Zero Trust policies, it’s crucial to first understand what devices are in your environment, including their capabilities and purposes. This can be particularly challenging with the wide array of IoMT devices, such as infusion pumps, patient monitors, etc. These devices vary greatly in function and risk, yet organizations often only identify them by their IP addresses within a broad subnet.
To effectively manage these devices, organizations need robust methods for discovering, classifying, and inventorying all assets, both managed and unmanaged. This process should provide detailed information about each device, including its type, make, capabilities, location, applications/ports, and behaviors. Given the large number of unmanaged devices and their frequent movement, automating discovery and classification is essential for maintaining an accurate and up-to-date device inventory.
2. Identifying Vulnerable Devices
After establishing a clear view of the device landscape, organizations need to evaluate the risk associated with each device. This assessment involves identifying devices that have known vulnerabilities, lack essential security software, or utilize weak passwords or certificates. It’s also important to monitor for signs of compromise, such as unusual behavior or connections to suspicious domains. With this information, you can plan corrective actions to address any weaknesses. Additionally, these insights are valuable for developing risk-based policies within a Zero Trust framework, helping to ensure that your security measures are aligned with the actual risks your devices face. Devices deemed high-risk can be dynamically restricted from accessing sensitive assets or interacting with potentially dangerous domains.
3. Understanding Device Communication Requirements
For a successful Zero Trust implementation, it’s essential to grasp the specific communication needs of each IoMT device. IoMT devices often use specialized protocols that may not be supported by standard security tools. While laptops might require broad internet access, IoMT devices typically have limited needs, such as connecting to a cloud backup or receiving updates from a vendor’s site. Organizations should establish a detailed baseline for each IoMT device’s network behavior, including its necessary interactions and the protocols it uses. This baseline helps ensure that communications are legitimate and not directed toward malicious sources. By defining precise policies based on this baseline, security teams can restrict devices to only the essential interactions needed for their operation.
4. Dynamically Segment Devices
In a Zero Trust framework, it’s crucial to apply risk and security insights effectively. Policies must be dynamically enforced using the latest available information, ensuring that only necessary communications are permitted while all other traffic is blocked. This approach can be enhanced through microsegmentation. Unlike traditional network segmentation, which groups similar devices based on their location or function, microsegmentation creates policies tailored to each device’s specific needs. This means that instead of allowing unrestricted lateral movement within a segment, each device is only permitted to communicate with essential services, blocking all other traffic regardless of its network location. Policies should adapt based on the device’s risk profile, with stricter controls applied to critical devices or those exhibiting signs of vulnerability or unusual behavior.
5. Continuous Monitoring and Adaptation
In a Zero Trust model, it’s essential to recognize that security is an ongoing and dynamic process. Security contexts evolve constantly, and trust granted to a device or session at one time may not hold in the future. Environments with IoMT devices might frequently change—new devices are introduced, and existing devices shift locations. Consequently, risk and threat levels can fluctuate daily. Organizations must be equipped to identify new devices, detect behavioral changes, and spot any signs of compromise.
Why ColorTokens Xshield™?
ColorTokens provides a comprehensive solution that guides organizations through this transition with minimal disruption. Their platform is designed to help healthcare entities progress through the Zero Trust Maturity Model’s five pillars and three foundational steps, ensuring a tailored approach that evolves with their specific needs and challenges.
ColorTokens Xshield™ offers a robust solution for protecting Internet of Medical Things (IoMT) devices, which are increasingly critical to healthcare operations. By employing advanced microsegmentation, Xshield™ ensures that network traffic and device interactions are meticulously controlled, permitting only authorized communications. This level of granular control is essential for maintaining the security of sensitive healthcare environments. Xshield’s real-time monitoring and analytics provide deep visibility into device behavior, facilitating swift threat detection and response. This capability is crucial for healthcare organizations striving to maintain digital resilience and preparedness against breaches.
How Does ColorTokens Achieve CISA Zero Trust Maturity Model?
ColorTokens Xshield™ aligns with the CISA Zero Trust Maturity Model by delivering comprehensive visibility, automation, and governance across your network. It scans and classifies all assets, enabling precise visibility and modelling of your environment. Xshield™ uses machine learning and heuristics automation to recommend the access policies which are defined by your business processes, thus policies can be implemented quickly to block malicious lateral data movement by both external and internal threats, without spending days or weeks on policy inference. It provides real-time policy analysis through a unified interface, supporting both network and user access governance. With microsegmentation, Xshield™ reduces the attack surface, controls traffic flow, and prevents lateral movement. It integrates seamlessly with LDAP/SAML for contextual identity management, enforces least privilege access to workloads, and secures critical assets with AES-GCM encryption, ensuring robust protection and compliance.
By offering advanced microsegmentation, real-time monitoring, and seamless integration with existing systems, Xshield™ ensures meticulous control over network traffic and device interactions. This not only protects sensitive data but also enhances resilience against breaches. For healthcare organizations striving to maintain the highest standards of digital security and preparedness, adopting ColorTokens Xshield™ means embracing a future-proof solution that fortifies your network against the ever-growing array of cyber threats, ensuring continuous protection and operational integrity.
Want to learn more about how major healthcare organizations are securing IoMT devices? Let’s have a chat.





