Imagine a scenario where a ransomware attack cripples a hospital’s ventilators, infusion pumps are manipulated to deliver incorrect dosages, or a CT scanner is hijacked to serve as a launchpad for a larger network breach. These are not hypothetical situations; they are real threats that healthcare organizations face today. As medical devices become increasingly interconnected, they also become prime targets for cybercriminals. The combination of outdated software, insecure communication protocols, and an expanding attack surface makes them highly vulnerable to sophisticated attacks.
The growing interconnectivity of medical devices has introduced new security challenges, making them prime targets for cyberattacks. Infusion pumps, MRI machines, and ventilators, which were once isolated systems, now operate within hospital networks, exposing them to potential exploitation. Threat actors capitalize on weaknesses in legacy software, misconfigured networks, and unprotected communication channels to disrupt healthcare operations, compromise patient safety, and exfiltrate sensitive medical data.
Example of Scenarios on How Hackers Can Exploit Medical Devices
Ransomware in Critical Care Environments
A threat actor gains initial access to a hospital’s network by delivering a phishing email containing a malicious payload, which exploits unpatched vulnerabilities in endpoint systems. Once inside, the attacker employs credential dumping techniques to escalate privileges and move laterally using tools such as Mimikatz or BloodHound. The attacker then targets network-connected medical devices, deploying ransomware that encrypts essential systems such as ventilators and patient monitors. Advanced ransomware variants employ fileless malware techniques, executing malicious code in memory to evade traditional, signature-based detection mechanisms. With critical infrastructure locked down, hospitals face a difficult choice: pay the ransom or endure significant delays in patient care.
Remote Manipulation of Infusion Pumps
Infusion pumps rely on wireless communication to receive dosage instructions from centralized hospital management systems. Attackers exploit weak authentication mechanisms, default credentials, or unencrypted communication protocols (such as Telnet or HTTP) to intercept and manipulate data. Through man-in-the-middle (MITM) attacks, a hacker can modify the dosage being delivered to a patient, either increasing or decreasing medication levels. This kind of attack is particularly dangerous when targeting high-risk drugs such as insulin or pain management opioids, where even small deviations can result in life-threatening complications. Without TLS encryption and proper certificate validation, these attacks can go undetected, allowing malicious actors to persist in the environment.
Exploiting MRI Machines as Attack Vectors
Many MRI and CT scanners run on outdated Windows-based operating systems, making them susceptible to well-documented exploits such as EternalBlue (MS17-010). Once an attacker gains access to an MRI system, they can leverage lateral movement techniques, such as Pass-the-Hash or Kerberos ticket theft, to escalate privileges and establish persistence. From this foothold, attackers can deploy command and control (C2) beacons, exfiltrating sensitive patient imaging data or deploying additional malware payloads. Additionally, adversaries can weaponize compromised MRI machines by modifying scan settings or triggering device malfunctions, leading to incorrect diagnoses and delayed treatments.
Denial-of-Service Attacks on Smart Ventilators
Smart ventilators rely on proprietary communication protocols for remote monitoring and automated adjustments. Attackers exploit vulnerabilities in these protocols to launch denial-of-service (DoS) or distributed denial-of-service (DDoS) attacks, overwhelming devices with rogue commands or excessive traffic. These attacks can force ventilators into failure states, rendering them unresponsive to legitimate clinical inputs. More advanced threat actors can execute firmware corruption attacks, injecting malicious code into a ventilator’s operating system, effectively “bricking” the device. In environments where multiple ventilators rely on a shared network segment, a single compromised device can introduce cascading failures, leading to systemic patient risk.
The Real-World Consequences of Medical Device Attacks
The implications of cyberattacks on medical devices extend far beyond technical disruptions; they pose significant risks to patient safety and hospital operations. If a ransomware attack encrypts life-critical systems, doctors and nurses may be left without access to essential monitoring devices, delaying urgent treatment and potentially resulting in loss of life. A manipulated infusion pump could deliver a lethal overdose or an inadequate dose, leading to medical complications or fatalities. Similarly, a denial-of-service attack on smart ventilators could prevent patients from receiving oxygen at the right levels, exacerbating critical conditions.
Beyond patient harm, hospitals face operational and financial burdens. An attack on a hospital’s imaging systems or connected medical devices can lead to forced shutdowns, delaying critical procedures and surgeries. The financial ramifications of such attacks are also severe, with ransom demands, regulatory fines, and the cost of incident response further straining already tight healthcare budgets. As cybercriminals continue to evolve their tactics, healthcare organizations must prioritize the security of medical devices to ensure uninterrupted patient care and safeguard institutional integrity.
Mitigating Cyber Threats Against Medical Devices
In an era where medical devices are increasingly interconnected, adopting a Zero Trust framework is crucial for ensuring their security against evolving cyber threats. The Zero Trust Maturity Model, as outlined by CISA, comprises five fundamental pillars: Identity, Devices, Networks, Applications, and Data—along with three foundational capabilities that ensure continuous visibility and monitoring, governance, and security enforcement across all layers of an organization’s infrastructure. This structured approach ensures that security is enforced at every layer of the network.
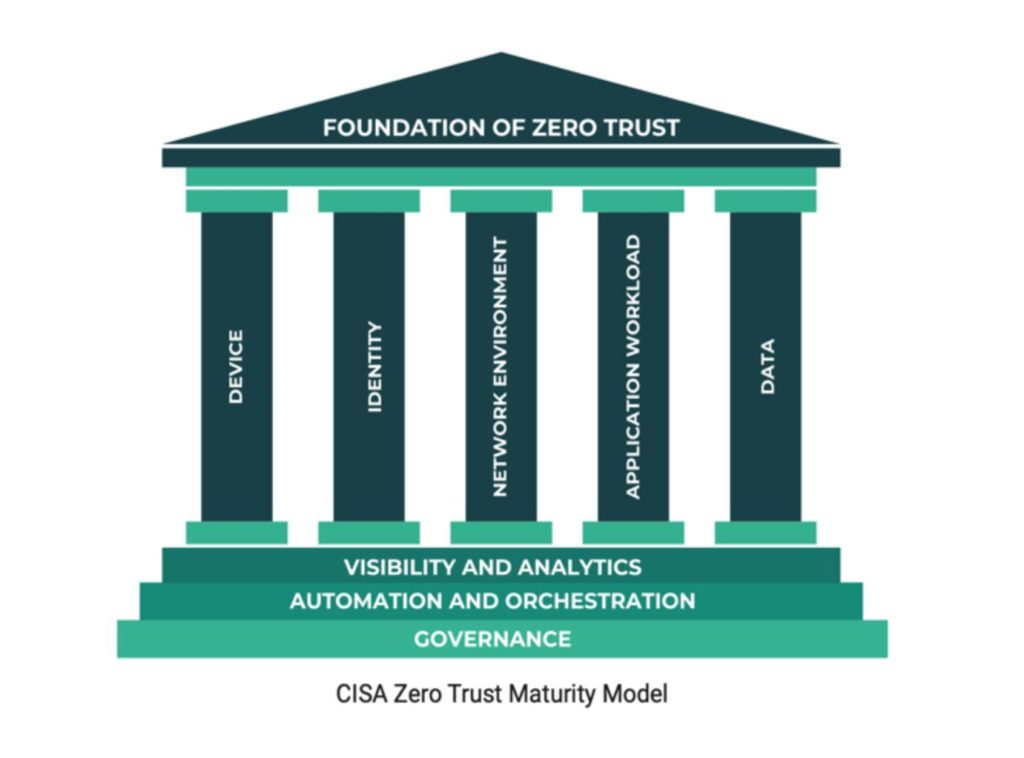
Out of all the mitigation strategies under Zero Trust, we would like to highlight three key approaches that are particularly critical for securing medical devices:
Firmware and patch management remain fundamental security measures for protecting medical devices against evolving cyber threats. Regular updates help mitigate vulnerabilities and safeguard devices from known exploits. However, one of the most pressing challenges is securing medical devices through firmware and patch management. Unlike traditional IT systems, patching medical devices is not always straightforward due to regulatory constraints and operational risks. Large healthcare institutions manage thousands of devices, making widespread patch deployment impractical. As a result, organizations must turn to virtual patching via intrusion prevention systems (IPS) to shield unpatched devices from exploitation. Integrity monitoring solutions can detect unauthorized firmware modifications, while cryptographic code signing ensures that only manufacturer-approved updates are applied, preventing the risk of firmware tampering.
In cases where patching is not feasible, microsegmentation becomes the most critical line of defense. Implementing a Medical Device Isolation Architecture allows healthcare organizations to confine medical devices within dedicated network segments, reducing exposure to unauthorized access. By restricting lateral movement, attackers are prevented from using a single compromised device as an entry point to the broader network. Utilizing least privilege access principles and software-defined perimeters ensures that medical devices communicate only with trusted systems, further minimizing attack surfaces.
Even with strong segmentation and patching strategies in place, real-time threat intelligence and anomaly detection are essential to proactively identify and mitigate emerging cyber threats in medical devices. Threat intelligence leverages data from various sources, including known attack patterns, malware signatures, and adversary behaviors, to provide security teams with actionable insights. This allows organizations to anticipate potential breaches and implement preventive measures. Anomaly detection, powered by machine learning and behavioral analytics, continuously monitors device activity for deviations from established baselines. Given that medical devices often have predictable usage patterns, any irregularities, such as unexpected network communications, unauthorized access attempts, or sudden spikes in data transfer, can signal a potential compromise. By integrating threat intelligence with anomaly detection systems, healthcare organizations can establish a proactive security posture, ensuring that even sophisticated, previously unknown threats are quickly identified and mitigated before they disrupt patient care.
Conclusion
Medical devices represent a critical attack surface that cannot be ignored. Cyber adversaries continuously evolve their tactics, requiring healthcare organizations to adopt proactive, intelligence-driven security strategies.
By leveraging microsegmentation, Zero Trust frameworks, advanced threat detection, and robust firmware security, hospitals can build a resilient security posture that protects both patient safety and healthcare infrastructure. The future of medical device security depends on our ability to stay ahead of emerging threats.
The security of medical devices is not just an IT issue—it is a matter of saving lives.
If you want to know how microsegmentation and Zero Trust approaches keep the integrity of your medical devices, get in touch with one of our experts at colortokens.com/contact-us




