The Landscape
American Water, the largest water and wastewater utility in the United States, plays a crucial role in ensuring the availability of safe and reliable drinking water for millions of residents. Recently, the company encountered a significant challenge when a cyberattack disrupted its customer portal and billing services. This incident raised concerns about the vulnerability of essential utilities to digital threats, emphasizing the importance of cybersecurity in protecting critical infrastructure.

Overview of the Incident
The cyberattack disrupted American Water’s online customer portal, MyWater, temporarily suspending billing operations and limiting call center availability.

Note on American Water website
The company serves over 14 million people across 24 states and has filed an 8-K Breach Notice with the U.S. Securities and Exchange Commission on October 3. According to reports, the company first detected ‘unauthorized activity within its computer networks and systems’ on October 3.
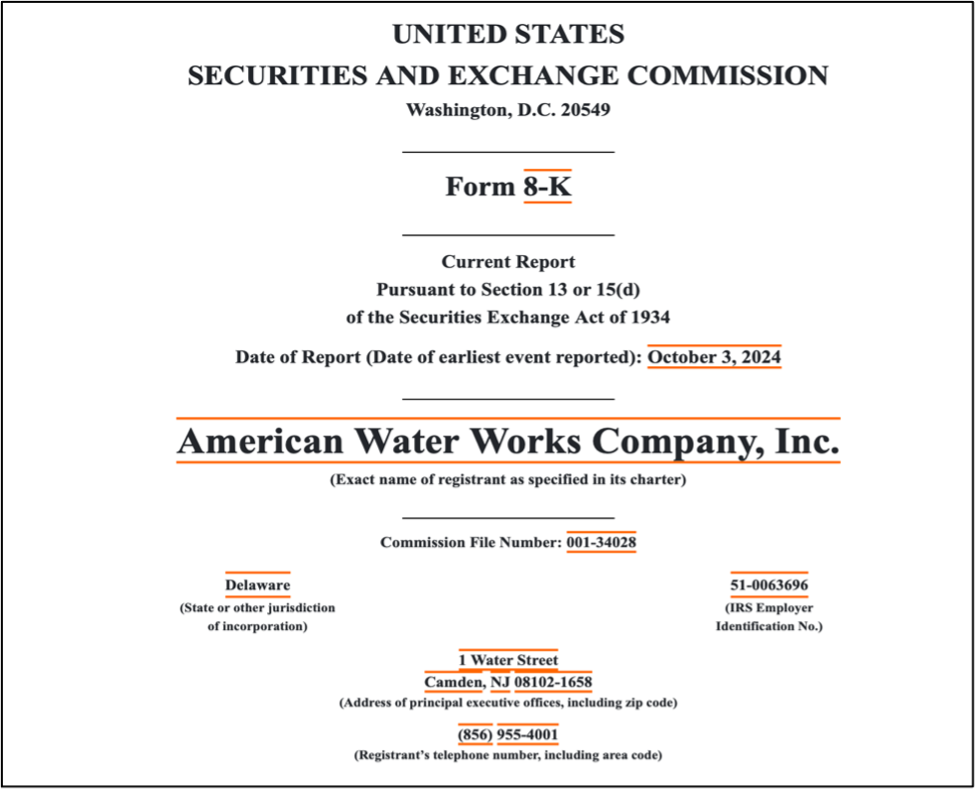
8-K Breach Report filed by American Water Works
Response from American Water: In an FAQ on its website, American Water announced a temporary halt to billing, assuring customers that no late fees would be applied, and call center services will operate at limited capacity. “To safeguard our customers’ data and prevent any further environmental impact, we have taken the precaution of disconnecting or deactivating specific systems,” the FAQ explained. “We proactively took MyWater offline, which means billing is paused until further notice. Rest assured, we are working tirelessly to restore these systems safely and securely.”
Speculation and Broader Implications: While the company has not disclosed the specifics of the attack, cybersecurity analysts quickly speculated that it was likely a ransomware incident. To date, no ransomware group has claimed responsibility for the attack on American Water. The company believes that none of its water or wastewater facilities have been adversely affected. However, it acknowledges that the full extent of the incident’s impact remains uncertain.
American Water serves 1,700 communities primarily in the Central and Eastern U.S., along with California and Hawaii. This incident underscores the broader implications for the utility sector, highlighting the urgent need for enhanced security measures to safeguard public resources against evolving cyber threats. As the industry continues to digitalize, the importance of robust cybersecurity strategies is paramount.
If the water systems remained unaffected by the cyberattack, American Water may have successfully implemented a crucial cybersecurity best practice: segregating operational technology (OT), Internet of Things (IoT) devices, and industrial control systems (ICS) from the IT network. This can be achieved through segmentation and other strategies. This approach enhances security by isolating sensitive operational technology from traditional information technology, minimizing the risk of a widespread impact during a cyber incident.
The Rising Cyberattacks on Water Systems
The U.S. water system faces significant challenges, including aging infrastructure, rising demand, and increasing cyber threats. As cyberattacks from state actors like Russia, China, and Iran escalate, the vulnerabilities of these systems become increasingly evident. Their reliance on digital technologies makes them particularly susceptible to intrusions, raising the risk of service disruptions, public health crises, and economic repercussions.
In September 2023, Arkansas City, Kansas, switched to manual operations at its water treatment facility to manual operations after discovering a cyber incident. CISA reported ongoing exploitation of internet-accessible OT and ICS, emphasizing that exposed systems could be compromised through default credentials or brute force attacks.
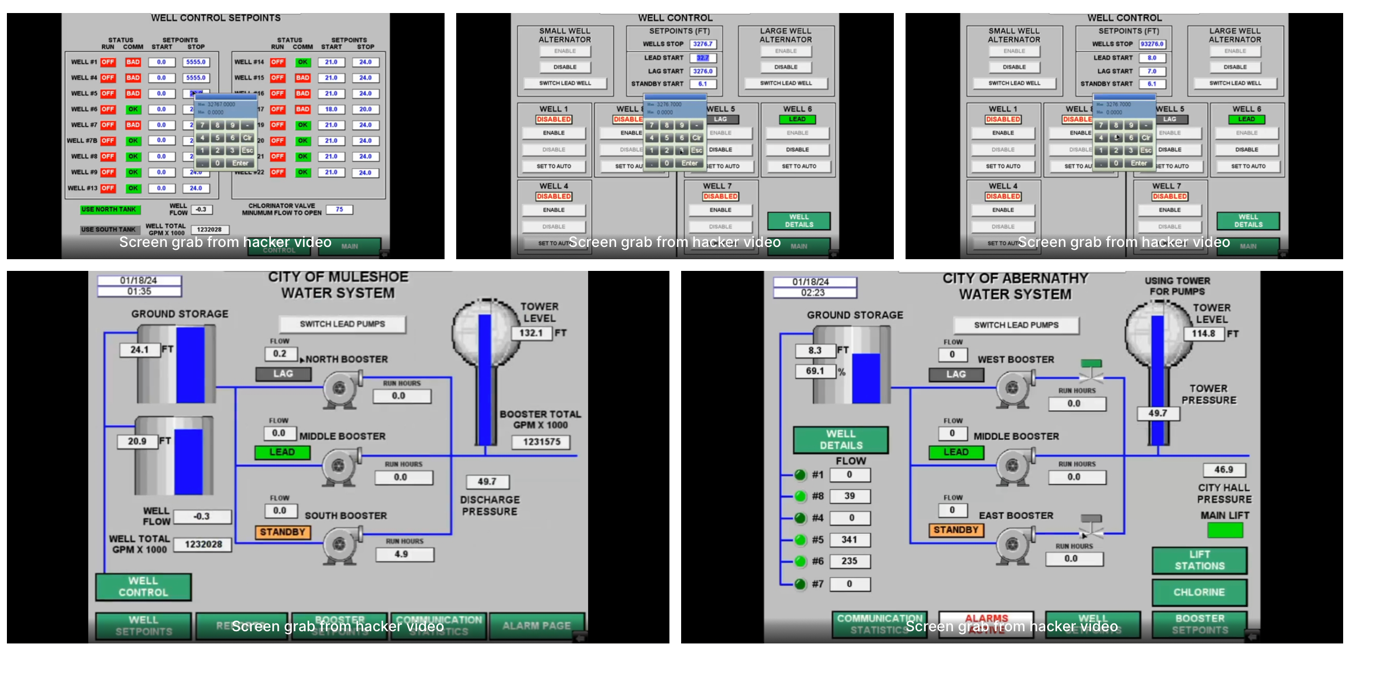
In January 2024, multiple Texas water and wastewater plants, including those in Hale Center, Muleshoe, Lockney, and Abernathy, were attacked, exposing vulnerabilities in their supervisory control and data acquisition (SCADA) systems. Hackers released videos showing them manipulating controls remotely. In Muleshoe, this resulted in a water tank overflow lasting for approximately 30 to 45 minutes. A common factor in these incidents was vendor software that kept systems remotely accessible.
Additionally, the Chinese cyber-espionage group Volt Typhoon infiltrated critical infrastructure, including water systems, remaining undetected for years. CISA also warned of the Iran-linked Cyber Av3ngers, which compromised programmable logic controllers (PLCs) essential for water treatment processes.
To combat these vulnerabilities, the U.S. Environmental Protection Agency (EPA) has issued guidance to water operators on improving cybersecurity. This follows calls from the White House for enhanced state support. Critical infrastructure entities are advised to adopt best practices, including changing default credentials, patching vulnerabilities, and segmenting systems, as robust cybersecurity measures for water utilities are essential.
Microsegmentation helps isolate critical assets from the broader network, effectively limiting potential attack surfaces. By creating secure zones, this approach ensures that even if one segment is compromised, others remain protected. This is particularly important for segregating operational technology (OT), Internet of Things (IoT) devices, and industrial control systems (ICS) from IT networks. This segregation enhances security by containing threats and preventing their spread to critical systems.
Safeguarding our critical infrastructure is not just a technical necessity; it is a vital commitment to public health and safety. Contact us to fortify your defenses and ensure that your critical resources remain resilient against the tides of uncertainty. Together, let us pave the way for a safer, more secure future.





