SYDNEY – 29 November 2024 – As industrial networks expand into wireless domains, new vulnerabilities are exposing critical infrastructure to potential cyber threats. With this evolution, safeguarding wireless devices within industrial settings has become essential. Since the launch of Guardian Air, Nozomi Networks has emphasised the need for stronger protections, particularly on wireless fronts.
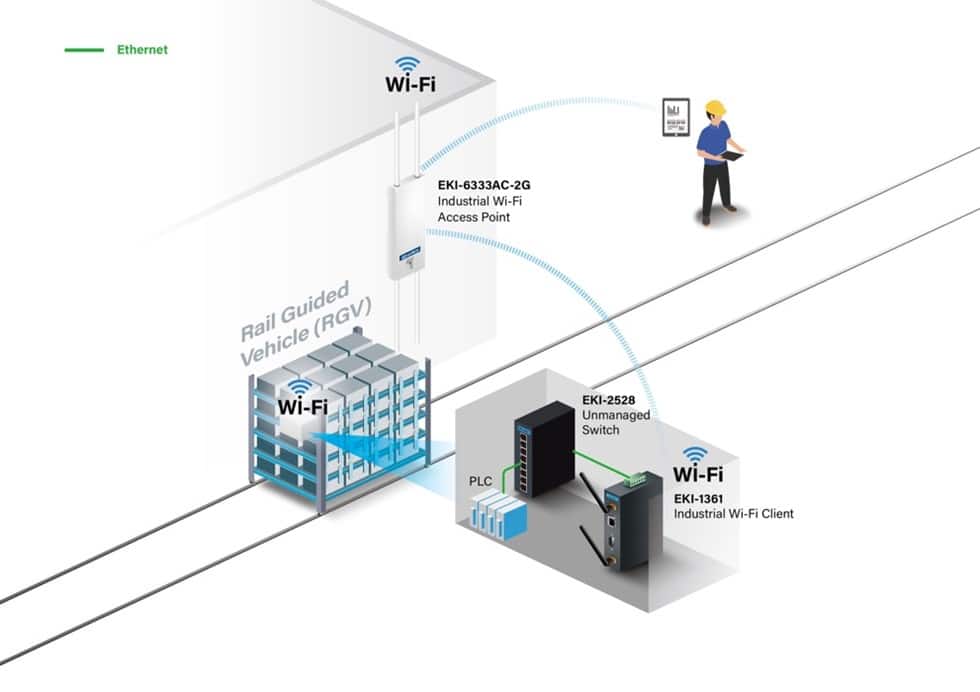
Recognising this, Nozomi Networks Labs has conducted an analysis of version 1.6.2 of the EKI-6333AC-2G industrial-grade wireless access point. Thanks to its resilience in challenging environments, this device is utilised across diverse sectors, ranging from automobile assembly lines up to warehousing and distribution operations within logistics. Our analysis identified 20 vulnerabilities, each assigned a unique CVE identifier. These vulnerabilities pose significant risks, allowing unauthenticated remote code execution with root privileges, thereby fully compromising the confidentiality, integrity, and availability of the affected devices.
Following the triage and confirmation of these issues, Advantech has released firmware version 1.6.5 to address the vulnerabilities on EKI-6333AC-2G and EKI-6333AC-2GD and firmware version 1.2.2 for EKI-6333AC-1GPO. Through the responsible disclosure process coordinated with Advantech, the EKI-6333AC-2GD and EKI-6333AC-1GPO devices were also confirmed to be impacted by these vulnerabilities due to shared firmware code.
Research Scope
The EKI-6333AC-2G by Advantech is an industrial-grade wireless access point designed for challenging environments, providing stable, dual-band Wi-Fi connectivity. It is particularly suited for mission-critical applications within industrial settings, like manufacturing, energy, and public infrastructure, where durability and secure connections are essential.
What Are the Impacts of These Vulnerabilities?
Several of these vulnerabilities have been evaluated as critical, given that they could ultimately lead to remote code execution (RCE) with root privileges over the access point. This would allow a threat actor to compromise the device’s confidentiality, integrity, and availability. Two possible attack vectors were identified:
- Attack Vector 1 (LAN/WAN): In situations where an attacker can interact directly with the access point over the network, they can exploit these vulnerabilities by crafting malicious requests that target the vulnerable service.
- Attack Vector 2 (Over-the-Air): An additional scenario occurs over the air, where an attacker does not need to be connected to a wired (LAN/WAN) or wireless (WLAN) network. They could exploit the wireless spectrum to execute code on the device simply by being in physical proximity to it.
Given these severity levels, a malicious user could achieve the following outcomes:
- Persistent access to internal resources: Once code execution on the device is achieved, malicious users may implant a backdoor to maintain persistent access. This setup could enable scenarios where initial access is gained through malware infection (such as via email), and persistence is established by compromising the Advantech device.
- Denial of Service (DoS): In scenarios where a vulnerable access point serves as the backbone network to control wireless RGVs navigating complex production layouts—the ability to tamper with these critical access points could significantly disrupt automation processes on production lines.
- Lateral movement: Gaining root privileges on the device enables the attacker to repurpose the access point as a fully functional Linux workstation, providing a new foothold for further exploration and penetration within the network. This can be accomplished, for instance, by conducting man-in-the-middle (MITM) attacks to capture credentials transmitted over unencrypted protocols or by exploiting known vulnerabilities in unpatched devices using publicly available exploits.
Vulnerability Spotlight
We chose to highlight an over-the-air attack scenario leading to arbitrary code execution by chaining two specific vulnerabilities, rather than focusing on discovered command injections classified as critical. This scenario, in our opinion, is more interesting since it involves the wireless spectrum as possible attack vector and provides a different perspective on how attackers might choose to target manufacturing facilities typically considered ‘safer’ due to higher isolation.
The attack combines a ‘CWE-79 – Improper Neutralisation of Input During Web Page Generation (Cross-Site Scripting)’ (CVE-2024-50376), which can be leveraged by an attacker without even being connected to a corporate network, with a ‘CWE-78 – Improper Neutralisation of Special Elements Used in an OS Command’ (CVE-2024-50359), which would typically require authentication if exploited independently.
Before describing how the attack can be performed, it is important to briefly detail how a wireless access point works. In simple terms, a Wi-Fi access point acts as a bridge between the wireless spectrum and a wired network. The access point periodically sends clear text messages over the air called ‘beacon frames’. These frames announce the presence of the network, communicate essential details such as the network name (SSID) and the signal power, and guide end-user devices like laptops and smartphones in discovering and maintaining already established connections.
All devices supporting wireless connectivity are therefore equipped with dedicated hardware and software to implement a logic that allows them to receive, parse and interpret beacon frames and all the other types of frames involved in a Wi-Fi communication (a similar logic can also be applied for Bluetooth communications). If a vulnerability is found in any of these processes – such as in the case of the Advantech access point – this weakness could compromise the security of the device itself. Furthermore, such a vulnerability could have cascading effects, potentially leading to an immediate and broader security impact on the rest of the network, as the compromised device might act as an entry point for attackers.
With this brief explanation we can now better understand how CVE-2024-50376 and CVE-2024-50376 can be exploited. To begin, a malicious user must be in physical proximity to the Advantech access point, at a distance that is sufficient for an attacker to broadcast information from a Rogue Wireless Access Point. With this term we refer to a fake access point that is fully controlled by the attacker and is separate from the Advantech one. Leveraging the rogue access point, the attacker can broadcast arbitrary ‘beacon frames’ that are received and captured from surrounding devices with wireless capabilities.
To make sure that the rogue wireless frames are visible to the Advantech device, attackers can either place themselves close to the access point or leverage dedicated antennas to propagate the rogue signal across longer distances. In both cases, it is important to understand that threat actors remained external and were never connected to the company network that was exposed via Advantech’s access point.
Supposing that the physical proximity requirement is met, we now have to meet a second requirement: an administrator-level user visiting the ‘Wi-Fi Analyse’ section of the Advantech web application.
This step could be obtained by either inducing a victim through phishing and social engineering attempts or by simply waiting for an administrator to visit the vulnerable web page as may happen during regular maintenance activity.
When visiting the ‘Wi-Fi Analyser’ section, the web application automatically embeds information received through beacon frames without proper sanitisation against special characters. One such piece of information an attacker could broadcast through its rogue access point is the SSID (commonly referred to as the ‘Wi-Fi network name’). The attacker could therefore insert a JavaScript payload as SSID for its rogue access point and exploit CVE-2024-50376 to trigger a Cross-Site Scripting (XSS) vulnerability inside the web application. This means that an external attacker can inject arbitrary JavaScript code in the victim’s browser and therefore perform arbitrary operations as if it was connected directly to the user session.
Having reached this stage, the attacker may inject a complete JavaScript-based C&C inside the victim’s browser to perform arbitrary operations leveraging for example readily available tools such as the Browser Exploitation Framework (BeEF). Although the Wi-Fi standard limits to 32 characters the length of SSIDs it was proved to be possible to circumvent this limitation, but we have chosen to omit further details.
While the attacker would already be able to control the device’s settings via its web interface, they could take it a step further by chaining CVE-2024-50359. This vulnerability involves an authenticated command injection that can be activated through the administrative panel, allowing for deeper system manipulation. Since the process responsible for executing the web application runs with root privileges on the Advantech device, no particular restrictions are encountered in the execution of arbitrary commands injected over the device at operating system level. One such command could be to allow to a persistent connection back to an internet-facing C&C machine to be established through a reverse shell. This would enable attackers to gain remote control over the compromised device, execute commands, and further infiltrate the network, extracting data or deploying additional malicious scripts.
Remediations
After these vulnerabilities were reported, Advantech promptly addressed them by releasing the following firmware versions:
- EKI-6333AC-2G: v1.6.5
- EKI-6333AC-2GD: v1.6.5
- EKI-6333AC-1GPO: v1.2.2
We encourage all asset owners to upgrade to this latest version to protect their network and devices from unauthorised access.