Introduction
In 2023, the Latitude Financial cyberattack exposed over 14 million customer records, including driver licences, passport numbers, and financial details. While remediation focused on containment and response, one quiet question lingered for many defenders:
“Why didn’t we ask, ‘what if?’ sooner?”
That single moment underscores the critical role of ethical curiosity-a mindset that’s often missing from our frameworks, dashboards, and compliance checklists. While we invest heavily in tools, standards, and automation, true cyber resilience demands something human: the courage to question, explore, and challenge the status quo.
What Is Ethical Curiosity?
Ethical curiosity is the mindset that motivates individuals to:
- Investigate how systems work, not just how they fail.
- Ask “what if?” and “why?” in the face of routines and assumptions.
- Pursue knowledge responsibly, always weighing the impact on users and society.
Unlike compliance-driven approaches, ethical curiosity is proactive and creative. It’s about seeking to understand the unknown, not just ticking boxes or following policies.
Why Ethical Curiosity Matters in Modern Security Programs
- Adversaries Are Already Curious
Cyber attackers thrive on curiosity. Whether they’re lone actors, ransomware groups, or state-backed operations, they are constantly probing, experimenting, and repurposing old exploits in new ways.
If defenders don’t mirror this exploratory instinct, they risk reacting from behind-always one breach too late.
Fact: According to MITRE, over 30% of the techniques added to the ATT&CK framework each year involve lateral movement and privilege escalation pathways that evolved from basic configuration oversights-not zero-days.
- Curiosity Unlocks Innovation
Some of the most powerful ideas in cybersecurity-zero-trust architecture, bug bounty programs, anomaly detection-began with simple, persistent questioning.
It was someone asking:
- “Why do we give implicit trust to this device?”
- “What if we opened our systems up to ethical hackers?”
- “Why is this user behaving differently today?”
Encouraging security practitioners to think beyond checklists and compliance can lead to game-changing insights that static frameworks often miss.
- It Builds Safer Teams
Security teams often operate under pressure: burnout, breach anxiety, and tight deadlines. By fostering ethical curiosity, organisations create safer, more empowered environments. People feel encouraged to surface their questions and observations-without fear of blame or ridicule.
This has a compounding effect: when developers, analysts, and engineers feel psychologically safe, they speak up earlier, collaborate more freely, and solve problems creatively.
From Culture to Practice: Nurturing Ethical Curiosity in Your Organisation Here are four ways leaders can embed ethical curiosity into their security programs: 1. Create Exploration Zones
Not every security learning opportunity needs to come from a breach. Structured experimentation-like internal “hack days,” capture-the-flag (CTF) challenges, or security gamification-gives teams space to explore unfamiliar paths safely.
Example: A New Zealand-based SaaS firm holds monthly “Break & Learn” sessions where employees are encouraged to gently probe mock systems for vulnerabilities. These sessions have led to real-world fixes, all from simulated curiosity.
- Reward the Question, Not Just the Outcome
Celebrate employees who challenge assumptions, even if their inquiry doesn’t reveal a vulnerability. The value is in the questioning mindset, not just the discovery.
- Set up “curiosity shoutouts” during retros or town halls.
- Recognise cross-functional teams that uncover blind spots during internal reviews. • Encourage leaders to model curiosity by asking open-ended “what if” questions.
- Enable Responsible Exploration
Clear guidelines are essential to ensure ethical boundaries are respected. Establish:
- A safe disclosure policy internally for reporting flaws or misconfigurations. • A documented ethical hacking charter that outlines scope, tools, and rules of engagement. • Well-maintained staging environments for exploratory testing without production risk.
By formalising the “how” of safe exploration, you remove ambiguity and foster trust. 4. Debrief the “Why” Behind Security Events
Too often, post-incident analysis focuses only on what failed-not why someone found the issue in the first place.
Ask:
- What sparked the discovery?
- What question or observation triggered the investigation?
- Could this mindset be encouraged in others?
These insights are powerful training inputs that go beyond root-cause and help grow strategic thinking.
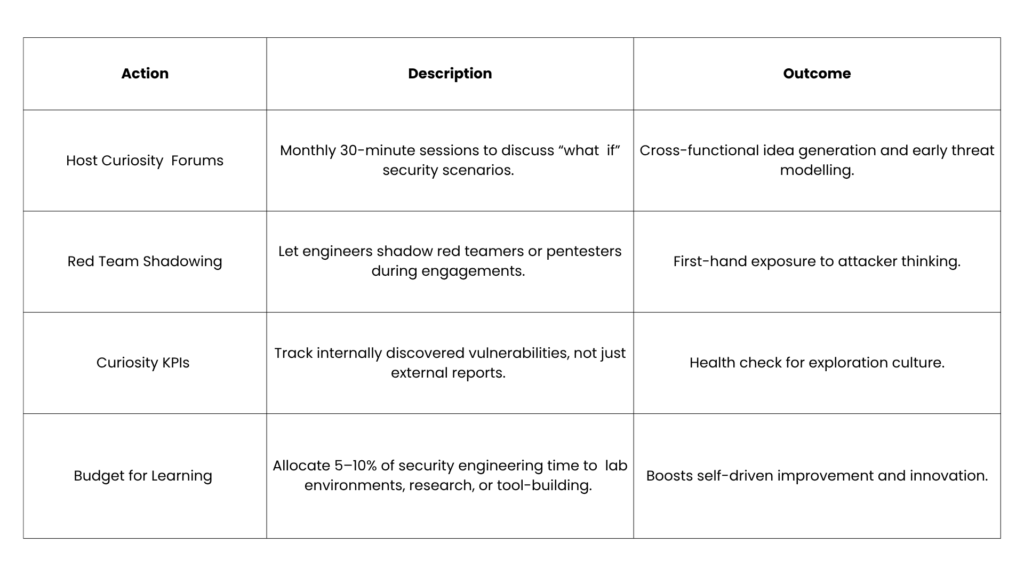
Practical Steps You Can Take This Quarter
Final Thoughts: Curiosity Is a Defence Strategy
We often look to policies, tech, and frameworks as our first line of defence. But attackers aren’t bound by frameworks-they are driven by questions.
So should we be.
By cultivating ethical curiosity across teams-from developers and engineers to product managers and executives-we build not only better defences, but more agile, adaptive organisations.
In an age where threats move fast and blind spots evolve daily; curiosity may be our most underused asset in cyber defence.
About the author: Ankita Dhakar is the founder of Capture The Bug, a Penetration Testing-as-a-Service platform helping ANZ enterprises discover and fix security issues through continuous, ethical hacking programs.