“The Cybersecurity and Infrastructure Security Agency (CISA) defines insider threat as the threat that an insider will use their authorized access, intentionally or unintentionally, to do harm to the department’s mission, resources, personnel, facilities, information, equipment, networks, or systems. Insider threats manifest in various ways: violence, espionage, sabotage, theft, and cyber acts.”
While the spotlight often shines on external threats such as ransomware, organized crime, and state-sponsored attacks, it is crucial not to overlook a more insidious danger lurking within: insider threats. These internal threats can be particularly devastating because they originate from individuals who have legitimate access to critical systems and sensitive data. The evolving nature of insider threats necessitates a nuanced approach—one that emphasizes not only detecting and mitigating these risks but also ensuring that unauthorized access is effectively prevented. This safeguards our most valuable assets and restricts any potential for lateral movement. Building digital resilience involves more than adopting a defensive posture; it requires a strategic approach to protect what truly matters and maintain robust security across the organization.
According to a 2024 survey by Cybersecurity Insiders, an overwhelming 90% of respondents stated that insider attacks are as difficult (53%) or more difficult (37%) to detect and prevent compared to external cyberattacks.
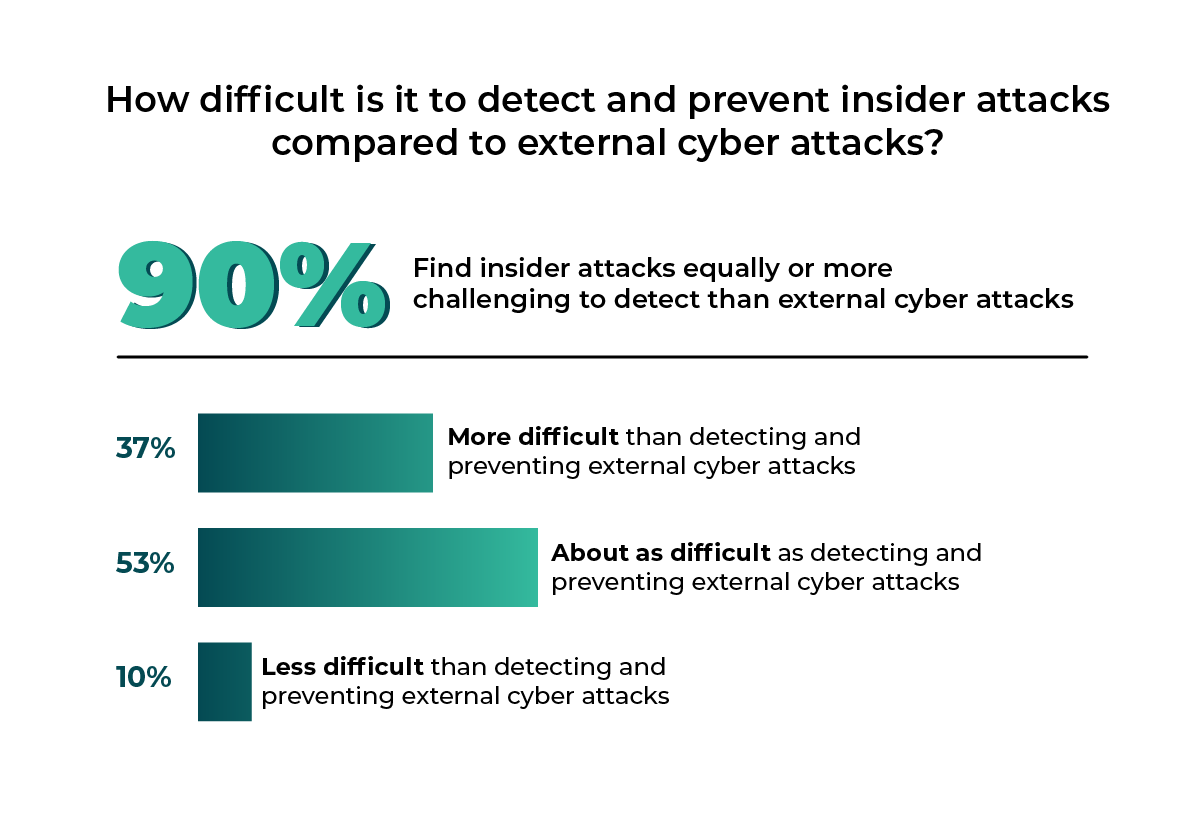 2024 Insider Threat Report by Cybersecurity Insiders
2024 Insider Threat Report by Cybersecurity Insiders
Classifying Insider Threats
Insider threats can be categorized into three primary types, each presenting unique risks and challenges to organizations. Understanding these categories aids in developing effective strategies to mitigate their impact.
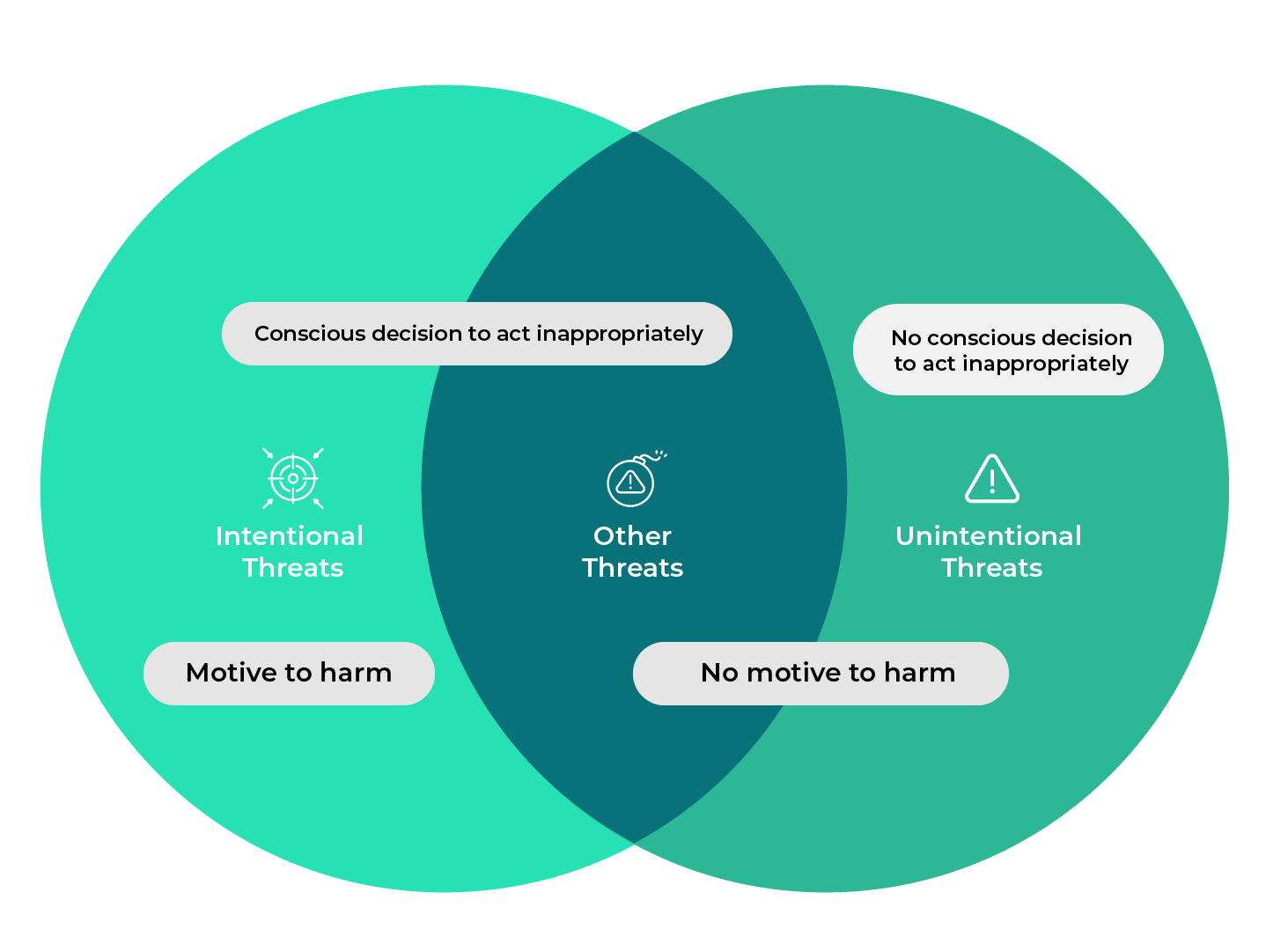
- Intentional Threats: Intentional threats, commonly known as “malicious insiders,” involve deliberate actions taken to harm an organization for personal gain or to address grievances. These insiders may act out of revenge for perceived slights, such as missed promotions or terminations. Their harmful activities may include:
- Privilege Escalation: Exploiting elevated permissions to access sensitive systems or data. This often involves taking advantage of vulnerabilities in the system or using unauthorized methods to gain higher levels of access.
- Data Exfiltration: This refers to the unauthorized transfer of data, often using advanced techniques like encryption or obfuscation to evade detection. Attackers may blend exfiltrated data with legitimate traffic to avoid being noticed.
- Sabotage: Deliberate damage to systems or data, including deploying malware to corrupt files, disrupt operations, or cause system outages.
- Unintentional Threats: Unintentional threats arise from carelessness rather than malicious intent and can be further divided into:
- Negligence: Actions taken out of carelessness, despite awareness of security policies. Examples include allowing unauthorized individuals to access secure areas, losing portable storage devices containing sensitive data, or ignoring critical update notifications.
- Improper Data Handling: Accidental exposure of sensitive information due to mishandling or misconfigurations.
- Phishing Vulnerabilities: Falling victim to phishing attacks, which can compromise credentials and lead to unauthorized access.
- Weak Security Practices: Using weak passwords, neglecting software updates, or failing to follow basic security protocols.
- Accidental: Mistakes that unintentionally create security risks, such as sending sensitive documents to the wrong email address, clicking on malicious links, or improperly disposing of confidential files.
- Other Threats: These threats encompass various forms that extend beyond the previous classifications, yet they remain significant:
- Collusive Threats: These occur when insiders collaborate with external actors to compromise an organization. This can involve recruiting insiders to facilitate fraud, theft, or espionage.
- Third-Party Threats: Contractors or vendors, while not formal employees, may have access to organizational systems or networks, posing direct or indirect threats.
- Moles: Outsiders who deceitfully gain insider access by posing as employees or partners, further increasing the risk.
Examples of these threats include:
- Credential Theft: Techniques such as keylogging, phishing, or exploiting vulnerabilities to capture login details, which attackers then use to gain unauthorized access.
- Exploitation of Compromised Accounts: Using stolen credentials to navigate through the network, escalate privileges, and access additional systems, often leading to data exfiltration or operational disruption.
Notable Incidents Illustrating Insider Threats
In September 2023, MGM Resorts International fell victim to a social engineering attack orchestrated by the cyber threat group Scattered Spider. The attackers impersonated an employee using information from LinkedIn to gain access to the IT help desk, securing administrator privileges for MGM’s Okta and Azure environments. MGM hastily deactivated its Okta Sync servers and other essential infrastructure components to prevent the escalation of the attack, causing interruptions to reservation systems, digital room keys, slot machines, and more. This led to ransomware attacks that disrupted operations, costing nearly $100 million.
In June 2023, Zellis, a third-party payroll provider serving the UK and Ireland, experienced a significant data breach due to a zero-day vulnerability in its subcontractor’s file transfer software, MOVEit. Hackers exploited this vulnerability, accessing Zellis’s systems and leaking sensitive customer data, including information from high-profile clients like British Airways and the BBC. This incident not only caused reputational damage but also raised potential legal repercussions. The attack highlighted how third parties can pose substantial risks as internal threats; inadequate security measures by subcontractors can result in significant vulnerabilities for organizations. Zellis had no choice but to disconnect the affected server and engage external security teams for forensic analysis.
In April 2023, Jack Teixeira, a member of the Massachusetts Air National Guard, was arrested for leaking classified U.S. military documents on Discord. Holding a Top-Secret security clearance, he shared sensitive intelligence with friends, jeopardizing national security and straining international relations, thereby highlighting the dangers posed by privileged insiders.
Common Indicators of Insider Threats
- Anomalous Behavior Patterns
- Unusual Access Times: Accessing systems or data outside of normal working hours or on weekends can be a red flag. This behavior deviates from an employee’s typical schedule and may indicate suspicious activity.
- Abnormal Data Transfers: Large volumes of data transferred, particularly to external or unauthorized locations, may indicate that someone is exfiltrating information. Monitor for unusual spikes in data movement or patterns that do not align with the user’s role.
- Access to Unusual Files: If an employee starts accessing files or systems outside their typical job functions, it could be a sign of malicious intent. For example, a finance employee suddenly accessing sensitive engineering documents might warrant further investigation.
- Suspicious Network Traffic
- Unexpected Outbound Traffic: High volumes of data being sent outside the organization, especially to unknown or suspicious IP addresses, can signal a potential data breach. Network monitoring tools can help identify such anomalies.
- Unusual Communication Patterns: Communication with known malicious IP addresses or domains, or unusual patterns of network traffic, may indicate that an insider is being manipulated or is trying to communicate with an external threat actor.
- Encrypted Traffic: While encryption is a standard security measure, abnormal volumes or frequencies of encrypted traffic—especially if leaving the organization—could mask illicit activities.
- Unauthorized Access to Systems
- Unjustified Privilege Escalation: Instances where users gain elevated access rights without proper justification can indicate potential insider threats. Monitoring user permissions regularly helps ensure that access levels align with job roles and responsibilities.
- Accessing Sensitive Data Unnecessarily: When employees access confidential information that is outside their scope of work, it raises red flags. Regular audits of access logs can help identify such suspicious activities early.
- Failed Login Attempts: A series of failed login attempts by a user may suggest an insider attempting to access unauthorized systems or data. Implementing alerts for unusual login activity can provide timely warnings of potential breaches.
- Unauthorized Changes to Systems
- System Configuration Changes: Unapproved modifications to system settings, configurations, or security parameters can be indicative of an insider attempting to disable security measures or gain unauthorized access.
- Unapproved Software Installations: Installing software or tools not sanctioned by IT poses a risk. For instance, an employee installing remote access tools or file-sharing applications may attempt to facilitate unauthorized data access.
- Alterations in Access Permissions: Changes to user permissions or access levels that are not documented or authorized can indicate that someone is trying to escalate their privileges or access sensitive information.
- Unusual Employee Behavior
- Changes in Attitude or Performance: A sudden shift in an employee’s attitude or performance, such as becoming unusually secretive, disengaged, or stressed, might suggest that they are hiding something or are under external pressure.
- Changes in Attitude or Performance: A sudden shift in an employee’s attitude or performance, such as becoming unusually secretive, disengaged, or stressed, might suggest that they are hiding something or are under external pressure.
- Physical Security Issues
- Unauthorized Access to Restricted Areas: An insider who is found in areas they do not have authorization to access could be gathering sensitive information or conducting unauthorized activities.
- Lost or Stolen Devices: Devices containing sensitive information that are lost or stolen pose a significant risk. An insider’s carelessness or malicious intent may lead to such incidents, making it crucial to monitor and secure physical assets.
Case Study: Avis Cyberattack
Avis, a leading car rental company, recently disclosed a significant cyberattack that affected approximately 300,000 customers. The breach, identified in early August 2024, compromised sensitive personal information, including names, mailing addresses, email addresses, phone numbers, dates of birth, credit card numbers and expiration dates, and driver’s license numbers, as stated in a data breach notice filed with Iowa’s attorney general. The digital break-in occurred between August 3 and August 6, according to the car rental giant in filings with the Maine and California attorneys general. According to data breach notification letters sent to impacted customers and filed with California’s Office of the Attorney General, the company took action to stop the unauthorized access, launched an investigation with the help of external cybersecurity experts, and reported the incident to relevant authorities after learning of the breach on August 5.
Venky Raju, Field CTO at ColorTokens, commented on the breach: “Avis’ disclosure that the breach was due to insider wrongdoing, alongside their mention of a third party, suggests the perpetrator was either an employee of a business partner or someone whose system was compromised by a remote attacker. Regardless, once the attacker had access to the network, they were able to infiltrate critical business applications and exfiltrate customers’ personal information. This highlights the risks associated with a flat enterprise network without proper compartmentalization.”
Venky Raju further emphasized, “To mitigate such risks, enterprises should adopt a zero-trust strategy and implement microsegmentation to isolate applications and prevent unauthorized access. Traditional tools such as endpoint detection and response and intrusion detection systems are useful but often react too late to prevent attacks like the one experienced by Avis.”
Insider Threat Prevention Strategies for a Secure Organization
To effectively mitigate insider threats, organizations must adopt a comprehensive, multi-faceted approach that encompasses several key strategies:
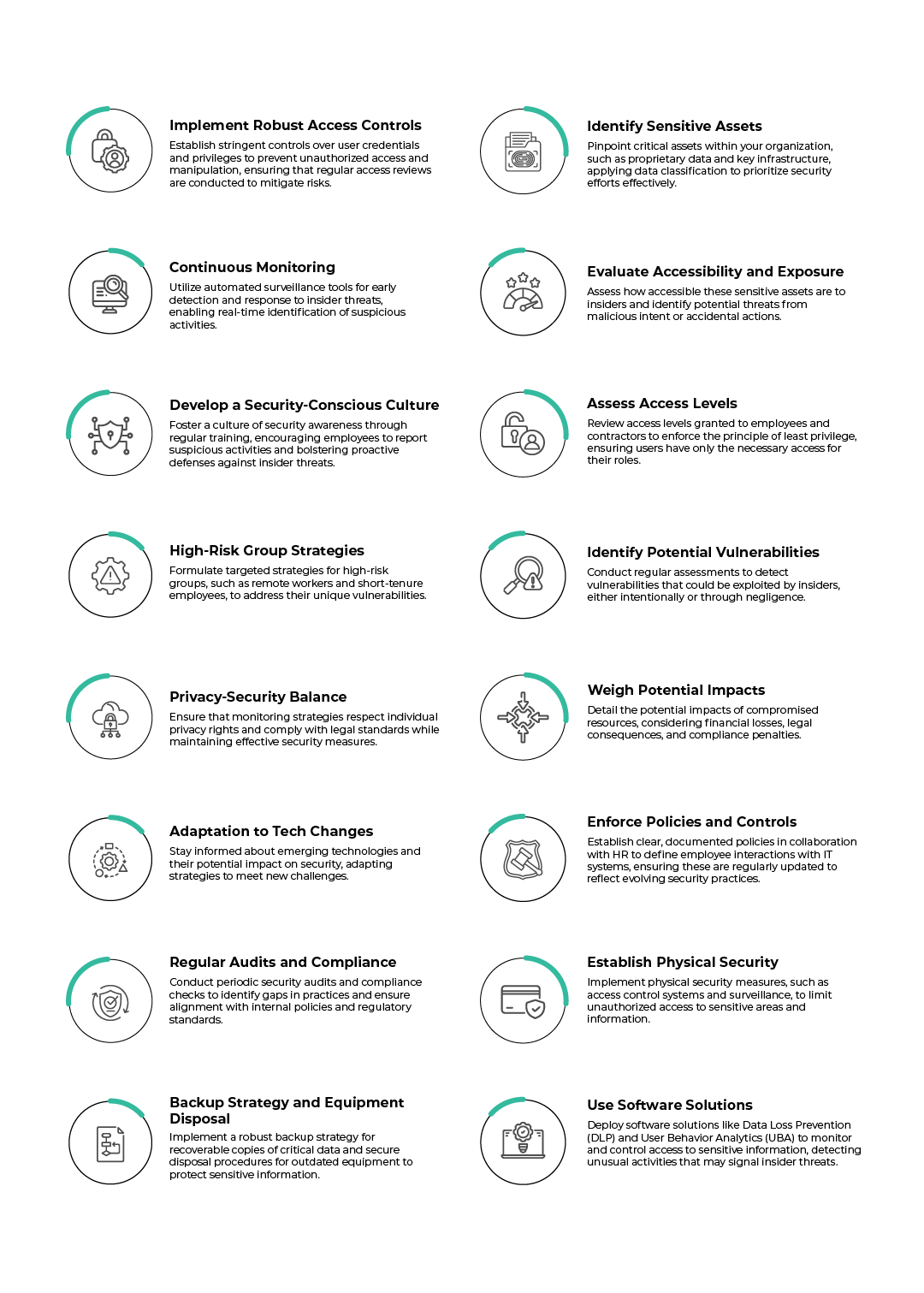
How Microsegmentation Can Keep Insider Threats at Bay?
To effectively safeguard against insider threats, implementing comprehensive security measures is essential. This includes protecting valuable assets, enforcing clear policies, and enhancing visibility into user activities.
For instance, during the Avis attack, the use of microsegmentation using granular policies could have restricted unauthorized access to customer data, thereby mitigating the breach’s impact.
Microsegmentation is crucial because it limits the attack surface, ensuring that sensitive data and critical systems are confined within defined boundaries. For instance, organizations can ring-fence systems hosting sensitive applications and data, allowing administrative and management access only from approved bastion servers or Privileged Access Management (PAM) systems.
Unlike traditional tools such as endpoint detection and response and intrusion detection systems—which are reactive and typically engaged only after an attack has occurred—microsegmentation proactively reduces risk by containing potential breaches before they escalate. By restricting application access to authorized systems and isolating systems accessed by third-party entities, organizations can ensure that unauthorized access is confined to smaller, manageable areas.
Additionally, granular segmentation enables the precise identification and protection of sensitive assets, ensuring that only authorized personnel can access critical information, thereby reinforcing the principle of least privilege. Ultimately, this strategy enhances an organization’s capability to enforce security policies and improve monitoring, providing a robust defense against insider threats. By applying comprehensive security policies to each network segment, organizations can enforce strict controls, minimizing the likelihood of both accidental and intentional breaches.
In conclusion, while insider threats may be the sneaky, unwanted house guests of the cyber world, a solid strategy like microsegmentation ensures they do not overstay their welcome.
Contact us today for a free consultation and learn how you can mitigate insider threats with advanced strategies like microsegmentation.



